Freely Available British and Irish Public Legal Information
[Home] [Databases] [World Law] [Multidatabase Search] [Help] [Feedback]
England and Wales High Court (Patents Court) Decisions
You are here: BAILII >> Databases >> England and Wales High Court (Patents Court) Decisions >> Optis Cellular Technology LLC & Ors v Apple Retail Uk Ltd & Ors [2022] EWHC 561 (Pat) (15 March 2022)
URL: http://www.bailii.org/ew/cases/EWHC/Patents/2022/561.html
Cite as: [2022] EWHC 561 (Pat)
[New search] [Printable PDF version] [Help]
Neutral Citation Number: [2022] EWHC 561 (Pat)
Case No. HP-2019-000006
IN THE HIGH COURT OF JUSTICE
BUSINESS AND PROPERTY COURTS OF ENGLAND AND WALES
INTELLECTUAL PROPERTY LIST (ChD)
PATENTS COURT
Rolls Building
Fetter Lane
London, EC4A 1NL
15 March 2022
Before :
MR JUSTICE MEADE
- - - - - - - - - - - - - - - - - - - - -
Between :
|
|
(1) OPTIS CELLULAR TECHNOLOGY LLC (2) OPTIS WIRELESS TECHNOLOGY LLC (3) UNWIRED PLANET INTERNATIONAL LIMITED |
Claimants
|
|
|
- and - |
|
|
|
(1) APPLE RETAIL UK LIMITED (2) APPLE DISTRIBUTION INTERNATIONAL LIMITED (3) APPLE INC
|
Defendants
|
Thomas Hinchliffe QC, James Whyte and Jennifer Dixon (instructed by EIP Europe LLP) for the Claimants
Charlotte May QC, Lindsay Lane QC, Joe Delaney and Jeremy Heald (instructed by WilmerHale LLP) for the Defendants
Hearing dates: 18-21 and 26-27 January 2022
- - - - - - - - - - - - - - - - - - - - -
Covid-19 Protocol: This Judgment was handed down remotely by circulation to the parties’ representatives by email and release to BAILII. The date for hand-down is deemed to be 15 March 2022.
Mr Justice Meade:
Introduction. 4The common general knowledge. 10
Agreed common general knowledge. 12
Cellular network architecture. 12
Impairments in mobile systems. 17
Techniques for overcoming impairments. 18
Disputed common general knowledge. 30
LTE frequency and resource allocations. 31
Implicit Signalling of Resource Allocation - Kobe agreement 32
Claims of the Patent in issue. 37
Teaching of the specification in more detail 44
Issues of claim interpretation. 46
“Code multiplexing structure”. 47
CCE associated with a … PUCCH.. 49
Validity over the prior art 57
Legal principles - obviousness. 57
Obviousness over Panasonic. 59
Pozzoli question 4 - claim 1 of 549. 60
Does Table 1 disclose using three spreading codes for data?. 60
Multiplexing ACK/NACK and CQI. 63
Section 2 - Utilisation of CDM resources of ACK/NACK resource. 68
Section 3 - Configuration of implicit ACK/NACK resources. 69
Section 4 - Proposed signalling scheme. 69
Sections 5 and 6 - Benefits and Summary. 71
Does Nokia disclose using three Walsh codes for data?. 74
Steps from Nokia to the Patents. 75
3 codes for data and 2-cyclic-shift gap. 75
Using an MRB and unused cyclic shifts. 76
Apple’s alternative case over Nokia. 77
Claim 8 of 549 and claim 2 of 810. 79
Introduction
1. This is “Trial D” in these proceedings, the last of the “technical” trials. Earlier judgments give the procedural context.
2. There are two closely related patents in issue at this trial, namely EP (UK) 2 187 549 B1 (“549”), and EP (UK) 2 690 810 B1 (“810”). I will refer to them collectively as “the Patents”.
3. The Patents are from the same family. By agreement I only need to look at the specification of 549 since such differences as there are in the specification of 810 are immaterial, and references in this judgment to specification paragraph numbers are to 549. The priority date, no longer in dispute, is 13 August 2007.
4. The Patents come from a portfolio owned by Panasonic and were later acquired by Optis. As it so happens, one of the pieces of prior art is from Panasonic, but nothing turns on that.
5. The Patents, the relevant claims of which are product claims covering “mobile stations” (i.e. mobile phones), are declared essential to LTE. Essentiality is disputed. The dispute arises because the functionality in question, while capable of being supported by Apple mobile phones, is not used in the UK.
6. Validity is attacked over two pieces of prior art called Panasonic and Nokia. Panasonic is cited for obviousness. The main attack over Nokia is also obviousness. Apple has a secondary case over Nokia, run as a squeeze against infringement, which was pleaded as obviousness but as it turned out was also an anticipation attack against 549. This did not change the substance of what was said, though, so I gave Apple permission to amend its Grounds of Invalidity on the last day of trial.
7. Optis applies to amend both of the Patents and since these are unconditional amendments the Patents will be revoked if the amendments are refused. At the start of the trial amendment was opposed on the grounds of lack of clarity, added matter, and extension of protection, but extension of protection was dropped in Apple’s written closing (along with one of the added matter points).
Conduct of the trial
8. Apart from day 2 when the hearing was remote because of a positive COVID result among the legal representatives, the trial was conducted in Court. This meant that most of the oral evidence was given live, but Optis’ expert was cross-examined remotely on day 2. I do not think this caused any problem or any unfairness. Throughout the trial, a live feed was made available for the public should they ask, and also for clients or representatives who could not fit into Court owing to COVID restrictions. I am grateful to the third-party providers engaged by the parties to make the technology work.
9. Mr Hinchliffe QC, Mr Whyte and Ms Dixon appeared for Optis and Ms May QC, Ms Lane QC, Mr Delaney and Mr Heald for Apple.
The issues
10. The issues for me to decide are:
i) The nature of the skilled person, where there was a disagreement similar to that which I considered in Trial C, [2021] EWHC 3121 (Pat).
ii) The scope of the common general knowledge (“CGK”). Much was agreed but there were also areas of material disagreement.
iii) Claim construction, where two points arise, one relevant to validity and one to essentiality/infringement.
iv) Essentiality and hence infringement, arising from the fact that the functionality in question is optional and not used in the UK by any network. There is no dispute of fact and no debate over what the relevant LTE standards require.
v) Obviousness over TDoc R1-072799 “Panasonic”, in conjunction with CGK.
vi) Obviousness over TDoc R1-073006 “Nokia”, in conjunction with CGK.
vii) Anticipation over Nokia, which I have mentioned already and was a squeeze on infringement.
viii) An insufficiency squeeze against obviousness, which was barely developed at trial.
ix) Whether the amendments to the Patents ought to be refused for:
a) Lack of clarity;
b) Added matter.
11. I propose to deal with the issues in that order, but I should mention that the issues interrelate to an unusual degree and the parties dealt with the same subject matter under different headings from each other. For example, Apple dealt with the clarity objection to amendment largely under the heading of construction. I make no criticism of this, but it has, I fear, made the structure of this judgment untidy in places and led to some repetition on my part.
Terminology
12. In this field terminology can be confusing. For example, a mobile telephone may be called a mobile, a mobile phone, a UE or a mobile station depending on context, and base station, BTS, NodeB and eNodeB all refer to the same thing, again in varying contexts. One particular aspect of the relevant context is the generation being discussed, whether 2G, 3G or 4G. An additional difficulty is that patents use their own terminology.
13. In some patent cases the differences between e.g. a NodeB and an eNodeB may be important, but in the present case they are not.
14. For simplicity, I have aimed (I expect not completely successfully) to refer to “mobile” and “base station” or “the network” in my own text, but I have not generally tried to amend materials that I have referenced or quoted. I have sometimes referred to “UE”, “NodeB and “eNodeB” where the context is more specific to the standards, as is the case in relation to infringement and some aspects of validity.
15. There are also some less well-known technical concepts in this case that are referred by different names. I explain them below, but it is worth flagging at this stage that:
i) “Zadoff-Chu”, also known as “ZC” sequences are types of “CAZAC” sequences. For the purposes of this judgment there is no material difference.
ii) Likewise, “Walsh codes”, “Hadamard codes”, “block codes” and “blockwise spreading codes” can all be regarded as the same thing for practical purposes, with the first two being specific instances of the latter.
The witnesses
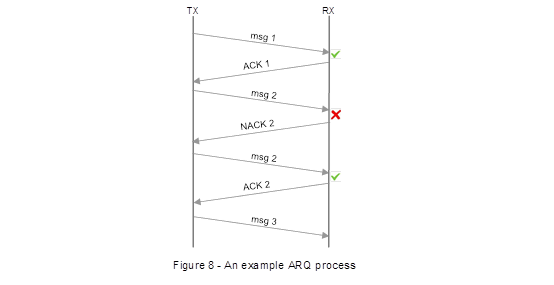
16. Each side called one expert witness.
17. There was fact evidence on behalf of Apple from Mr Francis Rowsell who oversaw “drive” testing of UK LTE networks in relation to the infringement/essentiality issue. He was not cross-examined and his evidence went in unchallenged.
Optis’ expert, Mr Bradford
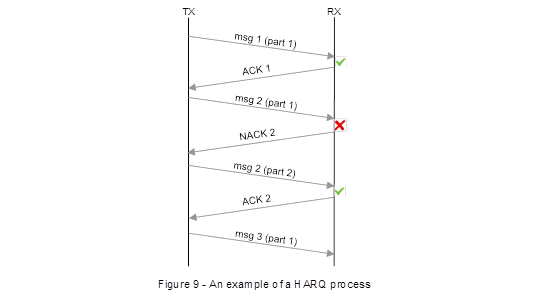
18. Optis’ expert was Mr Daniel Bradford.
19. Mr Bradford has a degree in electronic engineering with business management from the University of York, which he obtained in 2002. He worked in industry thereafter, becoming directly involved in mobile communications from 2007 (just after the priority date), although he said he kept abreast of mobile technology and standards before that. He worked on physical layer WCDMA for a femtocell application from 2007, and then on other physical layer issues for a microwave backhaul project. He has been an independent consultant since 2012 and has worked on projects which included physical layer aspects of eNodeBs.
20. Counsel for Apple submitted that Mr Bradford lacked experience of ETSI and of RAN1, at least compared to Apple’s expert. He accepted that he did not attend standards meetings, or even work in a supporting role in a company that did. However, as to the content of those meetings, he explained that around the priority date he acquainted himself with the versions of the standards then current, over a reasonably wide field, because his purpose was to be informed when he went for job interviews, and he did not know for whom he might end up working. Over time, I think he has picked up quite a good understanding of how ETSI works, more than adequate to support his evidence in this case. I agree his actual contact with ETSI has been more limited than that of Mr Edwards, but in itself that is unimportant. So I do not think there is anything in this submission.
21. Counsel for Apple also submitted that Mr Bradford had a distorted view of what the test for CGK was, and approached obviousness on the fallacious basis that unless something was in the CGK it could not be obvious to do it. I do not think Mr Bradford did this. There was plenty of discussion during his oral evidence about what was CGK and whether particular steps were in accordance with CGK, but that is normal and does not justify Apple’s submission.
Apple’s expert, Mr Edwards
22. Apple called Mr Keith Edwards. He also has a degree from York, in electronic engineering. He obtained it in 1983. From 1998 he was involved in work on the physical layer of UMTS, participating in a number of 3GPP RAN1 and RAN4 meetings, though on the evidence he did little more than dip into RAN1 meetings. He later worked on OFDMA and at around the priority date (from 2006-2009) he was at Nortel, working on its wireless 4G standards strategy. He is now a consultant and an Associate Lecturer at the Open University.
23. While accepting that he was trying to assist the Court, Counsel for Optis made several criticisms of Mr Edwards.
24. The first was that Mr Edwards was actually more familiar with RF aspects of cellular systems (the province of RAN4) than with the aspects of the physical layer dealt with in RAN1, and insofar as he was involved with ETSI, it was more on RAN4. Counsel for Optis pointed to evidence that Mr Edwards had given in Koninklijke Philips NV v Asustek Computer Inc [2018] EWHC 1224 (Pat) (“Philips v Asustek”), where the technology was different and Mr Edwards put more stress on RAN4. I did not think there was anything in the point that Mr Edwards stressed a different field of expertise on that occasion; there is nothing wrong, in itself, in emphasising the aspects of work history more relevant to the matter in hand.
25. I did however think that, as Counsel for Optis also submitted, a number of aspects of Mr Edwards's written evidence showed some lack of familiarity and comfort with the physical layer, and I have taken this into account. In particular, I thought it showed when he was cross examined about the real-world implications of using a single resource block for ACK/NACKs and CQIs (what this is, is explained below).
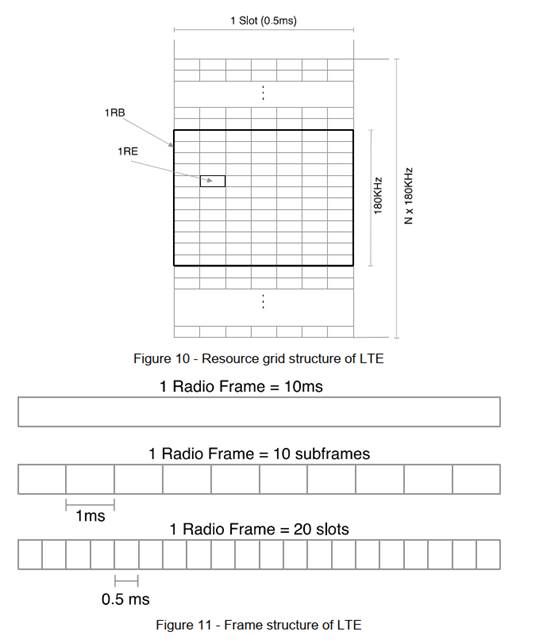
26. Counsel for Optis also pointed to evidence Mr Edwards gave in Philips v Asustek where Mr Edwards said that the skilled person would be aware of standards meetings, but would not know all the proposals discussed and would instead “routinely refer to the latest version of the relevant Technical Specification”. This would have meant, or strongly implied, that the CGK did not include Technical Reports or meeting minutes, both of which Apple argues in this case, with the support of Mr Edwards, would be CGK to a considerable extent. I agree that Mr Edwards’s position has been inconsistent on this potentially significant point. He suggested it was because the standard under discussion in Philips v Asustek was at a different stage of development than was LTE at the priority date in this case, but the facts did not support his explanation.
27. Next, Counsel for Optis drew attention to a number of areas where Mr Edwards had raised fresh points in oral evidence that were not in his written reports. This often happens for entirely proper and understandable reasons, of course, but in the present case I did think that some of the points Mr Edwards made were artificial and not well thought out.
28. Counsel for Optis pointed out that Mr Edwards had known of the Patents before he saw either Nokia or Panasonic. This was not his fault and happened because of the sequence of when prior art was cited and when the proposed claim amendments were formulated. Mr Edwards was clear that his task was to put the Patents out of his mind and I accept his evidence that he strove to do so.
29. Finally, Counsel for Optis submitted, based on statements on his company’s website (though not by him), that Mr Edwards is highly inventive. I suspect that he is, but as with the previous point, I am satisfied that he understood and sought to work with the concept of an uninventive notional skilled person.
30. Overall, these points lead me to approach with caution Mr Edwards’s evidence about what was CGK, and to apply a little scepticism about his evidence on the details of what to do with the cited prior art. But these are matters to put into the overall balance; they by no means cause me to discard his evidence.
The skilled person
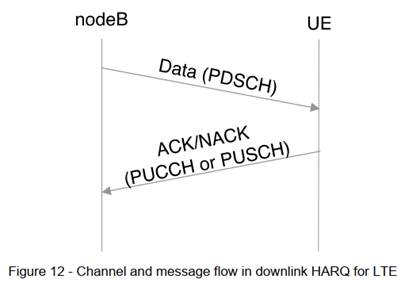
31. Optis said that the skilled person would be a person interested in the physical layer of a mobile communications system, but not necessarily LTE. Mr Bradford said in his oral evidence that the skilled person might not be working on LTE but on a proprietary system.
32. Through the evidence of Mr Edwards it appeared that Apple was positioning itself to go narrower and to contend that the skilled person would be engaged in work on, in particular, control signalling for the physical layer of LTE, a relatively narrow interest which would fall within the broad scope of RAN1 and which would, it seemed, help Apple when it came to the disputes over CGK. However, in its written opening and in particular oral submissions at the start of trial, Apple backed off this and said that the skilled person was a RAN1 person generally.
33. In Trial C I considered a very similar argument. I set out what I considered to be the applicable law at [29]-[31] by reference to my decision in Alcon v. Actavis [2021] EWHC 1026 (Pat), in which I drew heavily on the decision of Birss J, as he then was, in Illumina v. Latvia [2021] EWHC 57 (Pat).
34. Thus from [68] in Illumina Birss J provided the following approach:
“68. I conclude that in a case in which it is necessary to define the skilled person for the purposes of obviousness in a different way from the skilled person to whom the patent is addressed, the approach to take, bringing Schlumberger and Medimmune together, is:
i) To start by asking what problem does the invention aim to solve?
ii) That leads one in turn to consider what the established field which existed was, in which the problem in fact can be located.
iii) It is the notional person or team in that established field which is the relevant team making up the person skilled in the art.”
35. And in Alcon at [31] I said:
“31. I intend to apply that approach. I take particular note of:
i) The requirements not to be unfair to the patentee by allowing an artificially narrow definition, or unfair to the public (and the defendant) by going so broad as to “dilute” the CGK. Thus, as Counsel for Alcon accepted, there is an element of value judgment in the assessment.
ii) The fact that I must consider the real situation at the priority date, and in particular what teams existed.
iii) The need to look for an ‘established field’, which might be a research field or a field of manufacture.
iv) The starting point is the identification of the problem that the invention aims to solve.”
36. As in Trial C, the problem that the invention aims to solve is indeed within the general remit of RAN1.
37. Had Apple not backed off, and had I been called on to decide the point, I would have found that there was not any narrow, established field of control signalling in the LTE physical layer (just as the PDCCH was not an established field in Trial C). RAN1 was the relevant established field, and was broader.
38. On a related point, Apple relied on what e.g. I said in Alcon at [58], citing Horne Engineering v. Reliance Water Controls [2000] FSR 90, about being able to infer the nature of the skilled person from what the specification assumes about his or her abilities. Apple said that since the Patents assume that the skilled person has a detailed knowledge of LTE going beyond the draft standards and covering the latest development efforts, it can be taken that the skilled person would be someone with a familiarity with all relevant materials of that kind and hence the kind of RAN1 working discussion documents that Apple says were CGK. This seems circular and I reject it. In any event, it was not made out that the skilled person, in order to work the Patents, would need to know things about RAN1 discussions. I return to this point in relation to CGK.
39. Apple also pointed out that in Trial C Optis said that the skilled person was a RAN1 person but in this trial submits that he or she had still broader interests, with no necessary focus on LTE at all, such as proprietary systems, to which Mr Bradford referred in his evidence, and which I have mentioned above. It is reasonable to raise this inconsistency. While it might theoretically be justified by the fact that the claims of the Patents are not limited to LTE, I think Optis’ position is unrealistic given that no other context for use of the invention has been suggested and given the focus in the specification on LTE. Also, anyone working on a proprietary system would still regard RAN1 as a key reference source. So while acknowledging the theoretical possibility of proprietary systems, in practical terms I can and I think should treat the skilled person as a RAN1 person working on LTE. In closing oral submissions, Counsel for Optis essentially accepted this.
