Freely Available British and Irish Public Legal Information
[Home] [Databases] [World Law] [Multidatabase Search] [Help] [Feedback]
England and Wales Court of Appeal (Civil Division) Decisions
You are here: BAILII >> Databases >> England and Wales Court of Appeal (Civil Division) Decisions >> IPCOM GmbH & Co Kg v Vodafone Group Plc & ors [2021] EWCA Civ 205 (19 February 2021)
URL: http://www.bailii.org/ew/cases/EWCA/Civ/2021/205.html
Cite as: [2021] RPC 10, [2021] Bus LR 813, [2021] EWCA Civ 205, [2021] WLR(D) 105
[New search] [Printable PDF version] [Buy ICLR report: [2021] Bus LR 813] [View ICLR summary: [2021] WLR(D) 105] [Help]
ON APPEAL FROM THE HIGH COURT OF JUSTICE,
BUSINESS AND PROPERTY COURTS, INTELLECTUAL PROPERTY LIST (ChD), PATENTS COURT
Mr Recorder Douglas Campbell QC
Strand, London, WC2A 2LL |
||
B e f o r e :
LADY JUSTICE ASPLIN
and
LORD JUSTICE ARNOLD
____________________
| IPCOM GMBH & CO KG |
Claimant |
|
| - and - |
||
| (1) VODAFONE GROUP PLC (2) VODAFONE LIMITED (3) VODAFONE UK LIMITED |
Defendants |
|
| - and - |
||
| SECRETARY OF STATE FOR DEFENCE |
Intervener |
____________________
Thomas Mitcheson QC and Stuart Baran (instructed by Hogan Lovells International LLP) for the Defendants
Michael Silverleaf QC and Azeem Suterwalla (instructed by Government Legal Department) for the Intervener
Hearing dates : 26-28 January 2021
____________________
Crown Copyright ©
- The Claimant ("IPCom") is the proprietor of European Patent (UK) No. 2 579 666 entitled "Allocation of access rights for a telecommunications channel to subscriber stations of a telecommunications network" ("the Patent"). The Patent is among a portfolio of mobile phone patents which IPCom acquired from Robert Bosch GmbH. It is a divisional patent of which both the parent and another divisional have previously been litigated in this country. The Patent has a priority date of 8 March 1999, and it expired on 15 February 2020. IPCom contends that the Patent was essential to operating access control in accordance with an optional part of the LTE (4G) standard and that the Defendants ("Vodafone") infringed the Patent prior to a re-design implemented by Vodafone shortly before trial. Vodafone contend that the Patent was invalid and dispute infringement.
- The Patent is subject to pending opposition proceedings before the European Patent Office. As result of the EPO proceedings, IPCom made two applications to amend the claims of the Patent, the first unconditionally and the second conditionally. At trial the first set of amended claims was referred to as the "unconditionally amended claims" and the second set as the "conditionally amended claims".
- Mr Recorder Douglas Campbell QC sitting as a Judge of the High Court held, for the reasons given in his judgment dated 28 January 2020 [2020] EWHC 132 (Pat), that the unconditional amendments were impermissible on the ground of added matter, but that the conditionally amended claims were valid. He held that some of Vodafone's allegedly infringing acts infringed, but that others did not, in some cases having regard to his construction of the claims and in other cases because Vodafone had a defence of Crown use.
- Both parties have appealed against the judge's consequential order dated 8 April 2020 with permission granted in part by the judge and in part by Floyd LJ. IPCom does not challenge the judge's conclusion that the unconditional amendments were impermissible, but does challenge the judge's construction of one of the conditionally amended claims which underpinned his conclusion of non-infringement in some cases and his conclusion that Vodafone had a defence of Crown use in others. Vodafone challenge the judge's construction of the conditionally amended claims which underpinned his findings of infringement, a finding of infringement by equivalents and his conclusion that the conditionally amended claims were valid. In addition, Vodafone contend that any infringement was de minimis. Finally, Vodafone challenge the form of a declaration as to essentiality which the judge made.