40. There is another issue, which relates to the depth of involvement that the skilled person, being a RAN1 person, would have with the standard-setting process. Counsel for Optis submits, based on what Arnold J, as he then was, said in Philips v. Asustek at [148]-[151], that the skilled person does not necessarily correspond to those most deeply involved, the actual delegates regularly attending all the meetings. There were also people who attended occasionally or provided support behind the scenes, and the skilled person could be from any of those categories. I accept this point, which did not arise in Trial C. It is significant because the CGK has to be tested accordingly. There was reference by both sides, though more so by Apple, I thought, to documents such as email traffic about meetings or proposals which would not have been readily available to all of the above categories of people. Such material might also not be regarded as a sufficiently good basis for further action, and I deal with that in relation to CGK, to which I turn next.
41. Apple suggested that there was no evidence that a “back office” RAN1 person would not have all the same knowledge as the actual delegates, and so I should treat all materials known to the latter as filtering back to the former. I think this is obviously unrealistic and I reject it.
The common general knowledge
42. There was no dispute as to the broad, applicable legal principles: to form part of the CGK, information must be generally known in the art, and regarded as a good basis for future action. It is not a requirement for CGK that the skilled person would have memorised it; CGK includes information that the skilled person would refer to as a matter of course. In relation to obviousness, the Court also may have regard to information which the skilled person would acquire as a matter of routine if working on the problem in question.
43. The parties submitted a document setting out the agreed matters of CGK (and identifying the areas whose CGK status was in dispute), which I have used as the basis for the corresponding section of this judgment. It included a lot of material that was either very basic indeed, or that went into detail that has turned out not to matter to the dispute at trial. So I have edited the document down quite a bit, but that is not because it was not useful to my understanding. There is still a great deal of material, I am afraid, and I feel that is symptomatic of an excessive level of detail that both sides inflicted on this case, which need not in the end be all that complicated. However, without covering the ground it will not be possible to explain the arguments made, or for the evidence to be understood if this matter goes on appeal. It should be noted that I have kept the Table and Figure numbers in the following section from the parties’ document to preserve the usefulness of any cross-references to them. Because I have deleted some of them, this means that the numbering does not run continuously and there are gaps; this is deliberate.
44. Given my finding that the skilled person would represent not only LTE delegates but also occasional attendees and persons providing support (and, in theory, to anyone working on a proprietary system), materials will not have been CGK if they were only available to a limited group within that broader scope.
Sources of CGK
45. I think that the textbook by Dahlman, “3G Evolution - HSPA and LTE for Mobile Broadband” (“Dahlman”) represented, broadly, many of the sorts of things that would be CGK, but I accept Optis’ argument that it was published too close to the priority date to be CGK in its own right. It was published in June 2007, and, based on what Mr Edwards said, I accept that it reflected matters as they stood about 6 months before that. The skilled person, if they saw it, would realise that it had been written while LTE was still in flux, and would expect that some of its contents were subject to further change.
46. The circulation of Dahlman was not clearly established. Mr Bradford did not see it pre-priority and it is not known if Mr Edwards did. Nevertheless, textbooks are the classic source of CGK. As one of the first textbooks to be available on LTE Dahlman can provide useful pointers about what information was CGK, but must be scrutinised in relation to any specific information. It cannot be accepted that anything in Dahlman was CGK. Apple made a rather weak attempt to qualify Dahlman as CGK by reference to the promotional “blurb” on its own back cover. That is obviously inadequate.
47. Optis made an argument which it relied on in a number of respects, most notably on mixed resource blocks (as to which, see below), that Apple’s position on Dahlman must mean that anything not in Dahlman was not CGK. This does not follow, particularly on mixed resource blocks, where the materials in RAN1 relied on by Apple date from the period after the 6 months pre-publication of Dahlman but before the priority date.
48. The parties agreed that the current LTE specifications as approved by RAN1 would be a source of, and indeed would be, CGK. There was a dispute about whether draft specifications would be CGK and therefore as to which precise version would be CGK at any point. The draft that was said (by Apple) to matter on the facts of this case was version 1.2.1 of TS 36.211. It was never uploaded to the 3GPP website and was in circulation only by email; indeed the version which was then-current, v.1.2.0, which is referred to in the CGK section below, was uploaded, after v.1.2.1 first went into circulation. V.1.2.1 contained numerous track-changed amendments. Counsel for Apple argued that the 3GPP rapporteur, Mr Parkvall, was very reliable and it would have been expected that the draft changes he made would properly track the upshot of the most recent RAN1 meeting. I do not accept that this would lead readers to think that v.1.2.1 was really solid. So for these reasons v.1.2.1 was not CGK.
49. Tracking the dispute over the identity of the skilled person that I have dealt with above, Apple said that minutes of meetings that took place in RAN1 were also sources of CGK. I reject this argument in its broadest form (that everything in the meeting minutes was CGK) in the light of my decision about the skilled person. It is unconvincing that all this provisional material would be CGK. The minutes were also really very brief and to treat them as conveying reliable technical information would be unsound.
50. I do not rule out that a significant, firm decision at a RAN1 meeting could be CGK - the Kobe agreement may be an example, which I address in detail below and which I conclude was CGK.
51. It was agreed that individual TDocs were not CGK. However, both sides referred to TDocs for a slightly different purpose, which was to show how RAN1 members in fact viewed earlier documents, such as the Kobe agreement and the prior art, and to try to show that some technical matters were CGK on the basis of repeated references in TDocs. I recognise that this is theoretically potentially relevant but its weight is necessarily limited by not knowing how the authors themselves corresponded to the notional ordinary skilled person. The parties provided a helpful agreed chronology identifying the TDocs relied on, and I have reviewed the ones that were the subject of evidence or submissions at trial. I deal with some specific instances below, but I will say at this stage that in general I did not find this sort of thing very helpful, in its nature or volume, and where I have not dealt specifically with such TDocs it is because I thought them insufficiently important. I should also say that there is a difference between looking at what real people thought a document meant (which is ultimately a matter of law), and looking at what they thought could be done with it.
52. I consider my analysis above is consistent with the decision of Birss J as he then was, and then of the Court of Appeal, in Unwired Planet v. Huawei [2015] EWHC 3366 (Pat) and EWCA Civ 266, cited by Apple, that the skilled person in the field of telecoms would find out what was happening in general terms in the relevant standards organisation, and that an expert witness who did not do the same thing would not be doing their job. Gaining a general appreciation does not mean reading everything going on and was not intended by Birss J or the Court of Appeal to water down the requirement that CGK is that which is generally known and a good basis for further action. Floyd LJ also referred to the use of specific proposals which were not CGK as “providing a useful injection of reality”. As I have said, I accept that in principle but its usefulness depends on the facts, and proportionate deployment of such materials. In particular, I think the two decisions are consistent with my view of the skilled person checking recent meeting minutes for significant, firm decisions.
Agreed common general knowledge
Cellular network architecture
53. Each generation of mobile phone technology has a different architecture. However, they all share some common features. The key components are the mobiles, the base stations, and the core network.
54. There have been several different generations of cellular technology. The first generation of mobiles was entirely analogue and was introduced in the 1980s. The second generation (2G) is known as GSM (Global System for Mobile communications) and was the first digital system. GSM was first launched in the early 1990s and was initially a voice only technology. The third generation (3G) is known as UMTS (Universal Mobile Telecommunications System), was launched in the early 2000s, was based around Wideband Code Division Multiple Access (WCDMA) and supported high speed data as well as voice. The fourth generation of mobile phone technology uses LTE (Long-Term Evolution). Work on defining the standards was ongoing from 2005 and it was launched in the late 2000s and allowed much higher data rates.
55. Each generation of mobile technology also uses different names for certain components of the network architecture. For example, the base stations are known by various terms depending on the technology used. GSM (2G) uses the term BTS (Base Transceiver Station), WCDMA (3G) uses the term nodeB and LTE (4G) uses the term eNodeB (eNB).
56. The purpose of a mobile telecommunications network is to transmit information, referred to as “user data” (e.g., sound, text, images) to and from a mobile user efficiently, with minimal errors and distortions. Separately, information needs to be exchanged between users and the network in order to manage users’ connections e.g., for scheduling their transmissions. This is referred to as “control data”.
OSI Protocol model
57. The OSI 7-layer model (the Open Systems Interconnection model) is a conceptual model that characterises the communications functions between computing systems. The seven abstraction layers are described below in Table 1.
|
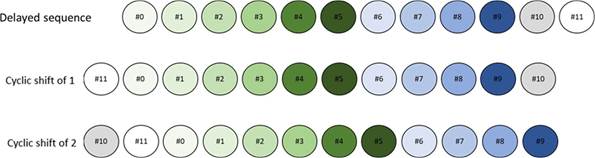
Layer Number |
Layer Name |
Main Roles |
|
1 |
Physical Layer |
Transmits raw bit streams over the physical medium. In the case of mobile communications, the physical medium is the radio spectrum. |
|
2 |
Data Link Layer |
Responsible for the reliable transfer of data frames from 1 node to another connected by the physical layer. |
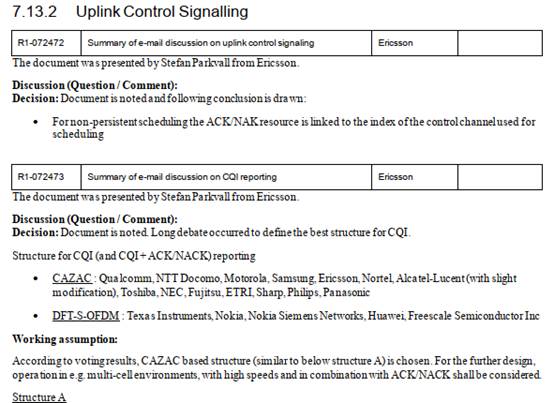
|
3 |
Network Layer |
Manages the delivery of individual data packets from source to destination through appropriate addressing and routing. |
|
4 |
Transport Layer |
Responsible for delivery of the entire message from the source host to the destination host. |
|
5 |
Session Layer |
Establishes sessions between users and offers services like dialog control and synchronisation. |
|
6 |
Presentation Layer |
Monitors syntax and semantics of transmitted information through translation, compression, and encryption. |
|
7 |
Application Layer |
Provides high-level APIs to the users. |
Table 1 - The OSI 7 layer model. (tutorialpoint.com)
58. Layers 1 and 2 of the OSI model are of most interest when considering the PUCCH and how it fits in with LTE. The PUCCH is a physical layer (layer 1) channel which is used to carry certain types of information between layer 2 on the mobile device and layer 2 on the base station.
59. Layer 2 of LTE includes multiple sublayers and one of these is the Medium Access Control (MAC) layer. MAC performs several different roles. One is error correction which it performs using a process called HARQ (Hybrid Automatic Repeat Request). HARQ, which is explained further below, relies on the transmission of control information. PUCCH can be used to send this information from the mobile device to the base station.
60. Another role of MAC is that of scheduling. Scheduling is performed at the base station side and involves the selection of various parameters for the transmissions to and from the base station. These parameters require various measurements to be made by the mobile device and reported to the base station. PUCCH is one of the channels that can be used to send this information.
Multiple Access Methods
61. The radio spectrum that is suitable for use within a cellular network is a finite resource. This resource must be shared between different types of wireless technology which could interfere with each other if they used the same frequencies. For these reasons the allocation of various bands for specific uses needs to be coordinated carefully. This is done at a national level (e.g., by Ofcom in the UK) and at an international level (e.g., by the International Telecommunication Union).
62. Operators use network planning techniques to make efficient use of their spectrum allocations. This could involve the careful selection of which frequencies are used in neighbouring cells and/or the coordination of other parameters designed to reduce interference between nearby cells.
63. The different transmitters within a cell (the base station and mobiles) must also all access this finite resource in an efficient manner. This can be done by a system that allows multiple transmissions at the same time and/or a system that switches so rapidly between the users that the switching is not noticeable.
Uplink and Downlink Duplexing
64. A first level of multiplexing separates the uplink signal (transmitted by the mobile devices) from the downlink signal (transmitted by the base station). This is referred to as duplexing of which there are two main types. These are Frequency Division Duplexing (FDD) and Time Division Duplexing (TDD). In an FDD system, different frequencies are allocated to the uplink and downlink. The distance between the uplink and downlink frequency is called the duplex spacing and can be very large.
65. In a TDD system both the base station and the mobiles use the same frequencies. In this case, they are separated in time. Part of the time the base station is allowed to transmit and part of the time the mobiles are allowed to transmit.
66. Each method of duplexing has its advantages and disadvantages. Some technologies (such as WCDMA) can use either FDD or TDD.
Multiple access methods
67. Multiple access is the process that allows multiple users to receive and/or transmit at the same time or effectively at the same time. Multiple access is much simpler on the downlink as there is only one transmission source (the base station). For the mobile, this makes it a simpler process to extract its own data.
68. Multiple access on the uplink is more difficult because there are many different transmission sources (the mobiles). In addition to being at different positions, each mobile device can have different frequency errors, timing errors and other types of channel impairments. These all increase the potential for interference between the different uplinks.
Frequency Division Multiple Access
69. In a Frequency Division Multiple Access (FDMA) system each user is separated by its own frequency (or channel) within the resources allocated for the uplink.
Time Division Multiple Access
70. Time Division Multiple Access (TDMA) is similar to the TDD method described above. Each mobile is allocated a time slot when it is allowed to transmit. GSM is an example of a system that uses TDMA.
Wideband Code Division Multiple Access
71. Code Division Multiple Access (CDMA) does not use separate times or frequencies for each transmission but instead uses a process known as scrambling. Each mobile is allocated a unique scrambling code which is used to scramble its data before transmission. The base station can recover the information transmitted by each mobile device by performing descrambling using the same scrambling code used by the mobile device.
72. WCDMA uses CDMA on the uplink to separate the different mobiles. WCDMA performs scrambling at a fixed rate (known as the chip rate) which is 3.84 Mchip/s.
73. Each mobile needs to combine several streams of data (channels) before they can be scrambled. The symbol rate of each of these channels is lower than the chip rate used for scrambling. To combine the individual channels and to increase the data rate to the correct chip rate another type of code is used. These codes are known as channelisation codes (or alternatively spreading codes). UMTS uses Orthogonal Variable Spreading Factor (OVSF) codes for its channelisation codes. The receiver can recover the original data from each stream by a process known as despreading.
Orthogonal Frequency Division Multiple Access
74. Orthogonal Frequency Division Multiple Access (OFDMA) is a multi-user version of Orthogonal Frequency Division Multiplexing (OFDM).
75. Instead of a single carrier, OFDM uses multiple carriers which are used to transmit parallel streams of data. Each individual carrier is called a subcarrier. Each subcarrier is separated by the same subcarrier spacing. The subcarrier spacing is selected so that it is the inverse of the symbol period. For example, LTE uses a subcarrier spacing of 15kHz and an LTE symbol has a period of 1/15kHz. This has the effect that individual subcarriers can be demodulated without any interference between each other, i.e., the subcarriers are orthogonal.
76. OFDMA extends this basic scheme by allocating a subset of the subcarriers to each mobile. Each mobile generates the signal for its subcarriers and sets the subcarriers that are not part of its allocation to zero.
77. OFDMA suffers from a high peak-to-average-power ratio (PAPR). This means a device using OFDMA would require a more powerful power amplifier (“PA”) (resulting in higher cost and a shorter battery life). For this reason, OFDMA was rejected for the uplink of LTE. But OFDMA was selected for the downlink of LTE as the cost of the PA was not as great a consideration in the base station.
Single Carrier Frequency Division Multiple Access
78. Single Carrier Frequency Division Multiple Access (SC-FDMA) is similar to OFDMA; the main difference from OFDMA is a precoding stage which combines inputs mapped onto consecutive subcarriers, followed by the last stage of the OFDMA approach. SC-FDMA results in a signal with a lower PAPR compared to OFDMA. This lower PAPR was the main reason for the selection of SC-FDMA for the uplink of LTE.
Orthogonal codes
79. Orthogonal codes were used in 3G CDMA systems, including UMTS. They are made up of a series of binary bits (represented by 1 and -1) arranged in a particular order.
80. Two codes are said to be orthogonal if when the corresponding bits are multiplied together and the product of the multiplication is added up, the result sums to zero as shown in the example below:
|
Orthogonal code A: |
1 |
1 |
1 |
1 |
|
|
Orthogonal code B: |
1 |
-1 |
1 |
-1 | |
|
Multiplication product (A x B): |
1 |
-1 |
1 |
-1 |
SUM=0 |
81. Orthogonality enables the receiver to pick out the relevant signal while minimising the interference from other signals sent at the same time and frequency, which is perceived as random noise. However, noise, interference and distortion of the radio channel may mean that other encoded messages which as encoded were orthogonal are not perfectly orthogonal when received, thus making it more difficult for the receiver to correctly pick out the signal for a particular user. This is because errors in the codes may make the codes appear more similar to one another. This “inter-code interference” would increase with the number of different signals that are code-multiplexed.
82. The length of an orthogonal code is referred to as the “spreading factor”. This may be thought of as the number of bits used to construct the code that encodes a single bit of data. (For example, the two codes used in the example above are 4 bits in length and have a spreading factor of 4.)
83. “Spreading” is the process by which a user’s data bits are multiplied with the bits that make up the code. This can have the effect of spreading the data out over a longer period of time. For example, if the single bit of original data occupied 1 notional unit of time, after being spread by an orthogonal code of length 4, that data would now occupy 4 notional units of time. The output bits resulting from this spreading process are sometimes referred to as “chips”.
84. Data from different users is spread with different codes and then the outputs are received by the receiver as a composite waveform made up of the signals from all the different users. The receiver knows the code used by each user and applies this code to the waveform that it receives in order to pull out or “de-spread” the data for a particular user.
85. For an orthogonal code of a given spreading factor N, there are N-1 different codes which are orthogonal to it. Thus, for example, for spreading factor 4 there are a total of four available orthogonal codes each of length-4.
86. There is a set of codes that exist for spreading factors that are a power of two. These codes can be written in various orders. The names “Walsh” and “Hadamard” are associated with such codes.
Impairments in mobile systems
87. There are various impairments in a mobile communication system which can degrade the signal that is received. If the impairments become severe enough it can become impossible for the receiver to recover the original data.
Noise
88. Noise is an unwanted signal that is superimposed onto the original transmission. Noise in wireless communications can occur because of natural background processes and it can be self-generated in the receiver.
Interference
89. Interference is an unwanted signal from other devices. Typical sources can include other mobile devices and base stations. These devices can be from inside or from outside the current cell. These devices can also be from different technologies altogether, e.g., microwave ovens.
Frequency offsets
90. Both the transmitter and receiver need to accurately reproduce the same frequency to be able to reliably transmit and receive the signal. Any error in the transmitter or receiver frequency can potentially degrade the ability of the receiver to recover the signal (e.g. because of limited frequency reference accuracy or the effects of Doppler offset, which is explained further below).
Channel conditions
91. In this context, the channel describes the physical environment between the transmitter and receiver. The received signal is greatly affected by the channel conditions that it has passed through. Sometimes the channel can be benign, for example when there is a Line of Sight (LOS) between the transmitter and receiver and no other adverse conditions. In other environments there may be no LOS, or the radio signal may suffer from reflections (such as off buildings) before it arrives at the receiver.
92. These reflections cause impairments which can make the signal difficult or impossible to recover. The reflections can combine to make the signal weaker or stronger. This effect tends to vary over time and may not affect all parts of the channel bandwidth equally. This effect is known as fading.
93. The various reflections can cause the signal components to arrive at slightly different times. This is known as dispersion, or delay spread.
94. Another type of impairment is Doppler spread. When the mobile is moving quickly with respect to the base station the Doppler effect means that the radio waves transmitted by the mobile will appear to change in frequency: the transmitted frequency will appear to be shifted higher (bunched up) if the mobile is moving towards the base station, and lower (stretched out) if the mobile is moving away from the base station. Copies of the signal that take different paths, as discussed above, will be affected differently by the Doppler effect. This will have the effect that the copies received at the receiver will be spread over a range of frequencies. Doppler spread has the effect that the way in which the different frequencies in the radio channel are affected by fading changes with time. A fast-moving mobile experiencing a high Doppler spread will typically experience rapid changes in its radio channel characteristics as it moves through the environment and the propagation paths change. This effect will be more pronounced when mobiles are moving at greater speeds e.g., when a user is on a high-speed train.
Techniques for overcoming impairments
95. This section describes some of the techniques that have been developed to overcome the impairments described above.
Pilot signals
96. A pilot is a known signal that is transmitted along with the data. The pilot information is affected by the channel conditions in the same way that the rest of the signal is. The receiver has knowledge of what pilot signals are transmitted and can use this information to estimate the current channel conditions. It is then possible to reverse some of the effects of the channel. Even with a pilot, it is not always possible to create a perfect estimate of the channel conditions, and this can limit how well the signal can be recovered.
97. The use of pilot signals cannot help with all the impairments described above. For example, noise and interference cannot be improved by this type of channel estimation as the pilot and other signals are not affected in the same way by these two impairments.
98. LTE uses the term “reference signal” to refer to pilot signals.
Error detection and error correction
99. Errors after the signal has been received can affect the system in different ways. Sometimes it is possible to allow a small number of errors with only a small degradation in performance, for example in voice calls. However, often when errors are detected, the whole message is of no use and must be discarded or retransmitted.
100. Various techniques have been developed to both correct any errors that have occurred (error correction) and detect the presence of any errors that remain (error detection).
101. Most wireless standards use several different types of error correction depending on the type of message being sent. They all involve increasing the message size by the transmission of extra data (redundancy or parity) along with (or instead of) the original message. The receiver can then use the extra data to correct all or some of the errors that may have occurred.
102. The use of a Cyclic Redundancy Check (CRC) is a standard way of detecting errors in most wireless communications. For a CRC, error detection is typically done by adding extra data to the end of a sequence of message bits. These extra bits are calculated based on the message.
Automatic Repeat Request
103. If messages are detected with errors (a CRC failure) or are not received at all they may need to be sent again. This is often done using a process called Automatic Repeat Request (ARQ). ARQ requires the transmission of control information in the opposite direction to the information being sent. These are acknowledgments (ACKs) or negative acknowledgments (NACKs) which indicate that a message has either been received correctly or not.
104. Figure 8 shows a basic ARQ message flow. In this example the transmitter (TX) sends a message (msg 1) to the receiver (RX). The receiver does not detect any errors so sends an ACK back to the transmitter. A second message (msg 2) is then sent but this time an error is detected so the receiver returns a NACK. Upon reception of the NACK the transmitter resends msg 2. This time msg 2 is received correctly and an ACK is returned.
105. In early wireless communications systems (e.g., GSM and the early versions of WCDMA) this ARQ process was not implemented in the physical layer but was implemented at a higher layer in the protocol stack. This has the effect of adding latency to the process which degrades the quality of service experienced by the user. This was a motivation for the development of HARQ which is described in the next section.
HARQ
106. HARQ was introduced to the 3GPP standards for the HSDPA (High Speed Downlink Packet Access) feature which was added to WCDMA in 2002 (3GPP Release 5). One improvement provided by HARQ is that it reduces the amount of redundant information that must be transmitted for error correction purposes. It also reduces the latency caused by implementing the ARQ process at higher layers in the protocol stack. This is done by combining the error correction stage and the ARQ process and moving them down into the physical layer.
107. The example HARQ process shown in Figure 9 is similar to the standard ARQ example shown in Figure 8. A difference is that not all the information needs to be sent in the original transmission. It may contain a subset of all the information generated for the purposes of error correction. If the receiver can decode the information from the initial transmission an ACK is sent.
108. If the original transmission cannot be decoded a NACK is sent. Then, instead of resending the original message, the transmitter sends a different subset of the encoded message. At the receiver, instead of discarding the original message, it is combined with the second transmission.
109. There is a higher chance of successfully decoding the combined message compared to decoding the first or second transmission separately.
110. Moving the HARQ process to the physical layer created a new requirement for the physical layer to be able to send ACK/NACK data. HARQ can be implemented in both the uplink and downlink directions, in which case ACK/NACK data also needs to be sent in both directions.
111. As part of HSDPA, a new channel (the High Speed Dedicated Physical Control Channel, HS-DPCCH) was added to carry the uplink control information. This information includes the ACK/NACK data.
CQI
112. CQI was added to 3GPP as part of HSDPA. This CQI is sent from the mobile to the base station and represents an estimate of the maximum data rate that the mobile can receive.
113. This estimate is based on the mobile device’s measurements of the current channel conditions. In HSDPA this CQI information is sent as part of the HS-DPCCH which also carries the ACK/NACK data. The HS-DPCCH is a dedicated channel (a dedicated channel is dedicated to one mobile device). In the HS-DPCCH, ACK/NACK data occupies the first time slot of a subframe and CQI data occupies the second and third time slots of that subframe. CQI in LTE is described below.
LTE development.
114. The requirements for LTE were finalised in June 2005. There were many requirements of the LTE physical layer including:
i) Reduced transmission latency.
ii) Increased user data rates.
iii) Increased cell edge bit rates.
iv) Greater flexibility of spectrum usage.
v) Reasonable power consumption for the UE.
115. The selection of OFDMA for the downlink and SC-FDMA for the uplink were key design choices for the new LTE physical layer.
LTE frame structure
116. LTE uses a resource grid to describe both the uplink and downlink frame structure. The downlink frame structure is identical to the uplink frame structure and is described here in more detail. The LTE frame structure has an impact on the design choices for the PUCCH.
117. The smallest part of the resource grid is the resource element (RE). An RE consists of one subcarrier and is one symbol in duration. LTE uses a subcarrier spacing of 15kHz.
118. Individual REs are organised into resource blocks (RBs). An RB contains twelve subcarriers (180kHz) and either six or seven symbols. The number of symbols in one RB is dependent upon the cyclic prefix mode. If there are seven symbols an RB will contain 84 RE altogether. The duration of an RB is 0.5ms. LTE also uses the term “slot” to describe the duration of an RB.
119. ![]()
![]() Two slots form a subframe (1ms) and ten subframes form a frame (10ms). The number of RBs in the frequency domain depends on the bandwidth of the cell. The resource grid is shown in Figure 10 and Figure 11 below.
Two slots form a subframe (1ms) and ten subframes form a frame (10ms). The number of RBs in the frequency domain depends on the bandwidth of the cell. The resource grid is shown in Figure 10 and Figure 11 below.
120. This resource grid structure allows the frequency and time domain positions of various channels and signals to be easily described when the base station sends uplink and downlink resource allocations.
121. When large amounts of data are to be sent, multiple RBs can be assigned.
HARQ in LTE
122. To enable reduced latency (which was one of the key requirements for LTE), LTE adopted a Transmission Time Interval (TTI) of 1ms. This is the period that is used to transmit data.
123. HARQ was also adopted as a key feature of LTE. HARQ requires that ACK/NACK data is returned before the next message can be sent or the previous message retransmitted. To avoid any gaps in transmission that would have occurred while the transmitter is waiting for an ACK/NACK, a number of parallel HARQ processes are used, each of which run independently.
124. The downlink data is transmitted using the Physical Downlink Shared Channel (PDSCH). The ACK/NACK data is transmitted on the uplink using Physical Uplink Shared Channel (PUSCH) or PUCCH channels. Uplink control signalling is sent on the PUSCH if the UE has a PUSCH allocated otherwise it is sent on the PUCCH. Figure 12 below shows a message flow diagram of messages used for HARQ on the downlink in LTE.
CQI in LTE
125. The introduction of OFDMA (downlink) and SC-FDMA (uplink) in LTE made it possible for the base station to select which set of subcarriers are used for transmission on the uplink and downlink. The base station will select those frequencies which have the optimum channel conditions at that instance in time. To facilitate this scheduling the base station needs regular measurements of the channel conditions in each direction. The base station can then use the received CQI to adapt the modulation scheme and coding rates used on the PDSCH to channel conditions and to optimise time and frequency selective scheduling on the PDSCH.
126. To facilitate frequency selective scheduling a mobile device must make measurements of the downlink quality in various sub-bands and send this information to the base station in the form of CQI reports.
127. Since channel conditions can change quickly the CQI reports need to be sent regularly.
LTE uplink channels
128. While LTE has many advantages, it has some disadvantages too. These limitations have an important effect on the design of the LTE channels and how they can be used.
129. One limitation arises from the restrictions imposed by the choice of SC-FDMA as the uplink. The key benefit of SC-FDMA is that it produces a signal with good PAPR properties. However, if multiple SC-FDMA signals were transmitted at the same time the PAPR would increase and the main advantage of SC-FDMA would be lost. Therefore, in an SC-FDMA system, it is only possible to transmit one channel at a time.
130. A second limitation is the use of the 180kHz RB. This relatively large minimum resource allocation would make it very inefficient to send small amounts of control information unless it was possible for multiple mobile devices to share the same RB.
131. These limitations led to the adoption of just two main types of uplink channel; the PUCCH and the PUSCH. As at the priority date, the LTE standard only allowed the mobile to transmit on the PUCCH or the PUSCH separately but not simultaneously.
132. PUSCH is the main data channel and is used by the mobile to send user data and/or most signalling information. It can use a variable number of RBs depending on how much information is to be transmitted. Typically only one mobile can be allocated a PUSCH on a single set of RBs and because the PUSCH requires the allocation of a number of RBs that would no longer be available to another mobile, a PUSCH is only allocated when it is needed. For the same reason it is unlikely that a mobile will be allocated resources in all subframes.
133. The PUCCH is used for sending small amounts of control information. The types of control information include ACK/NACK data and periodic CQI reports.
The LTE Standards
134. References to Tables and Figures below are to the Tables and Figures in the standards, unless indicated otherwise.
At the Priority Date
135. The versions of the standards current as at the priority date were CGK. Version 1.2.0 of TS 36.211 (TS 36.211 v.1.2.0) and version 8.1.0 of TS 36.300 were both published before the priority date. I have held above that v.1.2.1 of TS36.211 was not CGK.
TS 36.211 v.1.2.0
136. Section 6.1.1 of TS 36.211 v.1.2.0 specifies that the uplink physical channels include the PUCCH.
137. Section 6.2 defines the uplink resource grid described above. It explains that the number of subcarriers in an RB is twelve, and that the number of SC-FDMA symbols in a slot (for frame structure type 1, which is the frame structure used for FDD) is seven for normal cyclic prefix and six for extended cyclic prefix. The number of uplink RBs is said to depend on the uplink transmission bandwidth configured for the cell and to be between 6-110.
138. Section 6.4 relates to the PUCCH and states that the PUCCH carries uplink control information and that the PUCCH is never transmitted simultaneously with the PUSCH. The formats supported by the PUCCH are shown in section 6.4 in Table 16, reproduced below as Table 3:
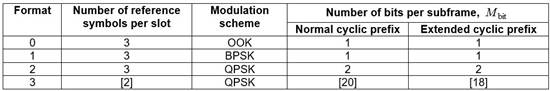 |
Table 3 - Slot formats supported by the PUCCH (Table 16 TS 36.211 v.1.2.0)
139. The Table states that format 0 uses an “OOK” modulation scheme and carries 1 bit per subframe. Format 1 uses “BPSK” and carries 1 bit, while format 2 uses “QPSK” and carries 2 bits. Format 3 uses QPSK modulation and might carry 20 bits when using normal cyclic prefix but only 18 bits when using extended cyclic prefix. In this regard, format 3 is different to formats 0, 1 and 2 which carry the same number of bits when using normal and extended cyclic prefix. The details of OOK, BPSK and QPSK are not relevant to the issues in this case.
140. Table 16 also specifies the number of reference symbols per slot for each of the formats. The terms “reference signals”, “reference symbols” and “DMRS” are often used interchangeably to refer to demodulation reference signals that are used for channel estimation (although DMRS are only one type of reference signal). A demodulation reference signal provides a pilot signal of the type described above to the base station to allow coherent demodulation at the base station. It is necessary to have a unique reference signal available for each different mobile sending information on the PUCCH. Formats 0, 1 and 2 each include three reference symbols per slot while format 3 might include two reference symbols per slot. There is no indication in TS 36.211 v.1.2.0 of where in the slot the reference symbols should be positioned.
141. Section 6.4.1 describes that scrambling may be applied to the bits to be carried on the PUCCH while section 6.4.2 describes that the scrambled bits are modulated with the scheme defined in Table 16 to produce a block of complex-valued symbols d(0),…, d(Msymb - 1). These symbols, referred to as “modulation symbols”, represent the bits which are transmitted by the various PUCCH formats. The SC-FDMA symbols carrying the DMRS and the SC-FDMA symbols carrying the modulation symbols are both affected by the propagation channel. The content of the DMRS is known to the base station and the base station can therefore use the DMRS as a phase reference to allow coherent demodulation of the modulation symbols.
142. Section 6.4.2 states that, “For OOK and BPSK, Msymb = Mbit , while Msymb = Mbit/2 for the other formats.” This means that for formats 0, 1 and 2 there will be only one modulation symbol, d(0) (carrying one bit for formats 0 and 1 and two bits for format 2, according to Table 16), while (assuming normal cyclic prefix) for format 3 there might be ten modulation symbols d(0),…d(9) (carrying 20 bits, again, according to Table 16).
143. Section 6.4.2.1 describes the sequence modulation for PUCCH formats 0, 1 and 2. That is, section 6.4.2.1 describes how the modulation symbol d(0) is spread to form a block of complex-valued symbols z(i) which will be mapped to the resource elements in which the PUCCH signal will be transmitted. Section 6.4.2.1 describes that for all formats the complex-valued symbol is multiplied with a cyclically shifted length-12 CAZAC sequence and is then block-wise spread with an orthogonal sequence. As I have said above the term orthogonal sequence is often used interchangeably with similar terms or variations of similar terms such as orthogonal cover code, orthogonal spreading code, and block-wise spreading code.
144. A CAZAC sequence is a sequence which has constant amplitude and has no correlation with a time-delayed version of itself (constant amplitude zero auto-correlation). One example of a CAZAC sequence is a Zadoff-Chu sequence, sometimes referred to as a “ZC” sequence.
145. The CAZAC sequences that were to be used in the frequency domain on the PUCCH were required to be length 12, corresponding to the 12 subcarriers available in an LTE resource block, each of which could carry one of the complex numbers in the sequence. The 12 different cyclically shifted CAZAC sequences could be formed from a length-12 root sequence.
146. The properties of the length-12 CAZAC sequence are such that twelve mutually orthogonal sequences can be produced by applying twelve different cyclic shift values to the sequence. When the base station receives a signal modulating the cyclically shifted length-12 CAZAC sequence from a mobile, it performs a correlation process. From the peaks in the correlation result it is possible to determine which cyclic shift was transmitted. A cyclic shift is achieved by shifting a sequence so that symbols are rotated from the end of the sequence to the start by the size of the shift.
147. The multiplication of the modulation symbol d(0) with a cyclically shifted length-12 CAZAC sequence results in a block of twelve complex-valued symbols y(0),..., y(NZC -1) . This can be thought of as a frequency domain spreading which is performed to spread the d(0) modulation symbol over the twelve subcarriers in a resource block.
148. The block-wise spreading of the block of twelve complex-valued symbols y(0),..., y(NZC -1) involves multiplying this block of symbols by each of the elements of an orthogonal sequence w(i) to produce twelve complex-valued symbols for each element of the orthogonal sequence. There are seven symbols in a slot and three of these symbols are used for the reference signal. This leaves four symbols in a resource block in a slot over which to block-wise spread the d(0) information with the orthogonal sequence w(i).
149. The result of the multiplication with the cyclically shifted length-12 CAZAC sequence and the block-wise spreading is a block of complex-valued symbols z(i) which contains one complex-valued symbol for each of the resource elements of the four SC-FDMA symbols in one slot of a subframe which will carry the d(0) information.
150. Section 6.4.3 describes that the block of complex-valued symbols z(i) is mapped in sequence to the resource elements assigned for transmission of the PUCCH.
151. Following the mapping of the block of complex-valued symbols z(i) to the resource elements of a resource block, an Inverse Fast Fourier Transform, “IFFT” (the details of this do not matter) is performed for each symbol to produce a time-domain signal and a cyclic prefix added to produce the final SC-FDMA symbol.
152. Section 6.4.3 also describes that the mapping of modulation symbols for the PUCCH onto resource elements is such that frequency hopping occurs at the slot boundary. This is shown in Figure 18 of TS 36.211 v.1.2.0 section 6.4.3 which is reproduced as Figure 17 below.
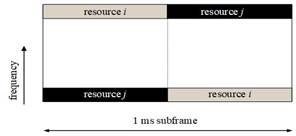 |
Figure 17 - Figure 18 of TS 36.211 v.1.2.0
153. Section 6.4.2.2 describes the sequence modulation for PUCCH format 3. It describes that for format 3, each complex-valued symbol is multiplied with a cyclically shifted length-12 CAZAC sequence.
154. For format 3, as described above, there might be ten modulation symbols d(0),…, d(9) carrying 20 bits. There is no block-wise spreading performed in the sequence modulation for format 3. Instead, each of five SC-FDMA symbols in each of the two consecutive slots forming the PUCCH resource is used to carry a respective one of the modulation symbols d(0),…, d(9). The multiplication with the cyclically-shifted sequence produces a block of complex-valued symbols z(0),...,z(NZCMsymb -1), and this is mapped in sequence to the resource elements across the two resource blocks of the PUCCH. An IFFT is then applied in respect of each SC-FDMA symbol period to produce a time-domain signal and a cyclic prefix added to produce the final SC-FDMA symbol.
155. TS 36.211 v.1.2.0 does not include any detail on how the cyclic shift and orthogonal sequence to be used in generating a format 0, 1 or 2 signal is to be determined or which combinations of cyclic shifts and orthogonal sequences will be available to be allocated. There is no detail in this version of the standard of how to determine the cyclic shift to be used for generating a format 3 signal or which cyclic shifts will be available to be allocated.
156. Based on Table 16 of TS 36.211 v.1.2.0 (Table 3 above) and the number of bits that can be carried by each of the formats, PUCCH format 0 would be for scheduling requests, formats 1 and 2 for 1 or 2 bits of ACK/NACK and format 3 for CQI.
157. TS 36.211 v.1.2.0 also includes section 5.8.1 which relates to the physical downlink control channel (PDCCH). This section describes that a PDCCH carries scheduling assignments and is transmitted on an aggregation of one or several control channel elements where a control channel element corresponds to a set of resource elements. It mentions that the PDCCH supports multiple formats. PDCCH formats 0 and 1 are listed in a table but no further information is provided about these formats.
TS 36.213 v.1.2.0
158. TS 36.213 v.1.2.0 section 9.1 is entitled “UE procedure for determining physical downlink control channel assignment”. It consists of the following text:
“[includes determining ACK/NACK, CQI, SR physical uplink shared control channel assignments which maybe implicitly based on downlink L1/L2 control channel assignments or explicitly signalled]
A UE is required to monitor a set of control channel candidates as often as every sub-frame. The number of candidate control channels in the set and configuration of each candidate is configured by the higher layer signaling.”