- The Secretary of State for Defence ("SSD") has intervened in IPCom's appeal with permission granted by Lewison LJ in order to challenge the judge's conclusion on Crown use, and in particular his interpretation of section 55(1) of the Patents Act 1977. Although the intervention is made by SSD because the Ministry of Defence is most likely to be affected by the judge's decision, counsel for SSD explained that other interested departments had been consulted and supported SSD's position.
- Before proceeding further I would like to pay tribute both to the judge's careful judgment, which dealt concisely with a large number of issues, and to the high quality of the submissions we received on the appeal.
- It is common ground that the Patent is addressed to an engineer (or a team of engineers) concerned with developing mobile phones for use in the UMTS (3G) mobile telecommunications standard, and in particular developing systems for the control of access to the random access channel (RACH). There is no dispute that the skilled person would be, as the judge put it, "very skilled indeed", and in particular would know where to find relevant information in the various standards.
- There was little dispute before the judge as to the skilled person's common general knowledge as at the priority date. I reproduce the judge's account in slightly abbreviated form below.
- Where the uplink from a mobile station (such as a mobile phone) is a shared RACH, there is a danger of collision between users' signals, allowing stronger signals through and preventing weaker ones. This competition is called "contention". It can be tackled in numerous ways. One set of ways in which the problem is tackled is by restricting access to the channel.
- One well known way of restricting access to the channel involves a form of lottery. "Lottery" is not a term of art, but is a convenient term to provide an analogy for what is done. Each mobile station generates for itself a random number and compares it with a value sent by the network. A "win" can be defined as generating a random number greater than or equal to the transmitted value. So, for example, the possible transmitted numbers could be 1 to 10, and the random numbers could be 1 to 9. If the base station transmits a 10, no mobile will get onto the channel, but if it transmits a lower number than 10 an increasing proportion of mobiles can get on. At busy times the access can be throttled back to prevent collision. At very low usage times the transmitted value could be 1, and all mobiles would get access.
- Systems in which certain classes of user (user classes or access classes) could be restricted from access were also well known. For example class barring, under which a mobile of a particular class would be barred from access absolutely, was a feature of the GSM/GPRS (2.5G) system. This is explained below.
- Bandwidth is a scarce resource in any mobile telephone system. Designers of such systems try to arrange matters so as to minimise the amount of data that has to be sent routinely. One common general knowledge way of limiting the amount of data to be sent is the use of single bit flags, which alert the mobile to the fact that data is coming. This allows the network only to send the data when the flag is set.
- Section 3.3.1.1.1 of GSM 04.08 specifies the method for determining whether the mobile in question is granted permission to access the network. It explains that each user is allocated to an access class. The allocated access class is stored on the SIM. There are 10 normal access classes, access classes 0 to 9. These are randomly allocated based on the last digit of the International Mobile Subscriber Identifier number (the "IMSI"), which is essentially a SIM Card identifier. There are approximately equal numbers of users in each of access classes 0 to 9. In addition, some special users are also allocated to additional special access classes 11 to 15. GSM 02.11 (now TS 100 921) defines the special access classes as being for the following high priority users:
- Section 3.3.1.1.1 of GSM 04.08 states that the system can instruct mobiles in particular access classes not to make access attempts by sending a list of "authorised" access classes. This allows the load on the access channel to be varied between 100% and 0% in steps of roughly 10%. When the load on the access channel is controlled, some user classes will be able to access the system, whereas other user classes will be denied any access to the system. The system is referred to as "class barring".
- In GSM, class barring was a relatively crude concept: either everyone in a given class was barred, or nobody. If the class to which the mobile belonged was not barred, then the next step was to request network access.
- Each access class was represented by a single bit (i.e. there were 15 in total, as well as an additional bit for access class 10 which is not relevant for these purposes). Even if the access class to which the mobile belonged was allowed access, it did not follow that the individual mobile itself would be granted access. The mobile would allow a random number of time slots to pass before first requesting access. If the network did not have sufficient resources to grant access to the mobile upon its initial request, the mobile would wait for a random number of time slots to pass before retransmitting its request for access. This was called "random back-off".