TS 36.300 v. 8.1.0
159. TS 36.300 v.8.1.0 section 5.2.3 describes that the PUCCH is mapped to a control channel resource in the uplink. It describes that a control channel resource is defined by a code and two RBs, consecutive in time, with hopping at the slot boundary. Section 5.2.3 also states that, where there is time synchronization, the control signalling consists of CQI signals, ACK/NACK signals and scheduling requests. It describes that a CQI informs the scheduler about the current channel conditions as seen by the UE and that the HARQ feedback in response to downlink data transmission consists of a single ACK/NACK bit per HARQ process. TS 36.300 v.8.1.0 does not state which PUCCH formats would be used for the transmission of ACK/NACK, CQI and scheduling requests.
160. TS 36.300 v.8.1.0 section 5.1.3 describes that the PDCCH is located in the first up to 3 OFDM symbols of each subframe. It states that “Multiple physical downlink control channels are supported and a UE monitors a set of control channels”.
161. It also explains that “Control channels are formed by aggregation of control channel elements, each control channel element consisting of a set of resource elements. Different code rates for the control channels are realized by aggregating different numbers of control channel elements.”
162. TS 36.300 v.8.1.0 also states that the target NACK to ACK error rate (i.e., where a NACK is erroneously received as an ACK) is 10-4 to 10-3 and the target CQI block error rate is 10-2 - 10-1.
Disputed common general knowledge
163. I now turn to the areas where there was a dispute about CGK.
CAZAC sequences
164. CAZAC sequences are referred to above in the agreed CGK section. A point of detail was in dispute, however. The parties’ document in the section dealing with matters where the technology was agreed but the CGK status was not said as follows:
“In the time domain, one cyclic shift of a length-12 CAZAC sequence corresponds to a time- difference of 1/12th of a symbol. While all 12 cyclically shifted CAZAC sequences that could be formed from a length-12 root CAZAC sequence would be theoretically orthogonal, in practice the orthogonality between two different cyclically shifted sequences at the receiver could be reduced due to delay spread caused by multipath effects and loss of time-alignment between different mobiles on the LTE uplink. This could lead to inter-code interference between two mobiles using different cyclic shifts to spread their signals. It was known that loss of orthogonality would occur when the delay spread, or loss of time alignment exceeded the cyclic shift time. Therefore, the risk of inter-code interference was greatest for sequences that were only a single cyclic shift apart, whereas those separated by additional cyclic shifts would be more robust to this kind of interference. [The figure] below is a simple illustration that shows substantial overlap between two adjacent cyclically shifted sequences where one is delayed.”
 |
165. What was in issue was whether it would be CGK that the risk of inter-code interference would be greatest for sequences only a single cyclic shift apart. This dispute seemed inconsequential given the explanations in the cited prior art and the parties accordingly paid little attention to it at trial. It is certainly true that CAZAC sequences had not been used in this field before, but this sort of basic matter would, I find, have been identified by a skilled person preparing to use them in practice and would therefore be relevant to assessing obviousness even if not called out in the cited prior art and not CGK as such.
LTE frequency and resource allocations
166. The parties’ document included the following:
“LTE would be more flexible in the radio bandwidth used, allowing each operator and country to take advantage of the limited radio spectrum available. Compared to UMTS which operated only in 5MHz bandwidths, LTE would allow for frequency allocation flexibility with possible allocations at the priority date of 1.4, 1.6 (TDD mode), 3, 5, 10, 15 and 20 MHz.
Different LTE bandwidths encompass different numbers of resource blocks in the frequency dimension (i.e., in a single slot). For example, the number of resource blocks in each of the LTE FDD bandwidths would be as follows:
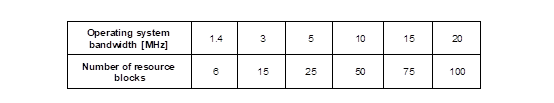 ”
”
167. Mr Edwards said in his reports that this was CGK and he was not challenged so I find it was CGK. It is of little importance; its place in the case is that it is an early and minor building block in Apple’s case for the obviousness of multiplexing ACK/NACKs and CQIs in the same resource block. For the narrowest bandwidth it can be seen that there are only 6 resource blocks in a slot. That argument by Apple fails for reasons given below, and this issue over CGK does not make any difference to my conclusion. I find that the skilled person would know as CGK that there would be narrow bandwidth implementations of LTE where there were few resource blocks per slot, and would find out more if they needed to.
PUCCH
168. Version 1.2.1 of TS 36.211 gave further details of the PUCCH in various ways, and because the parties disagreed about whether v.1.2.1 was CGK, it was therefore in dispute whether those details were CGK. I have held that v.1.2.1 was not CGK and so neither were those details, which were listed at paragraph 140 of the agreed CGK document.
169. The significance of the v.1.2.1 point was modest in any case. In relation to the PUCCH, v.1.2.1 contains a blank table with four rows for reference signals. Apple tried to use that to undermine Optis’ reliance on the equivalent table for data symbols. I accept Counsel for Optis’ submission based on Mr Bradford’s evidence that this aspect of v.1.2.1 would be seen as an obvious editing error in any event.
170. There was also a dispute (separate from the v.1.2.1 point) about whether use of an odd number of resource block pairs on the PUCCH was CGK. This was relevant because it was part of Mr Edwards’s analysis of the obviousness of multiplexing CQIs and ACK/NACKs in the same resource block. Mr Edwards’s view as expressed in his written evidence was that a technique called “puncturing” would allow the meaningful use of an odd number of resource blocks for the PUCCH. Mr Edwards’s view, and Apple’s argument, was based on a conclusion reached at RAN1 meeting #47bis and recorded in TDoc R1-070602. But the conclusion was at best tentative and qualified, and this plus the limited availability and clarity of these materials in the light of my general views of RAN1 materials expressed above means that this was not CGK.
171. In cross-examination of Mr Bradford Apple advanced a different point, which was that TS36.300, agreed to be CGK, showed at 5.2.3 the PUCCH being mapped to a control channel resource on the uplink defined by a code and two resource blocks (i.e. a single pair). This was not a point that had been supported by Mr Edwards in his reports and I accept Counsel for Optis’ submission that although TS36.300 says that a control channel resource has a single pair of resource blocks, there is no explanation of whether the control channel resources themselves come singly or in pairs.
PDCCH
172. The dispute here was over the degree of knowledge that was CGK in relation to how CCEs would be grouped in aggregates on the PDCCH.
173. Optis accepts that it was CGK that there would be levels of aggregation of CCEs on the downlink control channel, and that UEs would find out their individual control channels by blind decoding. That was all that mattered to the arguments, and further detail which was given in Dahlman and in v.1.2.1 does not matter, as I believe the parties agreed. The relevant figure in Dahlman (which is reproduced below) was used to illustrate various points during the oral evidence and argument, but the points did not depend on the fine detail, only on the facts that there was aggregation, there was blind decoding and that the control channel candidates were more numerous than the CCEs. I find that the greater detail in Dahlman and in v.1.2.1 was not CGK, consistently with my analysis above.
Implicit Signalling of Resource Allocation - Kobe agreement
174. In theory it might be possible to signal explicitly to each UE on the downlink what resource it should use on the PUCCH for signalling ACK/NACKs, but this would use a lot of resource. Apple contends that it was CGK at the priority date that implicit signalling would be used, i.e. a UE could infer from the information it received on the PDCCH what resource it should use on the PUCCH.
175. This had been discussed in RAN1, and at meeting #49 in Kobe it was resolved that “For non-persistent scheduling the ACK/NACK resource is linked to the index of the control channel used for scheduling.” The relevant section of the minutes as a whole is as follows:
176. The first part of this, following “Summary of e-mail discussion on uplink control signalling” with its “following conclusion” that “[f]or non-persistent scheduling the ACK/NAK resource is linked to the index of the control channel used for scheduling” is a clear disclosure of implicit signalling. Whether it was CGK does not matter all that much to obviousness because this “Kobe agreement” is referred to explicitly in both pieces of cited prior art. It might however matter to interpretation of the claims and it was argued out before me so I will decide it. This is also a convenient place to cover discussions following on from the Kobe agreement, which were relied on by the parties as shedding light on what it meant (or perhaps was thought to mean).
177. Consistently with my views as to the skilled person and approach to CGK in this case, the fact that the decision is recorded in meeting minutes would not, without more, make the Kobe agreement CGK. But there is further material in this instance, which is the fact that the agreement was picked up by numerous other companies, including Nokia and Panasonic, and was quite extensively discussed. The decision in favour of implicit signalling is also a fundamental one which it seems very unlikely would later be reversed, and that differentiates it from other more detailed points said by Apple to be CGK which were provisional, discussed only slightly, or liable to further change.
178. I therefore conclude that the CGK would include the Kobe agreement.
179. I do not think the Kobe agreement is ambiguous about what was agreed: it was that the index of the control channel on the downlink would be used to signal the uplink resource. In other words, it is a specific type of implicit signalling using the number of the downlink control channel.
180. To expand on this: it might have been possible for the decision simply to have been in favour of implicit signalling with details to follow, or (as I hold was the case) it might have been that the delegates decided for a specific kind of implicit signalling.
181. In document R1-072472, Stefan Parkvall of Ericsson had suggested two methods of implicit signalling, either an association with the control channel index (which was adopted) or association with “the downlink resource blocks”. It was not clearly established before me what the meaning of the latter was, although Apple submitted it referred to downlink data. In any event, the latter was not adopted and both proposals are quite specific. I do not think the skilled person would be likely to go back through proposals leading to the Kobe agreement so the ‘472 document is not CGK or directly available to interpret it, but it is consistent with and in a broad sense supports my clear impression that the reader of the Kobe agreement would think it was a specific decision to use the channel index, not just a general notion of implicit signalling. There are a number of other proposals in the TDocs leading to the Kobe agreement which also reflect RAN1 participants having entered into detailed considerations and having proposed using the control channel index. They are not however mentioned in the same way as the ‘472 document in the meeting minutes.
182. Subsequently, there was further discussion about the Kobe agreement, and in particular there was a suggestion from Panasonic in June 2007 that it was open to two interpretations: linkage to the control channel index, or linkage to the CCE. Panasonic suggested that there were pros and cons, in particular that the former would use more overhead while the latter would lead to some unused ACK/NACK resource. I agree with Optis that this document is a diplomatically-phrased attempt to reopen the Kobe agreement, which clearly refers to the first of the two interpretations. This document is not CGK in my view, being but one suggestion for a meeting, and which was not acted on. But it does illustrate that the discussions had reached questions of implementation detail, and that the choice between using the control channel index and the CCE number was not a simple one.
183. Two other companies made suggestions after Kobe but before the priority date about using the CCE for implicit signalling: Samsung and LG. The oral evidence did not dig into the detail of these and they were merely TDocs and therefore not argued to be CGK in themselves.
184. Finally, I ought to mention that in addition to the possibility of using the CCE or the control channel index, the oral evidence at trial touched on the possibility of using the index of control channel candidates (i.e. possibilities). What this is can be appreciated from the following figure from Dahlman (Figure 16.18).
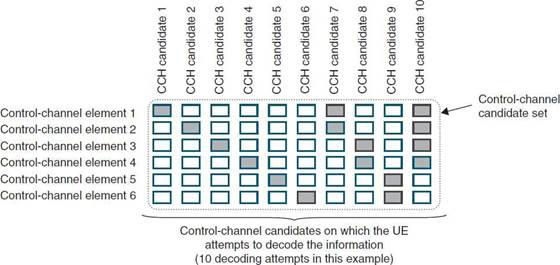 |
185. There are ten possible downlink channels for the UE to blind decode and which it would be possible (a “candidate”) that the UE would find was intended for it: 6 possibilities of one CCE, three possibilities of an aggregation of two CCEs, and one possibility of an aggregation of four CCEs. It might have been possible to use the candidate numbers for implicit signalling but it would not be attractive and does not affect my reasoning.
Mixed Resource Blocks
186. Apple contended that it was CGK to multiplex both ACK/NACKs and CQIs from different UEs in the same PUCCH resource block (such a block is called a mixed resource block, which I will abbreviate to “MRB”). This was based on the evidence of Mr Edwards, who in his first report relied for that view on the minutes of RAN1 meeting #49 where the CAZAC structure for CQI was chosen, and at the same time reference was made that “operation in e.g. multi-cell environments, with high speeds and in combination with ACK/NACK shall be considered”.
187. I have quoted the whole relevant section above, since it comes in the same document as the record of the Kobe agreement.
188. It should be noted that the reference relied on by Apple comes after the heading “Working assumption”. This connotes some general acceptance, and the question is what it means.
189. Apple’s argument is a somewhat complex one. It involves going back to document R1-072472, which I have referenced above in relation to the agreement on implicit signalling. But that document is not from the same section of the minutes as the section which addresses CQI. That section references a different document, R1-072473, which Apple did not rely on.
190. The ‘472 document refers to two transmission structures for CQI, “A” and “B”. “A” uses ZC modulation and “B” uses a different modulation. Reverting to the #49 minutes, one sees that “for CQI (and CQI+ACK/NACK) reporting”, a CAZAC structure “similar to below structure A” is chosen, and that is the ZC arrangement from the ‘472 document.
191. Optis said that “CQI+ACK/NACK” was used to refer to UEs which were sending a CQI and an ACK/NACK at the same time. Mr Edwards agreed that the expression was sometimes used that way, in TDocs and in his own written evidence. No document was identified by him or Apple which used it to refer to different UEs sending a CQI and an ACK/NACK at the same time.
192. This is a very confused picture and even assuming that the RAN1 #49 minutes can be resorted to in this way, the further reference to underlying TDocs does not reflect CGK.
193. Mr Edwards identified some other pre-priority RAN1 documents in his second report to try to show that MRBs were CGK. These were also not generally available, being in email discussions or TDocs which were not necessarily even considered at the relevant meetings (out of the twelve relied on eight were not treated and four merely noted). So they do not help on CGK.
194. Apple also relied on Mr Bradford having noted in his written evidence that [0007] of the specification of 549 said MRBs were CGK, and having agreed with it. He did say this and it was inconsistent with his oral evidence, which was clearly that they were not CGK. I think his written evidence was not what he actually thought. I prefer and accept his oral evidence.
195. Optis relied, through Mr Bradford, on TS 36.211 v.1.2.0 because it gave different formats for scheduling requests and ACK/NACKs on the one hand (formats 0, 1 and 2) and CQIs on the other (format 3), while saying that the former two could share a resource block, and not saying the same about format 3. Since the materials relied on by Apple and identified above do not make MRBs CGK, this counterargument from Optis does not really matter, but for what it is worth I agree that it is mildly supportive of Optis’ position.
196. So I conclude that MRBs were not CGK. This does not matter in relation to obviousness over Nokia since that discloses MRBs explicitly, but it is relevant to obviousness over Panasonic. The dispute over the CGK status of MRBs does not imply that there would be any difficulty implementing them if the skilled person thought of it and wanted to do it. Optis did not argue that there was any such difficulty. While I have rejected Apple’s collection of RAN1 documents mentioning MRBs as not being CGK, they do provide some evidence that if the skilled person was struggling with a particular problem of capacity in the uplink channel it is possible that they would themselves think of an MRB as a solution. I have borne this in mind when assessing obviousness over Panasonic.
The Patents
197. As I have said above, all references are to paragraph numbers in 549.
Claims of the Patent in issue
198. The claims on which I have to decide this case are:
i) Claim 1 of 549;
ii) Claim 7 of 549 as dependent on claim 1;
iii) Claim 8 of 549 as dependent on claim 1;
iv) Claim 1 of 810;
v) Claim 2 of 810 as dependent on claim 1.
199. These are all product claims. Optis gave up on the method claims because the functionality in the standard is not used in the UK and so Apple neither offers the method for use by purchasers of its phones, nor provides means essential for putting the method into effect in the UK.
200. I am going to use the following claim breakdowns provided to me early in the trial by Optis, and not objected to by Apple, which show the proposed amendments. For some reason the breakdowns use different letters for claim features of 810 claim 1 from the version exhibited to Mr Bradford’s evidence, which was only pointed out to me at the stage of correcting my judgment when it was not sensible to change back. The main difference, which has no impact on my reasoning, is that in the version given to me at trial feature 1[k] from Mr Bradford’s version was split into two. Claim 1 of 549 is as follows:


201. Claim 7 is as follows, and requires that the third spreading unit (for the blockwise code used for ACK/NACKs) uses a sequence of length 4:
![]()
202. Claim 8 is as follows and requires an unused cyclic shift before as well as after a CQI:

203. Claim 1 of 810 is as follows (and the additional issue raised by it depends on integers 1[b] and the opening part of integer 1[l]):


![]()
204. Claim 2 of 810 adds to claim 1 the same feature as that of claim 8 of 549.
Teaching of the Patents
205. The claims of the Patents are verbose and the language of the specification is not always easy either. I hope it will assist understanding of this judgment if I give a relatively high-level summary of the invention of claim 1 of 549. This is not a substitute for the claims themselves or an attempt to cover all of the teaching of the specification.
High level summary
206. Claim 1 of 549 is to a “mobile station”; I am going to stick to “mobile”.
207. The mobile has to be able to spread and transmit ACK/NACK and CQI signals (although it will not do both at once).
208. The mobile will spread and transmit its ACK/NACK and CQI signals in accordance with a “code multiplexing structure” (I will use the abbreviation “CMS” from here on). I return to this concept in more detail below, but for present purposes I refer to Figure 10:
209. This grid structure indicates where mobiles of the Patents are to put their ACK/NACKs and CQI signals. This grid will accommodate multiple mobiles, hence “multiplexing”.
210. An ACK/NACK is spread in the horizontal direction according to a ZC/CAZAC cyclic shift, and there are twelve options for that. It is also spread in the vertical direction according to a Walsh sequence. There are three options for that. The claims use generic functional language instead of ZC/CAZAC/Walsh, but I will use the latter as I think it is more understandable.
211. A CQI is only spread in the horizontal direction. It is not spread with the Walsh sequence.
212. Claim 1 of 549 calls for a checkerboard or mesh pattern of the general kind shown in Figure 10, which has what the claims call a “2-cyclic shift interval”. That refers to the fact that e.g. the square denoted CCE #1 with Walsh sequence 0 is 2 cyclic shifts from the next time that Walsh sequence 0 is used, which is at CCE #2.
213. Where a CQI is multiplexed (shown at ZC sequence 3 in Figure 10) it will “occupy” the whole of a vertical column because it is not spread with a Walsh code, and it is required that the cyclic shift following a CQI is not used; it is empty (ZC sequence 4 in figure 10). This is intended to prevent the CQI from interfering with a following ACK/NACK in the event of delay shift.
214. Figures such as figure 10 can be confusing at first (though not once the specification has been read) because they do not show the CQI “occupying” the whole of a column, and they do not show the empty cyclic shift that follows as blank. A clearer form of notation is the following, used by Mr Edwards in relation to where he said (and Optis disputes) the skilled person would get to from the Nokia prior art; it must be noted that the orientation is different (CAZAC on the vertical axis, Walsh code on the horizontal):
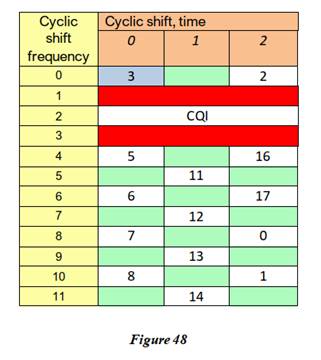
215. The cumbersome way that claim 1 of 549 describes all this is by reference to the mobile station having three spreading units (features 1[b], 1[c] and 1[d]) and three control units (1[e], 1[f] and 1[g]), one for each spreading unit. It then, in the characterising portion, describes the cyclic shift pattern at features 1[i], 1[j] and 1[l]. And it describes the unused cyclic shift in features 1[k], 1[n] and 1[o].
216. Other features do not call for separate comment in understanding the general pattern of the claim (e.g. 1[h] requires a transmitter and 1[m] says that CQIs are not spread with the Walsh codes).
217. Claim 7 of 549 says that the orthogonal sequence of the Walsh spreading code is a sequence of length 4. So in combination with claim 1 that means there are three spreading codes of length 4. This has some relevance to the Nokia prior art and to the added matter issue.
218. Claim 8 requires an unused cyclic shift before a CQI, as well as after.
219. Turning to claim 1 of 810, the broad structure is the same, but there is an additional requirement, found in features 1[b] and 1[l]. 1[b] requires a receiver that is configured to receive control information on a control channel element or CCE and feature 1[l] says that the CCE “is associated with” a PUCCH that determines the relevant cyclic shift for the mobile station. So this relates the CCE(s) on the downlink to the part of the mesh the mobile should multiplex its ACK/NACK or CQI into. The detail of what this requires is disputed. Optis reads it more narrowly and Apple reads it more broadly.
Teaching of the specification in more detail
220. The specification in this case has (as is normal) a section on the Background Art, and contains various statements as to what is “conventional”. An issue before me was the significance of these matters when it comes to assessing the CGK.
221. Apple referred to EPC rule 42. It says that the description shall inter alia:
(b) indicate the background art which, as far as is known to the applicant, can be regarded as useful to understand the invention, draw up the European search report and examine the European patent application, and, preferably, cite the documents reflecting such art;
222. This is not a requirement as to identifying CGK. The Guidelines for Examination in the European Patent Office, Part F, s4.3, to which Apple also referred, begins:
The description should also mention any background art of which the applicant is aware, and which can be regarded as useful for understanding the invention and its relationship to the prior art…
223. It also says that “the applicant should cite in the description the closest prior art known to him”. That may or may not be the closest prior art that actually exists, and it may well not be CGK.
224. This section of the Guidelines goes on to say:
The applicant may cite documents in the application which relate to standard technical knowledge (background art neither addressing the same technical problem nor necessary to complete the disclosure of the claimed invention).
225. The overall effect of this is that it cannot be assumed that simply by including something in the Background Art section the author of a patent specification is saying that it is CGK. The specific phrasing used could convey that that was the author’s belief, but that is different.
226. Counsel for Optis submitted that even if a specification did, on a proper full reading, say something was CGK then that was not conclusive. Counsel for Apple accepted this and said that such a statement in the specification would be a relevant consideration, something to take into account. I agree, but in the present case I have very full evidence from two experts and many contemporaneous documents to work from, so I do not think parsing individual statements in the specification to see if they are potentially about what was CGK rather than what was known from prior art documents is at all likely to help. And I do not believe Apple, in any event, was able to point to anything that was a clear statement as to CGK.
227. A related submission by Apple focused on the fact that the specification of 549 says that a number of code multiplexing structures were “conventional”. The most useful of these for Apple would be figure 6 or figure 7, and:
i) Apple said that the reference to figure 6 in [0011] in a discussion of Nokia implied that Nokia disclosed figure 6. This submission does not work, since the opening description in [0011], speaking of Nokia, refers to using 6 ZC shifts and figure 6 uses all 12. So it seems that when figure 6 is introduced, the author has moved on from Nokia. If the specification did say that Nokia disclosed figure 6, it would be wrong.
ii) Apple relied on figure 7 being called “conventional” as showing that it was in the prior art (I think Nokia), or the CGK. But when I asked where, Counsel for Apple could not say, because it is not even alleged to be in the CGK and is not in any of the prior art cited or known to Apple (since otherwise it would certainly have been cited).
228. Why the authors made such mistakes as they did in describing the relationship of the figures to the prior art is impossible to know in this case. Mistakes are not to be encouraged but nor are they a reason to treat something as being the case when it is not.
229. The “Background Art” section of the specification begins at [0002] with a general description of ARQ, ACK/NACKs and their transmission on an uplink channel, the example of which given is the PUCCH, which the skilled person would understand referred to LTE. At [0003] and [0004] there is then a description of the sending of CCEs on downlink control channels (these are referred to as L1/L2CCH channels, which the skilled person would relate to the PDCCH in LTE), and a mapping of CCEs to the PUCCH.
230. [0005] describes the use for spreading of ZC and Walsh sequences by reference to figure 1 and says that with 12 ZC sequences and Walsh sequences of length 4, it would be possible to multiplex a maximum of 48 mobile stations. At [0006] and [0007] the specification introduces inter-code interference in the time domain and, with specific reference to LTE, CQIs and the fact that they are not spread with Walsh codes.
231. At [0009] and [0010] the specification introduces delay shift interference and says that a previous approach to it has been to use only 6 of the twelve ZC sequences, which means that only 24 mobile stations can be multiplexed.
232. [0011] then discusses the Nokia prior art by reference to figure 6. I have addressed this above. The last sentence of [0011] says that interference between Walsh sequences #0 and #2 is extremely unlikely. This is not very clear but may relate to a realisation which was becoming more well known around the priority date, but was not CGK, that not all Walsh codes interfered equally. Counsel for Optis realistically accepted that he could not submit that the reader of the Patent would appreciate that that is what it was saying.
233. After paragraph [0011] there is a section called “Disclosure of Invention” and an immediate sub-heading “Problems to be Solved by the Invention”. This takes figure 6 and adds a multiplexed CQI, giving what is called a “mixed resource block”, shown in figure 7:
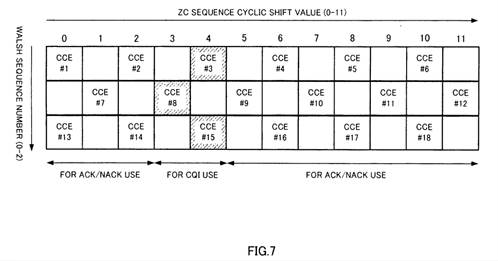
234. The specification says that this is “conventional”. As I have said already, Apple relies on that as an admission; Optis says that it is incorrect. In any event, the specification says that a CQI at ZC sequence 4 may cause interference with the following ACK/NACK at ZC sequence 5. It is the objective of the Patents to “suppress inter-code interference between an ACK/NACK signal and CQI signal that are code-multiplexed” - see [0013]. Essentially the same objective is stated at [0015].
235. There follows the list of figures at [0016]. Some of these are described as conventional, including, as I have said, figure 7.
236. There are three embodiments. They can be understood from figures 10, 11, 12, 13 and 14. I have already reproduced figure 10 above. Figures 11 to 13 do not call for separate comment other than to say that figure 13 shows having an unused cyclic shift before and after the CQI.
237. Figure 14 shows the third embodiment; this is outside the claims I have to consider because it has a cyclic shift spacing greater than 2. This gives rise to a detailed point on interpretation hinging on how figure 14 is described in [0069], and I will address that in relation to claim interpretation, below.
Issues of claim interpretation
238. There were two issues of claim interpretation.
239. The first relates to the claim features requiring that the apparatus be “adapted to spread and transmit … in accordance with a code-multiplexing structure”.
240. The second concerns “CCE associated with a PUCCH” and goes to the obviousness of 810.
“Code multiplexing structure”
241. This term is sought to be introduced by amendment. It does not have direct textual basis in the specification. Its introduction is opposed by Apple on grounds of lack of clarity. However, Apple does not oppose it on the basis of added matter. I think that is correct, because the concept which it describes is plainly taught in the specification, albeit that, perhaps oddly, there is not a convenient expression for it.
242. Apple submitted that the CMS is an “abstract logical structure known to the network”. I agree. It is plainly not a physical thing. It sets up a logical pattern of cyclic shifts and orthogonal sequence numbers by which the network dictates exactly where mobiles can multiplex ACK/NACKs and CQIs in a resource block.
243. Thus, in essence, figure 10 and those like it depict CMSs. This fits with the introductory words of feature 1[a] and with the way in which various things are said to be “in” the CMS in features 1[l] to 1[o]. One could perhaps think of the CMS as a map or a set of rules.
244. Optis submitted that the CMS must also be present in the mobile, or is a feature of the mobile. I do not accept this. The mobile must of course be adapted to spread and transmit “in accordance with” the CMS. A mobile which was programmed to put ACK/NACKs or CQIs in places that the CMS did not permit would not be so “adapted” and would be outside the claim. It also would not work. But that does not mean that the mobile has to have a copy of the CMS; it might have some simple procedural code which ensured compliance without “having” the whole “map”. Optis’ fallback position was that the base station and the mobile must work to a common understanding; this is of course the case as I have just said.
245. There are two further nuances which come into the arguments on infringement and on Nokia:
i) There is nothing in the claim to say that the mobile has to use the same CMS all the time, or can only be adapted to work with one. Although not really gone into in the evidence, this was a feature of the argument, since LTE allows a variety of CMSs. So far as it matters, I consider that since the CMS of the claims is intended to deal with interference, the skilled person would understand that it would be used when the network apprehended that there was a risk of interference and also that it was appropriate to multiplex ACK/NACKs and CQIs in the same resource block. At other times a different CMS could be used. A mobile would in practice need to be adapted to work with that too.
ii) Counsel for Apple submitted that the CMS is only that part of the 12x3 grid actually in use at any given moment. Hence, when the network scheduled only six mobiles the CMS in figure 13 would not include the code combinations for ACK/NACKs momentarily unused. I reject this. It is inconsistent with, for example, the indication in the figures that certain ZC cyclic shifts are “for ACK/NACK use”, with the language in feature 1[l] “for spreading” ACK/NACK signals, and with the general approach that the grids in the figures are complete maps of what to do and not to do.
246. Having explained what the CMS of the claim is, I move on to the central issue on infringement, which is whether the claim requires the CMS actually to be in existence for a mobile to fall within it (Apple’s position), or only that the mobile is “adapted”, i.e. suitable, to work with a CMS if and when there is a CMS, i.e. when the network creates or implements it (Optis’ position). This is partly a question of law, which I deal with in relation to infringement below, and where I accept Optis’ argument that “adapted” conventionally means suitable. However, Apple fortified its arguments by reference to aspects of the specification and the Patents, and I will deal with those here.
Apple’s six reasons
247. Apple advances six reasons in support of its position on this.
248. The first is that it contends the nature of the invention supports it. Apple says the Patents are about the coordinated use of uplink code resources by multiple mobiles. I agree with this so far as it goes, if one is looking for a very high level summary of the Patents, but it does not mean that all the claims have to be limited accordingly. Apple goes on to contend that such an invention would be more naturally protected by a claim to the base station, or by a method claim. I agree that those would be obvious options for a patentee, and indeed Optis has taken them (although those claims are not alleged to be infringed). But it does not follow that a claim to a mobile station should be construed to have identical scope. Claim 1 of the Patents is to a mobile station and it uses the well-accepted drafting approach of “adapted”. This point by Apple provides no reason for an unusually restricted approach to “adapted”.
249. The second is the contention that the only differences between the base station and the UE of the invention according to the different embodiments are in the processing in the base station. This is another way of deploying the alleged problem with [0069] that I have dealt with in relation to clarity below, and an assertion that Optis must contend that that paragraph is “wrong”. I refer to what I say in that context. It is true that mobiles operating in accordance with the different embodiments will differ little from each other, and that a mobile which can only operate according to the third embodiment will not infringe, because it will not be adapted to work with a CMS with a 2-cyclic-shift spacing. But again, this does not affect the fact that “adapted to” means merely suitable.
250. The third relies on the wording of integer 1[a], in particular “adapted to” and “code multiplexing structure”. As for “adapted to”, I have dealt with that in relation to the law below in connection with infringement. As to “code multiplexing structure” I have dealt with that above and agreed with Apple that it is a logical structure created in the network; a set of rules, in effect. Putting these two features together means that the mobile has to be adapted, i.e. suitable, to work with that structure, if such a structure is present. So I am unable to follow why this argument does not simply amount to saying that “adapted to” has a meaning in the context of the Patents different from the conventional one. I cannot see why it needs to.
251. The fourth is that the characterising integers of the claim use the words “uses” and “is not used” when referring to cyclic shift values. Apple says that these uses of the present tense with no sense of conditionality mean that the cyclic shifts must actually be used; it says that “adapted to” is not carried into the characterising integers. I reject this; it is just a lawyer’s point. The “uses” phrasing can perfectly well be understood to refer to what will happen if and when the mobile station actually spreads and transmits an ACK/NACK signal.
252. The fifth is that Optis’ construction would lead to invalidity. This is because, Apple says, of its alternative case (anticipation) over Nokia. But such potential invalidity is not at all apparent from the Patents and is therefore not a reasonable or even possible guide to the interpretation of the claims. Of course it is plain that an “adapted to” product claim, if it means “suitable for”, is generally more vulnerable to prior art than a method claim actually requiring the thing in question to be done, but that does not cast doubt on the intention behind the drafting. In any event, Optis accepts that the claim is broader in this sense, and I have rejected the alternative case over Nokia on the basis of it.
253. The sixth is that Optis’ construction lacks clarity. I deal with the clarity objection below and reject it.
CCE associated with a … PUCCH
254. This is part of feature 1[l] of 810. The issue is as follows.
255. There was no dispute at trial that it was CGK that downlink control information would be carried on a downlink control channel which would be divided into CCEs. This is the basis on which claim 1 of 810 proceeds, by virtue of feature 1[b], “a receiver configured to receive control channel information on a control channel element CCE”.
256. The downlink control for each mobile is referred to in the Patents’ specification as the “L1/L2CCH”, which is also frequently referred to as the PDCCH. There are multiple L1/L2CCHs, and each mobile is assigned one (see [0003]).
257. Then feature 1[l] says that “the CCE is associated with a physical uplink control channel, PUCCH, and the PUCCH is determinative of a cyclic shift value”.
258. The parties agree that this all describes an implicit signalling scheme. In other words the network does not explicitly or distinctly tell the mobile where to put its ACK/NACK or CQI among the options available in the code multiplexing structure, but the mobile works it out by implication from something else sent on the downlink control channel.
259. The downlink control channel for a mobile might consist of more than one CCE, and it was for the network to decide at any point in time, based on network conditions and especially channel conditions for a given mobile, how many CCEs to use for each mobile’s L1/L2CCH. This was CGK, as described above.
260. This means that the CCE number(s) for a given mobile will not necessarily match the number of the L1/L2CCH for it.
261. Optis contends that feature 1[l] of 810 requires specifically that the CCE number must be used for implicit signalling of the cyclic shift value; using the L1/L2CCH number is not within the claim. Apple on the other hand contends that the claim covers both, by using general language.
262. Relevant parts of the specification are paragraphs [0011], [0024]-[0027], [0049], and [0056]-[0059]. Thus where there is a mapping to give effect to implicit signalling of the kind referred to above it is from the CCE to the uplink PUCCH resource. There is reference to the numbering of downlink control channels, at [0023], but not to their being used to denote or imply the uplink PUCCH resource to be used. Although this favours Optis, it cannot be pressed too far because most of the references come from the description of the preferred embodiments, so the argument has a flavour of saying that claim language must be limited (in this respect, at least) to the preferred embodiments, which is not legitimate. While that cannot be said of [0011], which is in the general teaching, that paragraph is not as clear as it might be given that it is a paragraph dealing with Nokia, and the problem over the Patents treating Figure 6 as being “conventional”, to which I refer above. Nonetheless, it clearly calls out mapping CCE numbers to PUCCH allocations, and that is how Mr Edwards understood it; he also accepted that the only way that the Patents taught that the mobile could determine its PUCCH resource was by looking at its CCE number.
263. The CGK status of the Kobe agreement is also relevant to this argument. I have concluded above that it was CGK and that it was to the specific effect that the control channel index would be used for implicit signalling. This helps Optis; the reader would have the impression that the patentee was proposing a different approach.
264. Apple’s position is that any implicit signalling would do, but in my view the language is clearly not as general as that.
265. Apple also submits using the downlink control channel number falls within the language of the claim because there will necessarily be an association from the CCE number to the downlink control channel number. That this is incorrect was made clear in the cross-examination of Mr Edwards, when the following notional example was put:
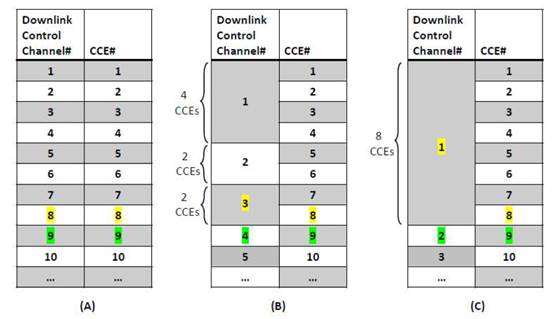
266. What one can see from this is that there is no necessary mapping from a CCE to a downlink control channel number. The same CCE can be in different downlink control channels depending on the aggregation.
267. Apple’s final effort was that the feature includes the use of downlink control channel numbers simply because downlink control channels are made up of CCEs. I reject this because it is so plainly not what the claim feature says.
268. I therefore conclude that Optis is right about the feature; the CCE itself must be used for the implicit signalling.
Infringement/essentiality
269. The issue concerned, expressing it a high level for now, the treatment of functionality which is required by the relevant standard but which the network operators are free to decide not to use, and do not use.
270. The issue arises in the context of claims which are product claims to mobile stations. The Patents include method claims but as I said above, Optis does not allege infringement of them.
The facts
271. There is no dispute about the following facts.
272. The relevant standard is intricate, and it is enough to say that there is parameter called Ncs(1). A condition for there to be a MRB is that Ncs(1) > 0.
273. As already mentioned, Apple led evidence from Mr Rowsell of Metricell that he measured the relevant control signals sent by UK networks. In particular, he did drive tests and found that the parameter Ncs(1) was always set to zero by all UK networks. This evidence was not challenged by Optis and it means that the UEs will not send MRBs in the UK. Apple’s position through Mr Edwards was that it will never make sense for UK networks to use MRBs because they only make sense for bandwidths narrower than 5MHz, which have never been deployed in the UK. Mr Edwards also suggested that there has been only limited use of the relevant narrower bandwidth elsewhere in Europe. This was not challenged.
274. None of this means that LTE-compliant UEs as sold by Apple in the UK cannot send MRBs; they could if they received the right signalling, as explained below. They have to support MRBs, for example in case they roam. Mr Bradford also explained in his evidence that the functionality is required to be present in mobiles for them to pass LTE conformance testing, i.e. for them to be regarded as standards-compliant.
275. In the agreed statement of technical issues relevant to essentiality, the following examples of MRB configurations were given:
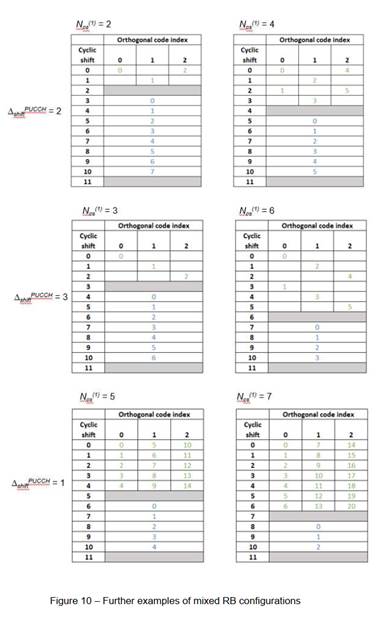
276. Here, the Ncs(1) is given above each example. The other parameter given is ![]() , which is the cyclic shift spacing. For the top right example where Ncs(1) = 4 and
, which is the cyclic shift spacing. For the top right example where Ncs(1) = 4 and ![]() = 2, the ACK/NACKs will go in the resources numbered 1 to 5 in green, in cyclic shifts 0 to 3, and the UE will work out which one is for it. Other parameters that I need not go into dictate the unused cyclic shifts 6 and 11 and the CQIs in cyclic shifts 7 to 10, numbered 0 to 5 in blue. The UE has programming that will process this all correctly.