- In GSM 04.60, which dealt with GPRS, there was a two-step test before the mobile gained access to the Packet Random Access Channel (PRACH). The first step was to check whether the access class was barred, as above. The second step was a service-based persistence test. In particular, the network transmitted a 4-bit persistence value for each of four differently defined radio priorities. The mobile would then conduct a persistence test by drawing a random value between 0 and 15 and compare this with the relevant transmitted threshold value. If the threshold (i.e. transmitted) value was less than or equal to the (mobile-generated) random number, then the access attempt would be allowed. If not, the attempt failed and the mobile would have to try again after a random time. It was possible to ensure that all attempts were successful by setting the threshold value to 0, or conversely to ensure that all attempts failed by setting the 4-bit value to correspond to 16.
- IS-95 was a proprietary system designed by Qualcomm, which was commercially released in the US and South Korea. IS-95 operated in two modes, one being analogue (which had a single access class barring mechanism) and the other being code division multiple access (CDMA) (which involves all classes undergoing a persistence test in order to gain access). The argument at trial focussed on the latter, on the basis that UMTS was also going to be based on CDMA, and hence the CDMA aspects would be of more interest to the skilled person at the priority date. IS-95 was relied upon by Vodafone as a specific item of prior art, but it was not disputed that the relevant aspects were common general knowledge.
- In summary, there are 10 classes numbered 0 to 9, and six special classes (Access Overload Classes, or ACCOLC) numbered 10 to 15. Mobiles are assigned to one (or more) of the 16 classes. Access to the CDMA system can then be controlled on a per class basis by persistence values transmitted by the base station.
- When the mobile wants to access the Reverse Access Channel (called the R-ACH: the difference between this and the RACH is not material), it has to undergo a persistence test or "lottery". The network transmits parameters relating to this persistence test which vary depending on the type of class involved. For instance, classes 0-9 are treated as a single group and share the same 6-bit value of PSIST. Conversely, each of the special classes 10-15 has an individual 3-bit PSIST value transmitted by the network. The mobile uses the transmitted value of PSIST for the class to which it belongs in order to derive a value, P, which is compared to a random number RP generated by the mobile in order to see whether access is permitted. If not, it waits a random period until it is permitted to make another access attempt, or until it has run out of attempts.
- Again, it was possible to ensure that all attempts for a mobile in a given class were unsuccessful, or conversely that all such attempts were successful, by ensuring that the value of PSIST for the relevant class was set to all 1s or all 0s, as the case may be. For instance, if the transmitted PSIST value for classes 0-9 was 111111, then mobiles in all normal classes were barred.
- Because the PSIST value for the grouped normal classes could take any value from 0-63 (being six bits), and because the PSIST value for each special class could take any value from 0-7 (being three bits), there was a lot of flexibility built into the system. In particular, the likely persistence delay could be varied over a large range for grouped classes 0-9, albeit that it applied equally to all of these classes; and the likely persistence delay could be varied over a smaller range for each of classes 10 to 15 separately.
- The specification of the Patent is in German, but there is an agreed translation. As is often the case with mobile phone patents, the specification is quite short, but densely written. Comprehension is not assisted by the slightly unusual way in which the specification is structured, the inclusion of passages which are irrelevant to the claimed invention (no doubt as a result of the specification's origin as a divisional application), the way in which Figure 4 is divided up and a linguistic oddity which appears to be an artefact of translation. Furthermore, a little care is required because the specification has not yet been amended to conform to the conditionally amended claims.
- After acknowledging some prior art, including aspects of GSM 04.60 version 6.2.0 and 02.11 version 6.0.0, at [0002]-[0006], the specification sets out the advantages of the invention as follows:
- After introducing the figures at [0014], the specification describes a number of exemplary embodiments in [0015] and following. Some of these embodiments do not have all the features of the conditionally amended claims, however.