= 2, the ACK/NACKs will go in the resources numbered 1 to 5 in green, in cyclic shifts 0 to 3, and the UE will work out which one is for it. Other parameters that I need not go into dictate the unused cyclic shifts 6 and 11 and the CQIs in cyclic shifts 7 to 10, numbered 0 to 5 in blue. The UE has programming that will process this all correctly.
277. On the basis of the construction I have arrived at, the top right example is a code multiplexing structure within the claims of the Patents. The examples with different values for ![]() do not fall within the claims because they have the wrong cyclic shift spacing. Each of them is a CMS, however and an LTE-compliant mobile will have to be able to work with all of them. Apple made an argument that the six examples all ought to be aggregated in some way to work out what “the” CMS is, with the result that the CMS allows all possible resources to be used for ACK/NACKs. In that case, Apple said, there is no infringement because there is no longer a 2-cyclic-shift mesh structure.
do not fall within the claims because they have the wrong cyclic shift spacing. Each of them is a CMS, however and an LTE-compliant mobile will have to be able to work with all of them. Apple made an argument that the six examples all ought to be aggregated in some way to work out what “the” CMS is, with the result that the CMS allows all possible resources to be used for ACK/NACKs. In that case, Apple said, there is no infringement because there is no longer a 2-cyclic-shift mesh structure.
278. I reject this on the basis of my finding as to what CMS means. Apple made the argument in attempt to exploit the fact that Optis contended that in a CMS where only a few UEs were being scheduled at a given point in time (e.g. if just 0 and 1 for ACK/NACKs were in use in the top right example because channel conditions and demand led the network to schedule that way), then nonetheless the CMS remained the whole of that example, including positions 2 to 5 for ACK/NACKs. So Apple’s argument was that if one has to consider the position over time, one has to consider all the examples. This is a false equivalence. One has to consider the rules that an individual CMS implies over time, not how a mobile will behave over time when it is using multiple different CMSs.
Legal principles
279. The parties disagreed about the proper legal approach to this kind of situation. Their disagreement was partly reflected in claim interpretation, which I have addressed already, and partly more general.
280. The issue concerned “adapted to” claims. Apple referred to IPCom v Vodafone [2021] EWCA Civ 205, at [110]-[117].
281. There, the claim in issue was a product claim to a base station. It required that the base station be “set up to send information signals with access threshold value and access class information as access authorisation data”. So the claim language was not precisely of the “adapted” form, but in my view it was to the same effect.
282. The base stations in the alleged infringement could not in normal operation send the required information; they would need reprogramming to do that.
283. Arnold LJ dealt with the issue in the following passage, which I quote in its entirety because it makes the facts clearer while capturing the steps in the Court’s reasoning:
"103. … claim language of the means plus function type, and I regard 'virtual body modelling apparatus' as an example of that type, is generally taken by the granting authority (the EPO) to be read as means suitable for carrying out the function. That is a good reason on its own to interpret such words in that way.
104. … The fact that a general purpose computer can be programmed to become a virtual body modelling apparatus does not mean that a general purpose computer is a virtual body modelling apparatus nor is it an apparatus suitable for virtual body modelling. It is not. If the right software was installed in the computer but the computer was switched off then that might well be apparatus suitable for virtual body modelling but that is a different point."
"I will start with direct infringement under s60(1). For this purpose I take it that a Wii system with a Balance Board [an item of hardware] running Island Cycling [game software] is an apparatus within claim 1. The pleadings include an allegation that sale of a Wii in the UK is sale of a product within claim 1. I reject that argument. A Wii console sold by Nintendo to customers is not, in the state it is sold, an apparatus within the claim 1. The game software is available on optical disks which are placed in the Wii console in order to play the game. To be within claim 1 it seems to me that the relevant disk, such as a disk carrying the Island Cycling software, at least has to have been inserted into the Wii unit and a Balance Board has to be connected. In that state, whether the unit is switched on or switched off, it seems to me that the claim is satisfied on the assumption I have made."
"225. … changing a base station from one which does not operate an infringing method … into one which does, is not as simple as choosing whether or not to supply power to it. Assume for the moment that the base station is not transmitting any barring parameters. Now assume that the operator wants to transmit the barring parameters for purposes of access control. The fact evidence established that making the change was not a simple matter of supplying power. On the contrary Vodafone's evidence shows that the change requires reprogramming the base station software.
226. IPCom submitted that the reprogramming was akin to flicking a switch. I disagree. I agree with IPCom that the extent of the reprogramming might vary between what Mr Bishop accepted was quite a trivial change (eg a change to the base station software which reads the configuration file, if one has the base station software source code) to a wholesale rewrite of the relevant software, but the fact remains that until the additional programming is done - however extensive or otherwise that additional programming is - the base station does not send the barring parameters. Nor is it adapted or configured to send them. On the contrary, it is adapted and configured not to send the barring parameters."
"… I accept that if the LTE network is in such a state that it merely needs power in order to operate access control as per section 5.3.3.11, then it is 'set up to send' and hence acts done in relation to that network will infringe unconditional claim 13. Unconditional claim 13 is only 'essential' when the network is in this state. Conversely if the LTE network requires some form of adaptation, configuration, or additional programming going beyond the mere supply of power then it is not 'set up to send' and acts done in relation to it will not infringe unconditional claim 13."
284. So the base stations were not “set up to” do things which would require reprogramming. This is a sensible approach to the language used and is also sound policy because if a system built around general purpose computers were “set up to” or “adapted to” do anything that could be achieved, even with reprogramming, then it would be extremely hard ever to achieve a valid product claim.
285. IPCom does not alter the general position that “adapted to” means “suitable for” in relation to means plus function claims of the kind in issue there and before me: the Court of Appeal referred to Birss J having said so, and it was not questioned. IPCom was really about a different point altogether - was a product “set up” or “adapted” for something that would require reprogramming before it could be achieved.
286. As I have said, the claim under consideration in IPCom (claim 7) was a product claim to the base station. In the present case, as I have also said, I am considering a product claim, to the mobile.
287. I agree that if reprogramming the Apple phones were required to achieve the result then they would not be so “adapted” - that is what IPCom decides. But it is not required. The phones have the necessary logic, albeit that it is never put into effect in the UK for the CMS on which Optis relies.
288. So overall taking into account the disclosure of the Patents and the general approach to “adapted to” claims, I conclude that the right approach to the claims of the Patents is to ask if the mobile, without reprogramming, would spread and send the ACK/NACK or CQI signal if a CMS as defined were present. But it is not necessary for the CMS in fact to be there.
289. An Apple phone would, without reprogramming, function properly in the example above where Ncs(1) = 4 and ![]() = 2, which represents, on my findings a CMS within the claims of the Patents. So there is infringement arising from compliance with the standard in this way, and the Patents are essential.
= 2, which represents, on my findings a CMS within the claims of the Patents. So there is infringement arising from compliance with the standard in this way, and the Patents are essential.
Validity over the prior art
290. I will address the main legal principles, then Panasonic, then Nokia. Nokia raises a discrete legal point which I will deal with there.
Legal principles - obviousness
291. At one level there was no dispute about the basic principles. As in other recent decisions I was referred to Actavis v. ICOS [2019] UKSC 15 at [52] - [73], with its endorsement at [62] of the statement of Kitchin J as he then was in Generics v. Lundbeck [2007] EWHC 1040 (Pat) at [72]. Apple relied, as it did in Trial C, on Brugger v. Medicaid [1996] RPC 635 at 661, approved by the Supreme Court in Actavis v. ICOS, to the effect that an obvious route is not made less obvious by the existence of other obvious routes. It played a lesser role in this trial.
292. Both sides put forward attempts to summarise and capture the inventive concept for the purpose of the Pozzoli analysis. This is legitimate in order to strip out unnecessary verbiage. Claim 1 of 549 is certainly long and wordy and stripping it back would be welcome, but as so often happens, the parties’ versions of the inventive concept were not neutral and quite different from one another. I have settled on the approach of listing the changes needed from each piece of prior art to reach the claims of the Patents, which is how the parties organised their written submissions. It is informed by and intended to reflect the claim features missing from the prior art, but not expressed by a list of feature numbers, because that would be so messy.
293. Optis reminded me about the importance of the Technograph principle that a stepwise approach to the gap between the prior art and a patent’s claims presents the danger of concealed hindsight and is illegitimate if it does so. I have borne this in mind and it is of some potential significance on both pieces of prior art.
Disclosure of Panasonic
294. Panasonic is a short (2-page) TDoc presented at RAN1 meeting #49bis in Orlando in June 2007, just before the priority date.
295. Its title is “Usage of Cyclic Shifts and block-wise spreading codes for Uplink ACK/NACK”.
296. In the introduction it points out the basic agreement for the use of ZC sequences and Walsh codes for multiplexing on the PUCCH.
297. It then refers to the Kobe agreement, but notes that management of persistently scheduled UEs’ ACK/NACK and the CQI are for further study. It says that “[o]ne possibility is to allocate separate radio resources to the uplink ACK/NACK for the persistently scheduled UEs and CQIs as shown in [4]”.
298. In the last paragraph of the introduction it refers to there having been discussion after the Kobe meeting of whether or not to use all the 12 ZC cyclic shifts “in e.g. different cells”. The authors write “In this contribution, we will show our preferences on how to utilize these cyclic shift values from the performance/complexity points of the view”.
299. In the first paragraph of the Discussion, the authors refer to the “current working assumption” being the use of “1 of 6” (out of 12) cyclic shifts within a LB (which means symbol) and “1 of 4 Block-wise spreading codes”. Since, however, the PUCCH RSs (reference symbols) are restricted to only 3 orthogonal covers, it points out that that means 18 simultaneous “usages” of cyclic shift/block-wise spreading codes, which Apple says would correspond to the following “striped” arrangement:
|
|
Block-wise spreading code w(i) | ||
|
Cyclic shift within a LB |
1 |
2 |
3 |
|
0 |
ACK/NACK#0 |
ACK/NACK#6 |
ACK/NACK#12 |
|
1 |
|
|
|
|
2 |
ACK/NACK#1 |
ACK/NACK#7 |
ACK/NACK#13 |
|
3 |
|
|
|
|
4 |
ACK/NACK#2 |
ACK/NACK#8 |
ACK/NACK#14 |
|
5 |
|
|
|
|
6 |
ACK/NACK#3 |
ACK/NACK#9 |
ACK/NACK#15 |
|
7 |
|
|
|
|
8 |
ACK/NACK#4 |
ACK/NACK#10 |
ACK/NACK#16 |
|
9 |
|
|
|
|
10 |
ACK/NACK#5 |
ACK/NACK#11 |
ACK/NACK#17 |
|
11 |
|
|
|
300. The document goes on to discuss moving to the arrangement of its Table 1:
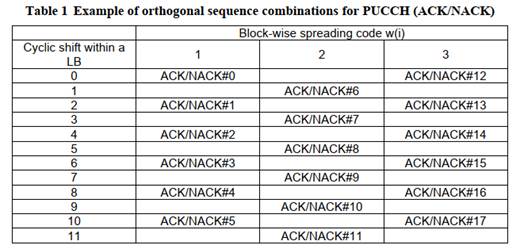
301. This uses all the cyclic shifts in the intra-cell situation, and the motivation for doing it is the observation reported in the paragraph beginning “Regarding a) …” that the orthogonality of the Walsh codes starts to break down with high speed UEs. The authors say that “We propose to investigate using different values of cyclic shifts within the cell for different Block-wise spreading codes”.
302. They go on to propose the way forwards in the conclusion:

Obviousness over Panasonic
303. I now turn to assess the argument of obviousness over Panasonic.
304. Although the parties did not express their submissions in terms of Pozzoli, I find it useful, subject to the point I made above about how to express question 3.
Pozzoli questions 1 and 2
305. I have addressed the skilled person and the CGK above. I am proceeding on the basis of the RAN1 skilled person, as I did in Trial C.
Pozzoli question 3
306. The disputed steps from Panasonic to claim 1 of 549 are:
i) Whether Panasonic discloses using three spreading codes for ACK/NACK data signals, or if not whether it was obvious;
ii) Using an MRB;
iii) Having an unused cyclic shift after a CQI.
307. Claim 1 of 810 introduces the additional feature of implicit signalling by the use of the CCEs.
Pozzoli question 4 - claim 1 of 549
308. I observe at a general level that Panasonic is just a discussion document; what Mr Edwards accepted was a “kick-off document”. It does not have any pointer to a clear way forward or even really as to what the investigators expected that they might find. What is proposed in the conclusion is primarily just to investigate, and a secondary matter (not really relied on by Apple) to define some tables or rules.
309. As Counsel for Apple submitted, and I accept, the mere fact that this is a document kicking off an investigation rather than a concrete proposal does not mean that it cannot render things obvious. But I find that in context it is a factor against obviousness.
Does Table 1 disclose using three spreading codes for data?
310. Apple contends that Table 1 discloses using three spreading codes for data (out of the four which were available in LTE at that time, as was CGK). As I understand it, Apple’s case was that it discloses three codes for reference signals and three codes for data.
311. Optis on the other hand contends that Table 1 is only addressed to reference signals.
312. I think the debate between the parties was polarised because it has arisen in litigation and the black-and-white positions taken are not reflective of the purpose of the document, or of Table 1. I think Table 1 is just there to illustrate that if one switches from the striped arrangement to the “staggered” one, all the shifts are used in a way which has only one or two Walsh codes per cyclic shift, potentially addressing the problem of Doppler with fast-moving UEs. It just is not asking itself the question “am I talking about reference signals or data”? As Counsel for Apple submits, that does not mean it may not render three codes for data obvious, but the argument does not start from the position that it discloses three codes for data.
313. Apple raised the following main matters:
i) Table 1 is not expressed to be limited to reference signals, and the rest of its teaching also covers data signals. This is true and means that Table 1 referring to data signals as well is not shut out. But it is not a driver in Apple’s favour, or at least not a strong one.
ii) A contention that Mr Bradford accepted that Table 1 could be understood as referring to using 3 out of 4 codes for data. I think his evidence read in totality (T2/225-228) was not to that effect.
iii) That the “current working assumption” was CGK and was the use of 3 out of 4 codes for data. I do not believe it was CGK and Apple did not point to any CGK source which could make it so (and reference to Panasonic itself, a TDoc, was obviously circular).
iv) There was no technical reason why the Table 1 allocation could not be applied to data. The fact that something could be done if thought of does not mean that it is being disclosed. This was no more than the absence of a negative - if using the allocation for data would have been seen or thought to be impossible that would tend to show Apple was wrong, but that was not a point Optis ran.
v) Mr Edwards stuck to his position. I agree; both experts did, and my function is to decide what the correct position is.
314. Optis relied on the following:
i) The CGK that in LTE ACK/NACK reference signals were going to be spread with length-3 spreading codes and ACK/NACK data signals with length-4 spreading codes.
ii) That the CGK is reiterated in Panasonic in the first sentence of the discussion.
iii) Panasonic does refer to limiting available cyclic shifts (albeit that it was proposing to move away from that) and does not refer to limiting available spreading codes.
iv) That being able to use all four spreading codes for data would cope with any Doppler problem better than just using three. I think Mr Edwards largely accepted that but in any event to the extent there was a disagreement I prefer the evidence of Mr Bradford.
v) A general principle in multiplexing to space out resources for users to minimise interference. Mr Edwards had drawn attention to this in his first report. Mr Edwards said this did not apply to Panasonic because the reader would think that Table 1 had already spaced resources enough. I agree with Counsel for Optis that there was no basis for this. Mr Edwards also said that perhaps the fourth code would be employed in a code-reuse scheme with other cells. There was no basis for this either and it was an instance of Mr Edwards speculating in a way which I think betrayed the use of some hindsight.
vi) Mr Bradford’s evidence that even if it was obvious to use only three codes in the striped arrangement, that did not apply if moving away from it.
vii) That no one else in the art suggested moving from a striped configuration to a configuration using only three codes for data. I found this point rather meaningless: no one else making the suggestion would not mean that Panasonic did not make it, and Optis’ position was that the striped configuration was not CGK anyway, so the art would not have been considering moving away from it.
viii) That whenever those in the art made suggestions for using three out of four codes, they used depictions or notations to make that explicit. This is not a tremendously strong point; it did not amount to saying that there was a convention in the field. But I agree with the premise that when it was clearly intended to use only three codes, it was shown. There were a number of documents of this kind. Their assessment is complicated by the fact that a number of them came from a point in time when it had been identified that not all Walsh code combinations interfered equally, so there was benefit in choosing the least-interfering combinations (see my comments in relation to [0011] in the Patents). But this was not CGK or available for the interpretation of Panasonic. So in relation to those documents, I find that Optis is right and there was something in the depiction or notation to make it clear that only three out of four codes were to be used. While not powerful on its own, this point draws strength from the point about spacing resources where possible: a reader would expect that if a document was intending to limit resource usage, it would say so.
ix) A particular document by ETRI. I reject Optis’ reliance on this, since it is a proposal made in the light of Nokia and Panasonic together and it is not possible to disentangle them. It is consistent with Optis’ general approach that the natural way forward would be to use all 4 codes for data, and that Nokia (which I deal with separately) would be progressed by tweaking the use of a scheme with 4 codes for data, but it does not help with specifically what would be done starting from Panasonic or Nokia alone.
315. There was some suggestion in evidence from Mr Edwards that using three codes for data would allow the same signalling to be used for data as for reference signals. But this was a bad point because in each case the signalling needed would just be a number from (say) 1 to 18 which the UE would translate into a cyclic shift and code combination by using a look up table. So the signalling burden would be the same. Apple did not really rely on this in closing and to the extent it did, I reject it.
316. Taking all the matters in the round, I do not think that Table 1 is disclosed as being for data. As I have said above, I think it operates at a much more general level.
317. I still have to consider whether it would be obvious to use three out of four codes for data from Table 1. Many of the considerations are the same as for whether the idea is disclosed in the first place. Essentially, and drawing on that reasoning, I think that if the skilled person was not already told about using three out of four codes, there would be nothing to trip them into thinking of it themselves. They would be naturally inclined to think that the spreading factor for ACK/NACK data was four and that they would want to use all of the available code space to reduce interference where that was a danger.
Multiplexing ACK/NACK and CQI
318. I have held that MRBs were not CGK. So Apple must seek to rely on the disclosure of Panasonic itself. It pointed primarily to the sentence beginning “[o]ne possibility …” that I have quoted above.
319. Mr Bradford took the position that this would not teach multiplexing in the same resource block, or make it obvious. Apple relied on a passage from his cross-examination (T2/206) as conceding that it covered multiplexing in the same resource block. I understood him to concede no more than that if one had multiplexing in the same resource block in mind already, the broad sense of the words used could cover it. But he was not accepting that such multiplexing would come to mind.
320. Mr Edwards maintained in oral evidence that this sentence did disclose multiplexing in the same resource block, but as I read his oral evidence that was on the basis that the approach was CGK, which I have rejected. In any event, I reject the notion that the sentence teaches it.
321. Mr Edwards also pointed to, and Apple relies on, the cross-reference to [4], a May 2007 TDoc from a number of companies the first-named of which is NTT DoCoMo.
322. Optis said that it was not open to Apple to cross-refer to [4] given its stance on the cross-reference to Nokia 002 in Nokia (dealt with below). I disagree that there was any necessary tension in Apple’s stance, which was that there was a difference between what was obvious to look at and what the skilled person would inevitably consult. In any event, my own view is that the skilled person would look to references or not depending on the nature and phrasing of the citation, the title of the reference, and other factors. The title of [4] is not promising in relation to the treatment of CQIs since they are not mentioned, and if the skilled person did go to look, they would find that the document itself does not mention CQIs at all.
323. Nevertheless, Mr Bradford did seem to accept that it might be obvious to go to reference [4], so I will consider what would happen if the skilled person did so. Apple’s argument as put to Mr Bradford was that the skilled person would see there that the discussion in relation to persistent ACK/NACKs made clear that it would be preferable to use up all the cyclic shifts, and only when that was exhausted to consider using another resource block. By analogy, Apple said, the skilled person would reason that CQIs should be multiplexed with ACK/NACKs until it became impossible and only then should they be put in separate resource blocks. This is tenuous and artificial and smacks strongly of hindsight. I reject it as disclosing the relevant multiplexing of CQIs with ACK/NACKs and for the avoidance of doubt it is of no value to Apple in arguing for obviousness either.
324. So I reject the idea that either in itself or through reference [4] does Panasonic teach the necessary multiplexing. I have also found above that it was not CGK. Apple contends that even so it is obvious. That is clearly possible in principle. It is not only things that were specifically in the CGK that can be deployed as obvious solutions to problems confronting the skilled person.
325. Apple also points out that Optis does not say it would have been thought impossible or problematic to multiplex in the way required by 549. That is true, but it does not provide reasons to think of it in the first place, or any motivation for it.
326. The motivation pointed to by Mr Edwards was that the multiplexing would:
i) Be seen as beneficial in a narrow bandwidth case where there would only be 6 RBs in the uplink and in the downlink such that only one RB would be used for the PUCCH.
ii) Be seen as flexible.
327. Mr Bradford disagreed with both. There was extensive cross-examination of both experts on the former and none on the latter, which I found vague and unconvincing in any event.
328. As to the narrow bandwidth case, it faces the difficulty that I have found it was not CGK to use an odd number of resource block pairs, which was the starting point for Apple’s argument. Even if it had been, Counsel for Optis explored with Mr Edwards the practical realities of the approach. I thought that Mr Edwards had focused on a very fact-specific situation of low bandwidth without trying to carry through the concrete analysis to check that it would work as a whole. The same applied to his analysis of leaving an unused cyclic shift, which I deal with next. These were matters that were only put to him in cross-examination and not supported by explicit evidence from Mr Bradford, but Counsel is entitled to raise such a challenge and I found it convincing. Mr Edwards had not taken into account matters such as the reporting frequency for CQIs, and scheduling requests. Mr Edwards responded by proposing rather complicated ideas like changing the spreading factor for scheduling requests. This heightened my impression that his proposal had not been well thought through.
329. Counsel for Apple pointed out that the matters raised by Optis were at a much more detailed level than the Patents. This is true, but having run a case on motivation that specifically invoked a detailed starting point (low bandwidth) I think it is legitimate to test its consistency.
330. Apple also said that Optis did not contend that there was any technical difficulty in implementing MRBs once the idea had been had, and it said that Mr Bradford accepted that if the skilled person knew the use of MRBs was possible then it could be an obvious thing to consider doing in the context of Panasonic (although his answers were quite heavily caveated and he maintained his position about the practical problems with the narrow bandwidth case and on the issue about odd numbers of resource blocks). Neither of these can help if, as I have found, MRBs were not CGK and would not occur to the skilled person in the first place.
331. I therefore do not think a case for the obviousness of multiplexing CQIs and ACK/NACKs in the same resource block was made out by Apple.
Unused cyclic shift
332. Panasonic does not teach this. Apple said that it would be obvious; its specific proposal as advanced in the evidence of Mr Edwards was again the low-bandwidth situation, since it was necessary for Apple to say that both the multiplexing and the unused cyclic shift were obvious together. I have rejected the low bandwidth proposal for reasons given above. Its problems become more acute if one attempts to include an unused cyclic shift.
333. I also found it unconvincing for Apple to run a case that it was obvious to use all the cyclic shifts, Panasonic’s starting point for investigation, and then to reverse direction and propose not using one altogether, although admittedly if one has reached the stage of combining CQIs and ACK/NACKs in one resource block then the skilled person would realise that interference of a CQI with a following ACK/NACK could not be addressed by different Walsh codes (because the CQI would not be spread with the Walsh codes).
334. Optis also points out a further tension in Apple’s case, which is that in the narrow-bandwidth case it would be all the less intuitive to take the decision to just give up ¼ of the available code space by only using three of the four available codes.
335. Finally on this, Optis pointed out that although Mr Edwards had put in numerous TDocs with MRBs, none suggested an unused cyclic shift. His answer, given in the context of a specific such document from Samsung, was that the authors had not thought it through. This point favours Optis to some extent.
336. Overall, I reject Apple’s case on this point as well.
810 additional feature
337. This is the requirement as to the association of the CCE with a PUCCH.
338. I have held that the Kobe agreement was CGK, and indeed it is referred to in Panasonic in any event. I have held that the Kobe agreement meant, specifically, the use of the control channel index and not implicit signalling generally. I have also held that the claims of 810 do not extend to the use of the control channel index but require the use of the CCE itself.
339. On this basis, Panasonic does not disclose the additional feature of 810.
340. There is simply no pointer in Panasonic to using the CCE and nothing in the CGK to point the skilled person in that direction. In addition, this issue is at a greater level of detail than Panasonic attempts to engage with. So I hold that this is not obvious over Panasonic.
Overall assessment
341. Panasonic looks superficially strong because Table 1 resembles at a high level the figures of the Patents. But I think it is only superficial. The document is a high-level proposal to conduct investigations, not a disclosure that would be expected to lead directly to anything useful.
342. Apple’s case involves a particular view of Table 1 which I think is unrealistically narrow, followed by a number of further steps, each of which is problematic, for reasons given above. I think the attack suffers from both hindsight in general and an inappropriately Technograph stepwise analysis.
343. I have in mind that the Patents do not entirely solve some of the issues put in the way of obviousness over Panasonic by Optis. In particular, Optis argued, as I have said, that it would not be obvious to use three codes of length four because that would involve not using some of the available code space. Yet the Patents do not use that code space, either. While I have taken this into account as a relevant factor it is only chipping away at individual parts of the claim, and I think it is important that the Patents provide a simple and practical overall solution which addresses code space utilisation, interference and multiplexing.
Disclosure of Nokia
344. As I said above, there is a point of principle which I have to resolve in relation to the disclosure of Nokia.
345. Nokia identifies a number of cross-referenced documents, listed at [1] to [7] on page 6. The last reference is ‘[7] R1-073002, “ACK/NACK performance of high speed UEs”, NSN, Nokia’. Optis says that the skilled addressee would read this document, which was referred to as “Nokia 002” at trial, together with Nokia itself. If this were so it would potentially assist Optis, because Nokia 002 gives illustrations which lack the 2-cyclic-shift pattern of the claims of the Patents and contain “adjacencies” which, Optis argues, are inconsistent with the direction that Apple say the skilled person would take from Nokia itself. I assess this argument below.
346. This is therefore a situation where the usual dynamic is reversed and the patentee wants to enlarge the material available to the skilled addressee when working from the prior art.
347. The point of principle concerns the proper approach to deciding whether the two documents must be read together in the light of the legal construct that is the notional skilled person. Apple says that the right approach can be identified by comparing the tests for anticipation and obviousness: if the skilled person would inevitably read two documents together in the light of a cross-reference from one to the other, then that is how the Court must proceed, but if the skilled person might or might not, and it would merely be one obvious option to combine them, then the person attacking the patent can choose whether to run a combination, or just rely on one document on its own. Apple says that at most it would be obvious to read Nokia with Nokia 002, and it chooses not to do so but to run Nokia on its own, though it says it still wins if they are combined.
348. In assessing this, I think it is important to have regard to the basic principles of the ordinary skilled person. He or she has unlimited diligence but lacks all inventive capacity. However, this unlimited diligence cannot be used to legitimise any degree of work on chasing references from a given document; one cannot say that with unlimited patience a skilled person would read every reference and every reference in every reference, particularly not if it would then lead to considering all the possible combinations of documents so found. This would be bad policy, because it would allow combinations of documents to be deemed in the mind of the skilled person which were not obvious to make.
349. Also, Apple’s argument rather assumes that references in a document offer ways to progress that document, but they may or may not. They may just provide background information. So while I agree with Apple that there will be situations where references in a prior art document present a range of options for the skilled addressee and it is a matter of choice and hence in the realm of obviousness which if any to pursue, that is just one situation and there will be others. Furthermore, the skilled addressee cannot think about what to take from or do with a reference, or whether to give it further attention at all, without turning it up to at least consider it, or making a judgment about what it is likely to contain from the cross-reference itself.
350. I do not want to make a wide-ranging decision about the right approach to this kind of situation based on just the limited facts of this case, but in general I consider that the highly diligent skilled addressee will by definition consider turning up the references in a prior art citation to see what there is to see, at least if the citation makes it seem that the reference is likely to be directly relevant to the task in hand. They may immediately discard it, if that is what the uninventive person would do, for example if they can readily then see that it is not in fact relevant. They may have choices to make, which then engages the law of obviousness. Sometimes the citation itself might make it clear that the reference is not useful to the purposes they have under consideration.
351. In the present case, the facts strongly favour the conclusion that the skilled person would read Nokia 002. The title is suggestive of a high likelihood of relevance, it is from the same organisation as Nokia itself, and its serial number makes clear that it is very close in time. I am sure that the skilled person would (as opposed to might, or could, or it would be an obvious possibility) open it up to see, and once they did that it would be immediately apparent that it was a companion paper to Nokia itself. Some real people might just skim Nokia without looking at Nokia 002, for reasons of shortness of time or the like, or because a reading of Nokia itself did not catch their attention, but that is not in keeping with what the notional skilled person would do. I also draw some support for this conclusion from Mr Bradford’s evidence that there was a page limit for TDocs and cross-referencing was a way to try to get around it, but it is not necessary to my conclusion.
The disclosure in detail
352. I need to go through Nokia’s disclosure in some detail in the light of the points in dispute.
Section 1 - Introduction
353. Nokia starts by explaining that it is about code resource allocation for ACK/NACK signals on the PUCCH; resources used by UEs which have only ACK/NACK signals to be transmitted, and not uplink data or periodic CQI. UEs which did have uplink data would use the PUSCH; Nokia does not spell this out but it was CGK.
354. There is then reference to what had been decided at RAN1 48bis in Malta: the use of CAZAC sequences and block level spreading. It is explained that block level spreading will be with spreading factor of 3 for reference signals and 4 for data. There is no real dispute about this, but it feeds into the later sections on which the argument does focus.
355. There is then a statement that allocating the resources explicitly would not make sense and that implicit resource allocation should be used. The authors refer to the Kobe agreement, saying that “for non-persistent scheduling the ACK/NACK resource is linked to the index of the control channel used for (DL) scheduling”. This is an almost verbatim quote from the RAN1 minutes to which I have already referred, with just the addition of “(DL)”.
356. The authors say that they will present a signalling scheme which can be used to map implicit signalling onto physical resources in the PUCCH.
Section 2 - Utilisation of CDM resources of ACK/NACK resource
357. This section begins by saying that “Certain principles” should be applied when allocating CDM resources between different UEs; this is where reference [7] to Nokia 002 comes in. I note, in addition to what I have said above that what the authors are talking about when referencing Nokia 002 are the principles that are to be applied. This conveys that what is being touched on is of high importance and is an additional reason to look at the referenced document.
358. In the following two bullet points, two kinds of interference are mentioned: delay spread affecting neighbouring cyclic shifts in the CAZAC sequence, and Doppler spread causing problems with different block level codes in the same cyclic shift. These would be readily understood by the skilled person, even if not CGK. The second bullet point can seem a bit confusing in its reference to “block level CAZAC/Hadamard code”, but it is probably just an artefact of its not having been conclusively determined that Hadamard codes would be used, and the remaining slim possibility that CAZAC codes would be used in both frequency and time domains. For the purposes of the dispute before me, it can just be taken that the block level codes would be Hadamard.
359. Following on, it is explained that adjacent cyclic shifts in the frequency and time domain have the worst orthogonality problems. Although easy to understand in its own terms, this statement is part of an important dispute, which is whether the teaching is that adjacencies must be avoided or merely are undesirable but can be accommodated at least to some extent. That is one place where Nokia 002 comes in.
360. Nokia then says that only part of the code resources can be used, but that the unused code space can be utilised to improve orthogonality. It goes on to make proposals in the “Intra-cell” and “Inter-cell” contexts. I am going to focus on the intra-cell situation since that is where the arguments at trial were directed, and it is also the area of Nokia’s greater focus.
361. For the intra-cell situation, Nokia proposes two code allocation schemes in Table 1:
362. This is clearly about reference signals, indicated by the letters “RS” at the top left. It has a grid of CAZAC sequences and blockwise codes for 18 and for 12 resources. For the 12-resource case, the scheme achieves a situation where there is only one blockwise code used for each cyclic shift (versus either one or two for the 18-resource case). This would be understood to give better protection against Doppler problems, as I believe was common ground between the experts.
Section 3 - Configuration of implicit ACK/NACK resources
363. This section sets out the parameters which characterize an implicit ACK/NACK resource. In themselves these are not controversial, but I point out the spreading factors for RS blocks (3) and data blocks (4) as those come into the later debate. The parameters are either “static” or “semi-static”. I return to those characterisations below.
364. At the top of the third page, the authors say that while the signalling burden for one implicit resource is not too big, signalling them all would be substantial, and values are given, depending on how many resources are in use.
Section 4 - Proposed signalling scheme
365. In this section, the proposed implicit signalling scheme is explained by reference to Figure 1, which is as follows:
366. The parameters to be used are given, again split into static and semi-static. A particularly critical one for the arguments before me is “num_t_shift”, which is described as “number of cyclic shifts of block spreading code (e.g. 3 or 4)” (it should be noted that the first reference to num_t_shift is wrongly written as “num_f_shift”, but it was common ground that this was an obvious typo, as can be worked out from later usage of the right expression, including in the labels on Figure 1).
367. The semi-static parameters include in particular res_1st, which can be thought of as the starting position in the tables to which I will refer in a moment, and shift_diff, which is the gap between two resources in those tables. Impl_res is the implicitly signalled number in those tables, i.e. the number in each cell.
368. These parameters are used in the algorithm given on the next page to give allocations of the kinds shown in figure 3. There is no dispute about how the algorithm works to give the values shown.
369. Figure 3 is as follows:
A B C
370. These three tables were referred to in the evidence as A, B and C and so I have added those letters. num_t_shift and res_1st are given for each table. It is not spelled out, but is fairly easy to see, that shift_diff for A, B and C is 3, 2 and 4 respectively (as was common ground).
371. A major debate was whether A and B would be seen to be taught for data as well as reference signals; unlike Figure 2, there is no clarifying reference to “RS”.
372. Every cell in the Tables in figure 3 has a code allocated to it and so in principle could be used, but Apple says that this would not be done in practice because it would lead to “adjacencies” and unacceptable interference.
373. At the end of section 4 there is some teaching about “the situation when periodic CQI and ACK/NACK from different UEs are transmitted in the same RU”. It goes on to mention related additional signalling:

374. If used, allowed_t_shift means that only certain of the blockwise codes would be used for ACK/NACKS, and allowed_f_shift means that only certain CAZAC codes would be used for ACK/NACKs. In practical terms this means that rows or columns in the Tables of Figure 3 could be reserved for periodic CQI or ACK/NACKs.
375. The teaching is confusing because it is not clear if the word “periodic” qualifies only “CQI” or also “ACK/NACK”. Apple said the former and Optis said the latter. Optis submitted that periodic ACK/NACK would be ACK/NACK from UEs scheduled to expect downlink data periodically without explicit control signalling each time. Optis’ position makes more sense but the fact is that the teaching is just not very clear.
376. It is not in dispute, however, that this paragraph discloses multiplexing CQIs and ACK/NACKs in the same resource block.
Sections 5 and 6 - Benefits and Summary
377. Section 5 seeks to explain why the proposed scheme reduces signalling burden, giving maximum bit usages for its scheme, which are contrasted with the usage for explicit signalling. It is worth noting that the calculation of bit usage assumes a maximum of 36 UEs, which arises from only 36 reference signal resources being available.
378. Optimisation against intra and inter cell interference is also taught to be an advantage.
379. Nothing turns on the Summary, which is just a wrap-up. The Appendix deals with inter-cell orthogonality and is not relevant to the issues for me, either.
Nokia 002
380. Nokia 002 starts with a brief introduction which is not important to my analysis. Section 2 explains the effect of delay spread between different cyclic shifts of the CAZAC codes, and the effect of Doppler spread between different Hadamard codes. This is repetitive of Nokia.
381. Nokia 002 goes on to say that the “most straightforward way” to allocate resources is to use 6/12 (i.e. 6 out of 12) cyclic shifts and 4 block-wise codes, “(3 with the RSs)”. It goes on to depict this:
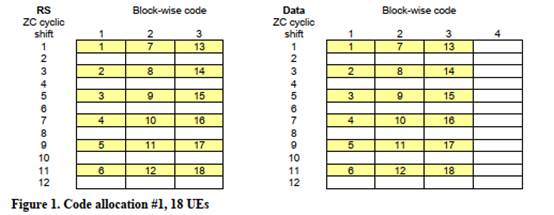
382. And explains that there will be significant interference between UEs with the same ZC shift. Since there are three UEs on each ZC cyclic shift in both parts of Figure 1, they are unsatisfactory. It is to be noted, since Optis relies on it, that in the Data part of Figure 1, it is spelled out that there are four Hadamard codes with one shown blank (differently from A and B in Figure 3 of Nokia).
383. At the bottom of the first page, Nokia 002 explains that much better performance can be achieved, and refers to Nokia (“[2]”). It shows code allocations for 18, 16 and 12 UEs arising from the application of Nokia:
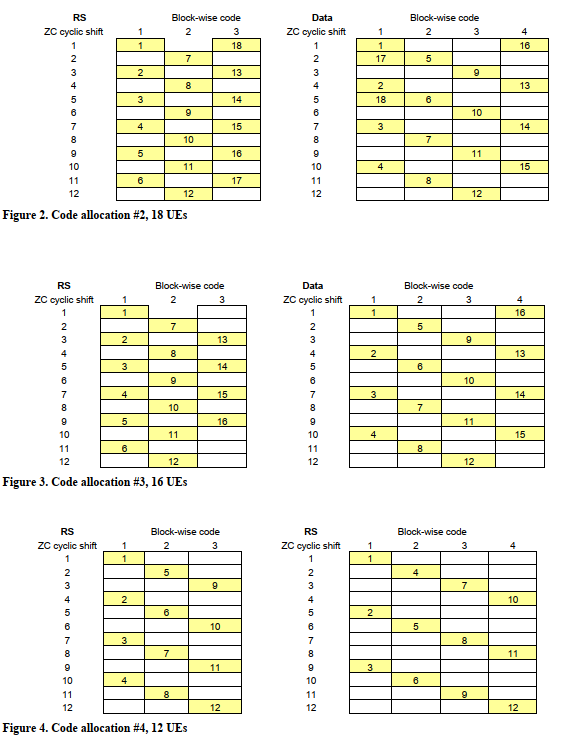
384. The right hand entry in the bottom row is mis-labelled; it should be “Data”, not “RS”.
385. In the Data part of the 18-user case it is possible to get an “adjacency”, since user 17 is on the same Walsh/Hadamard code and in an adjacent cyclic shift, compared with user 1 (and the same for users 2 and 18).