- After a general introduction to the way in which mobile stations (i.e. mobile phones, also referred to in the Patent as "subscriber stations") access the RACH and to the contention problem and the consequential risk of overloading of the RACH by reference to Figure 1 at [0015] to [0019], the specification states at [0020]:
- The specification goes on in [0021] to describe how information signals in the form of bit patterns transmitted from the base station on a broadcast control channel BCCH are used to inform the individual mobile stations "which rights have been assigned to the corresponding mobile station 5, 10, 15, 20 for sending on the RACH". It states in [0022] that "in order to notify [the mobile stations] of their assigned RACH access rights, the bit pattern comprises the assigned access rights for each user class 35, 40".
- The specification then describes the operation of the lottery by an evaluation unit 60 which accesses an access authorisation card (e.g. a SIM card) by reference to Figure 2 at [0023]. In this context it states that only when the random number R is at least as great as the access threshold value S is "access to the RACH permitted".
- A 10-bit embodiment and an embodiment involving priority classes are described by reference to Figures 3a and 3b at [0024]-[0033]. It is not necessary to describe these in any detail since they fall outside the claims, but it should be noted that the specification refers at [0024] to the access authorisation data "comprising the information relating to the rights for using the RACH".
- A 13-bit embodiment is described by reference to Figure 3c at [0034]-[0036]. Although this also falls outside the claims, it is of some importance since it provides the starting point for the claimed embodiment. The judge summarised the description as follows. In this embodiment, the network is transmitting a bit pattern of 13 bits. These 13 bits include both an access threshold value S (for use in the lottery, if required) and user class information Z (which tells the mobile whether it can access the RACH irrespective of the access threshold value S). Each of these values consists of a number of bits: S3, S2, S1, S0 and Z3, Z2, Z1, Z0. The mobile can obtain access to the RACH in either of two ways:
- In this embodiment, each user class must have an access class bit, since otherwise the mobile would not be able to switch between the two routes of access.
- The specification goes on at [0037] to describe an embodiment which forms the basis of the claims. This is described by reference to a flowchart which, unhelpfully, is split across Figures 4a, 4b and 4c. Vodafone's expert witness Mr Bishop helpfully combined these into one diagram in which he labelled each stage. I reproduce this below.
- The judge explained the disclosure as follows. The first decision diamond 200 asks whether the 10- or 13-bit process should be followed. If there are 13 bits, the system proceeds to diamond 280. At this point, the system carries out two checks: first, is a user class stored on the mobile's access authorisation card (i.e. on its SIM card); secondly, if so, is that user class "normally privileged" or "privileged"? This is described in the specification as follows:
- It should be noted that, in his diagram, Mr Bishop has amalgamated these two checks into a single question of "privileged user class on card?".
- The logic then proceeds as follows:
- The difference between "normally privileged" and "privileged" users is therefore that the "privileged" users can, if their access class is permitted, bypass the lottery. Even if the relevant access class of a "privileged" user is barred, that user can still access the RACH, but only by participating in the lottery. "Normally privileged" users, and those who do not belong to any stored user class, always have to participate in the lottery in order to obtain access to the RACH. This means that the "normally privileged" classes do not actually enjoy any privileges, unless one counts the mere ability to access the RACH via the lottery to be a privilege. (The terms "normally privileged" and "privileged" appear to be an artefact of the translation.)
- The specification states that, if the process does not successfully exit box 250, "the evaluation unit 60 ascertains no access authorization to the RACH 30 for the associated mobile station 5".
- The left side of the diagram (i.e. for 10-bit embodiments) does not refer to "privileged" users and is much the same as Figures 3a, b.
- Mr Bishop summarised the flow diagram above more concisely in a second diagram, which I reproduce below.
- It was common ground between the expert witnesses that in Figure 4 only privileged classes need to have an access class bit. This is because these are the only classes capable of bypassing the lottery. IPCom's expert Dr Irvine also accepted that, if one wanted the flexibility of making any normally privileged class into a privileged class, then that normally privileged class also needed to have an access class bit.
- The specification states at [0038]:
- In [0039] the specification describes the use of a repetition counter which can be communicated to the mobile stations at regular time intervals "together with the bit pattern for the assigned access rights". In [0041] it states that provision can be made for R below the value S "to be a prerequisite for access authorization".