386. Section 3 includes “Simulations”, and these show that all the arrangements based on Nokia are better than the “most straightforward” case. Optis says this shows that a useful result can be achieved with some adjacency therefore being tolerated, and I agree. In other words, it shows that it is not essential to avoid adjacency. If more than 18 users were scheduled, there would be more adjacencies.
Does Nokia disclose using three Walsh codes for data?
387. I return to Nokia itself. It is the starting point of Apple’s case that Table B in Nokia would be understood to be suggested for data as well as for reference signals (Table B is critical to Apple’s case because it is said to be able to give a 2-cyclic-shift mesh and so be able to meet claim 1 of 549). Optis challenges this. It can be thought of (and Optis mainly argued it in this way) as whether num_t_shift is the number of blockwise codes in use, or the spreading factor. Apple said it was the former, and Optis the latter.
388. In my view, it is very clear that num_t_shift is the spreading factor. This is the natural reading of its definition in section 4 (the reference to “e.g. 3 or 4” is because it could be 3 or 4 depending on whether reference signal or data) and is reinforced by the way in which the spreading factor is described in the “Static parameters” of section 3. Apple seemed at one point to suggest that sections 3 and 4 were different schemes, at least in this respect, but I reject that. They go together, with section 3 addressing configuration of the resources and section 4 describing what is then done.
389. Furthermore, num_t_shift being the spreading factor is consistent with its being a static or constant parameter. Mr Edwards called it “hard-wired” in his first report and I agree that that is the first and clearest impression that one gains from the document. Mr Edwards developed a complex and different view in his later reports, which I found very artificial, that a change of num_t_shift might be signalled because while being constant in any given cell it might change from one cell to another. But not only is num_t_shift called “static” or “constant”, but in Figure 1 “Constant” parameters are distinguished from “Signalled” parameters, and num_t_shift is among the former, not the latter.
390. I note also that the other static parameter is num_f_shift, which is the number of cyclic shifts of CAZAC codes (12) and there was no suggestion from any quarter that that would need to be signalled, or change.
391. I recognise that Table B is not explicitly labelled as being data or reference signals. If it were labelled then this whole discussion would not have arisen. But the fact that the labelling is deficient in this respect is not a reason to give it the broadest meaning possible. The context still matters very much and it essentially all points to Table B being for reference signals.
392. Additional points are:
i) The reader is told on page 1 (which would be CGK anyway) that there were 36 possible code resources for reference signals and 48 for data.
ii) 48 resources being available for data means using all 4 blockwise codes.
iii) When referring to the signalling burden for ACK/NACK data in the last bullet point in section 3, reference is specifically made to 12*4 code channels.
iv) If num_t_shift is as Apple contends, it is unclear what allowed_t_shift adds.
393. Apple suggested that there would be no benefit in using all 4 blockwise codes for data, but I accept Mr Bradford’s evidence that it would allow the resources in use to be spread out more sparsely, with less adjacency.
394. I also think that for reasons similar to those considered above in relation to Panasonic, it would be expected that if the authors of Nokia had intended the use of only 3 out of 4 blockwise codes for data as a possibility, it would have been conveyed in a clearer and different notation.
395. Apple’s case on this can only get worse if Nokia 002 is also considered, given that it shows a blank code for data when only three out of four are in use, and given the depictions in Figures 2, 3 and 4. But this is unnecessary to my reasoning, since I am clear in my mind that Table B depicts reference signals only in the context of Nokia itself.
Steps from Nokia to the Patents
396. There are 2 steps to consider (the first could perhaps be split in two and the parties did so in their written submissions, but I think they overlap and are more conveniently addressed together):
i) Use of 3 codes for data with a 2-cyclic-shift gap.
ii) Having an unused cyclic shift.
3 codes for data and 2-cyclic-shift gap
397. I have held that Nokia does not disclose the use of 3 codes for data. Apple maintains that it would be obvious nonetheless to use table B for data. The reason put forward is that the skilled person would see that it allows a 2-cyclic-shift difference for up to 18 users with no adjacencies. It says that 18 users is a realistic practical limit.
398. For reasons given in my consideration of whether table B is disclosed as being for data, and for reasons given on the parallel point on Panasonic, I do not think that the skilled person would think that limiting the codes used for data down from a possible 4 to only 3 would be useful in this connection. Rather, they would think that the more room there was to space out the resources the less likely there was to be adjacency and interference.
399. It is true that the striped arrangement on the first page of Nokia 002 uses only three codes for data. This is again similar to the argument over Panasonic; Nokia deprecates the striped arrangement and the skilled person would not think that what Nokia proposes would include sticking to the use of 3 codes for data.
400. I move on to consider the 2-cyclic-shift gap issue. Nokia does not say that there should be a 2-cyclic-shift gap and indeed table B does not show any gaps at all. Apple’s case is that the 2-cyclic-shift gap would emerge if only 18 UEs were scheduled.
401. Given my interpretation of “code multiplexing structure”, the CMSs of Nokia are the whole grid of numbers from 1 to 36 or from 1 to 48, as the case may be, and not just that part of those numbers in use at any one moment depending on how many UEs are scheduled. For example, it would not be the case that the CMS of Table B would be just the single resource at res_1st = 30 if there were only one UE scheduled. Nor is the CMS of Table B the first 18 numbers when there are 18 UEs scheduled.
402. Additionally, I think there is hindsight in postulating that the skilled person would look at table B and mentally “shade in” just 18 UEs. Nokia clearly provides an algorithm which can allocate all the resources, and there is no reason to think that they would necessarily be allocated in the numerical sequence of Table B. This is connected to the point on 810 that I consider below - one has to consider what signalling would allow the use of precisely the 18 resources on which Apple focuses.
403. To the extent that Apple’s argument on this point is based on the premise that Nokia teaches that there must never be adjacencies, I reject it. Nokia says that they cause problems, but not that they must be avoided at all times, or can be. I acknowledge that this point is clearer and stronger for Optis if it can read in Nokia 002, but I accept it in relation to Nokia itself.
404. I therefore conclude that Nokia does not make it obvious to have a CMS with 3 blockwise codes for data, or a 2-cyclic shift gap.
Using an MRB and unused cyclic shifts
405. Optis accepts that multiplexing CQIs and ACK/NACKs from different UEs is disclosed in Nokia. So the issue on the parts of the claims of the Patents concerning CQIs is whether to have an unused cyclic shift after a CQI.
406. On this issue, therefore, Apple starts from a stronger position than in relation to Panasonic. But it still faces the question of what motivation there would be to multiplex in this way, and how it would be done. In relation to motivation and the details of putting things into effect, the position is essentially the same as in relation to Panasonic, and I reject Apple’s position for the same reasons as given there.
810
407. I have addressed above what 810 requires in terms of features 1[b] and 1[l] - the CCE number must be used to derive the PUCCH resource. For the same reasons as given in relation to Panasonic I consider that the reference to the Kobe agreement in Nokia is a reference to using the downlink control channel index and so does not satisfy the claims of 810.
408. Mr Edwards proposed the use of CCE numbers as being either disclosed in Nokia or obvious. Counsel for Optis explored in XX what this would mean. By reference to a document put in cross-examination (CXX/14) Mr Edwards was asked about the situation where the downlink control channel consisted of more than one CCE, as would be the case in bad channel conditions. I find that in such a situation, Nokia would not result in the tidy, symmetrical 2-cyclic-shift pattern with no adjacencies implied by Apple’s case from Table B (and this is further support for my rejection of that case). Instead, it would lead to the resources being rapidly used up (because higher resource numbers would be used, corresponding to the greater number of CCEs being used in this scenario), with adjacencies accumulating quickly. For example, the following example put to Mr Edwards shows an adjacency arising with the 6th UE:
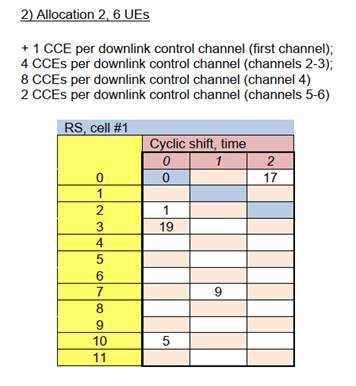
409. This is another example of Apple’s case being presented in a very abstract way, and coping inadequately with the detail that necessarily follows. I reject its obviousness case on this point.
Overall
410. Apple’s case over Nokia is very artificial. Its focus on Table B and its reading of that Table are both unrealistic and involve hindsight to look for something like the claims of the Patents. Unlike Panasonic, I do not think that there is even a superficial strength to Apple’s position over Nokia.
Apple’s alternative case over Nokia
411. I have held that the claims of the Patents do not require there to be a CMS, or for the mobile station to be used with it. They merely require the mobile station to be adapted to operate with a CMS as defined in the event that there is one. And “adapted” means able, without reprogramming.
412. It is on this basis, and only on this basis, that I have found infringement despite the fact that the relevant functionality is not ever used in the UK.
413. Optis accepted that the validity of the Patents must be tested against this broad scope. That means that if a UE operating as disclosed in Nokia could work with a CMS according to the claims of the Patent then the claims may be invalid (I say “may” because of the additional feature on 810). What the UE in Nokia is capable of doing can be inferred from the parameters signalled to it.
414. Apple has two attacks here.
415. The first is to set num_t_shift as 3, num_f_shift as 12, and shift_diff as 2.
416. The second is to set num_t_shift as 4, num_f_shift as 12 and shift_diff as 2, then use allowed_t_shift to prohibit use of the fourth block level code.
417. The first does not work because of my finding that num_t_shift is the spreading factor and not the number of codes used, but the second is possible.
418. Apple then says that it may postulate a limit on the number of UEs, which it sets as 18. Overall, this gives a situation like that in the RS entry for 18 UEs in Nokia 002, but which would also have a blank fourth column.
419. I agree that this (i.e. the second option but with 18 UEs scheduled at some time) is possible and a UE as disclosed in Nokia would be able to deal with it, but it is not a CMS within the meaning of the claims. There are three reasons:
i) As I have construed CMS it is the complete set of rules. The rules as disclosed in Nokia can populate all the resources in the grid. Its CMS is not a 2-cyclic-shift mesh; it cannot be because there are no gaps.
ii) Relatedly, with a limited number of UEs, the CMS is still the total set of resources.
iii) A 4th column dictated by the parameter allowed_t_shift as being unusable for scheduled ACK/NACKs would still be usable with ACK/NACKs (albeit they would be periodic ACK/NACKs). The CMS would therefore still provide for 4 blockwise codes for data.
420. Apple sought to evade some of those points, I think primarily the first, by pointing out that in the infringing devices according to the standard it is possible to use all the resources in the grid for ACK/NACKs. However, that is only possible if one looks at all the aggregate effect of all the resources covered by the possible scenarios set out above when I addressed infringement. In other words, it requires aggregating many different CMSs. No one CMS meets the claim. I rejected this approach when dealing with claim interpretation.
421. Had I been wrong about those points, the CQI features of the claims (multiplexing, unused cyclic shift after a CQI or before and after) would have to be considered. A UE according to Nokia has to be able to deal (or at least it is obvious to make it able to deal) with multiplexing CQIs and ACK/NACKs in the same resource block given the teaching in section 4, and the parameter allowed_f_shift which the UE has to be able to process could be used to reserve e.g. 3 cyclic shifts for CQIs, preventing their use for implicit ACK/NACKs. But there is no parameter that makes it possible to tell the UE not to use all of those for CQIs. There is no parameter to ensure a completely unused cyclic shift.
422. So the alternative argument fails against 549.
423. I did not understand Apple to argue that the alternative argument could allow it to succeed on 810 if it otherwise failed.
Claim 8 of 549 and claim 2 of 810
424. Although it does not arise, I would have held that if claim 1 of 549 was obvious then so was claim 8 (an empty cyclic shift each side of a CQI). If the skilled person had got to claim 1 and the view that an empty cyclic shift was useful to prevent delay spread, then there would not be anything inventive in having one before as well as one after. There was little argument about this, but I think Mr Bradford’s oral evidence justifies this conclusion.
425. Likewise, if claim 1 of 810 were obvious then so would claim 2 be.
Insufficiency
426. As I have said above, this was run only as a squeeze against obviousness and played no real part at trial.
Objections to amendment
427. As I have already mentioned, Optis’ amendments are sought unconditionally, so if they are refused 549 and/or 810 must be revoked.
428. The objections are as follows:
i) Lack of clarity. This boiled down to a single point which Apple runs as a squeeze - it says that if it is right about claim interpretation then the claims are clear.
ii) A point on added matter. It has two slightly different facets, the first of which runs against all the claims of the Patents and the second of which runs against claim 7 of 549.
Clarity
429. The objection is directed to the CMS feature.
430. As to the law, Apple said that the test was that set out by Neuberger LJ (as he then was) in LG Philips v Tatung [2006] EWCA Civ 1774 at [20] - the claim “needs to be as clear as the subject matter reasonably admits of”. I accept this; it means that perfect clarity is not required.
431. Apple’s main clarity objection was conditional - that it was not clear whether the CMS was a network feature or a feature of the mobile. It said there was a lack of clarity if its position on that was not accepted. Its position was that the CMS was a feature of the network, and I have agreed with that. So this part of Apple’s objection falls away.
432. The other thing Apple said was that the requirement was unclear “to the extent that this requirement means anything more than that the [mobile] is adapted to transmit and spread an ACK/NACK signal or CQI signal in accordance with a set of instructions”. That is what I have held a CMS is, in essence, so this falls away too.
433. In support of these points, Apple said that Optis was taking different constructions for infringement and validity. I do not believe that Optis is doing so. It accepts that its broad construction for infringement has to be applied for validity, but it says it wins on the facts.
434. Apple also said that Optis’ construction of CMS would lead to [0069] of the Patents being “wrong” (a like point was made about [0063]). [0069] says:

435. This paragraph says that the only difference between embodiment 1 (within the claims as proposed to be amended) and embodiment 3 (outside those claims because of the cyclic shift) lies in the processing in, and hence commands issued by, the network. The paragraph does not say, but I think it is self-evident, that the mobile will have to be able to process different commands from the network if those commands vary over time. This means working with different CMSs at different times, a point which I have addressed in relation to the interpretation of CMS above. There was some cross-examination of Mr Bradford about this which in itself was somewhat muddled, but in the end I think he confirmed that the “base station and the mobile must have a common understanding of where the resource is".
436. Apple said that this paragraph was wrong or so unclear that Optis ought not to be allowed to amend the claims unless it also addressed the error in this paragraph. For reasons just given, I do not think it is erroneous. To the extent that it is unclear it is only in a minor degree and anyway does not affect the clarity of the proposed amendments.
Added matter
437. This is a short point.
Legal test
438. There was no dispute about the basic relevant legal test, which has been set out in numerous judgments of the Patents Court and Court of Appeal going back to Bonzel v. Intervention (No 3) [1991] RPC 553 at 574: what is required is a strict comparison of the disclosures of the application and of the specification, and matter is added unless clearly and unambiguously disclosed in the application as filed.
439. In the present case, the argument can be tested by reference to the application for ‘549 (“the Application”).
No disclosure of 3 out of 4 orthogonal sequences
440. Apple says that there is added matter by a disclosure in the Patents (essentially by and in their claims) of using 3 out of 4 possible orthogonal (i.e. Walsh-type) codes for the ACK/NACKs.
441. Although Apple advances this argument under a single heading there are actually two points, since claim 1 of 549 and claim 1 of 810 simply require the use of 3 codes, and it is only claim 7 of 549 which specifies that they are of length 4, which is equivalent to saying that three out of 4 possibilities are to be used.
442. I will deal first with the point on claim 1 of each of the Patents.
443. Apple relies on it having been common ground that the ACK/NACK signals referred to in the claims are data signals, and that it was CGK that ACK/NACK data signals in LTE were going to be spread using Walsh codes of length 4. Apple is correct about both these propositions, and indeed I do not think they were in dispute.
444. Apple then says that with both these things in mind, claim 1 of each of the Patents discloses the use of 3 out of 4 codes for ACK/NACK data signals.
445. Apple also positions the argument as a squeeze, given that Optis says that a decision to use just three out of four codes, rather than all four, is part of the inventive distinction over the prior art.
446. Optis responds that claim 1 of each of the Patents does not disclose using 3 out of 4 codes, but merely covers that possibility. It accepts that given the Patents’ specification one extremely obvious thing to do in LTE would be to use three codes of length 4, but that that is not the same as there being any new disclosure. It says that the focus on length 4 codes comes from Apple’s obviousness case, and not the disclosure of the Patents.
447. In my view Optis is correct in all these points and Apple’s attack on the respective claim 1s is a bad one. There is no teaching of 3 codes of length 4 in those claims.
448. In particular, it is not legitimate to say that a claim discloses things that have its explicit requirements when combined with some CGK feature. Apple relied on what Floyd LJ said in Unwired Planet at [72]. That was in the context of priority, but I accept that what Floyd LJ was saying was equally applicable to added matter. He was emphasising that the disclosure of a priority document (the same would be applicable to an application) has to be assessed in the light of the CGK, and that that is especially important when assessing implicit disclosure. He was not addressing whether a priority document (or application) discloses adding to a set of explicitly claimed features a further, unmentioned feature on the basis that that feature is CGK.
449. I would also say that Apple’s reliance on small quotes from Mr Bradford’s evidence on this point was misconceived; he did say that he thought it was part of the inventive concept relevant to obviousness that three of four orthogonal sequences be used, but that is because he was addressing prior art that used all four of length 4.
450. As to the point about claim 7, the position is different since there clearly is a teaching of using three out of four codes. Since Apple’s case against claim 1 of each Patent over the prior art fails for reasons given above, Optis does not need claim 7, but I will resolve it in any event.
451. The first two embodiments of the Patents (and of the Application) are of the use of three codes of length 3, but there is teaching that the invention is not limited as to length (Application at [0020], Patent at [0021]). After all the embodiments there is the following teaching at [0075] of the Application ([0076] of the Patent):

452. This is a clear disclosure of using length 4 codes in embodiments 1 and 2, which have three codes, as I have just explained. Apple says that this teaching is connected with embodiment 3, which uses four codes of length 4. While the teaching follows embodiment 3 and while its thrust, of combining embodiments, would be understood to apply to embodiment 3 in a general sense, the last sentence is not about embodiment 3.
453. There was some oral evidence on this, in the course of which Mr Bradford accepted that the specification did not “spell out that specific example of three out of four”, but the issue of disclosure in terms of what the specification means is not really one for experts once the CGK is understood, and anyway he was not asked about [0075]/[0076]. I think he just meant there was no complete worked example using three codes of length 4, and that is true.
454. Therefore I find that there is a disclosure of the use of 3 codes of length 4 in the Application, to the clear and unambiguous standard required. This means the attack on claim 7 fails and is an additional reason why the attack on claim 1 fails, even if I am wrong in my analysis above.
455. So the added matter attacks against claim 1 and against claim 7 both fail.
Conclusions
456. My conclusions are:
i) The Patents are essential and infringed by Apple.
ii) The attacks over the prior art fail.
iii) The amendments sought are allowable.
iv) The Patents in their proposed amended forms are valid.
457. I will hear Counsel as to the form of Order if it cannot be agreed. I direct that time for seeking permission to appeal shall not run until after the hearing on the form of Order (or the making of such Order if it is agreed).