- Conditionally amended claim 1 is a method claim which I have broken down into integers as follows (I have retained the reference numerals since they assist in relating the features of the claim to each other; the amendments are shown by strike-through and underlining):
- Claim 5 (amended from claim 11 as granted) is a dependent claim which reads as follows:
- Claim 6 (amended from claim 12 as granted) is a product claim directed to the subscriber station which tracks claim 1 closely.
- Claim 7 (amended from claim 13 as granted) is a product claim directed to the telecommunications system which reads as follows:
- It is often useful in patent cases, particularly where the claims are prolix, to have a distillation of the inventive concept, although it must be used with care. As the judge recorded at [65], it was common ground before him that the inventive concept of unconditionally amended claim 1 of the Patent had been accurately epitomised by Dr Irvine as follows:
- In his oral submissions in this Court counsel for Vodafone pointed out that the judge had not set out in his judgment any comparable statement of the inventive concept of conditionally amended claim 1. Since no such statement was contained in either of Vodafone's skeleton arguments either, we asked counsel to produce one. Following the conclusion of the hearing, counsel for Vodafone submitted in writing that the inventive concept of conditionally amended claim 1 was the same as that of unconditionally amended claim 1, but with the addition of the feature of the flexibility of making any normally privileged class into a privileged class, so that that normally privileged class also needed to have an access class bit (reflecting the second point noted in paragraph 40 above).
- In response counsel for IPCom submitted that the inventive concept of conditionally amended claim 1 was the same as that of the unconditionally amended claim. Counsel for IPCom disputed Vodafone's contention for three reasons, which it is convenient to take in reverse order. First, Vodafone had pointed to no expert evidence (either written or oral) in support of their contention that this was the inventive concept of conditionally amended claim 1. Vodafone's new inventive concept was never put to Dr Irvine and did not appear in the written evidence of Mr Bishop. On the contrary, Dr Irvine said in his third report that he considered the key inventive concept of conditionally amended claim 1 was the same as that of unconditionally amended claim 1 which the judge quoted.
- Secondly, while conditionally amended claim 1 contained additional wording to overcome the added matter objection to the unconditional amendment, all the additional language did was to incorporate additional aspects of the Figure 4 embodiment without changing the inventive concept. IPCom contends that Figure 4 does not teach flexibility of making any normally privileged class into a privileged class: rather it teaches that membership of the privileged user class is determined by checking what is stored on the SIM card at diamond 280.
- Thirdly, Vodafone were seeking to import their construction of claim 1, and in particular the requirement that "each of the user classes is assigned one access class bit", into the inventive concept.
- Without pre-empting the issue of construction, I consider that IPCom's first and second reasons are good ones for concluding that the inventive concept of conditionally amended claim 1 is the essentially same as that of the unconditionally amended claim.
- Vodafone dispute the judge's construction of claim 1 in three respects: (i) the meaning of the phrase "each access class bit corresponding to a user class", (ii) the meaning of the phrase "a normally privileged user class or a privileged user class" and (iii) the meaning of the expression "access right". IPCom disputes the judge's construction of the phrase "set up to send" in claim 7.
- There is no dispute as to the applicable principles. In short, the words of the claim must be interpreted from the perspective of the skilled person in the light of their common general knowledge and having regard to the inventor's purpose.
- Integer [5] of claim 1 requires that "each access class bit represents one user class and … each of the user classes is assigned one access class bit". Vodafone contend that this means that every user class must have an access class bit transmitted. IPCom contends that it only requires the privileged classes to have an access class bit transmitted. The judge concluded at [81]-[85] that IPCom was correct. Vodafone argue that, even if the judge was correct on the construction of the unconditionally amended claim, he fell into error when it came to the conditionally amended claim, in particular because the latter refers to both privileged and normally privileged users whereas the former only referred to privileged users.
- As the judge noted, Vodafone's argument is partly linguistic and partly technical. The linguistic argument is simple. The claim not only requires that "each access class bit represents one user class", but also requires that "each of the user classes is assigned one access class bit". This requires each and every user class to be assigned an access class bit, and it does not differentiate between the privileged and normally privileged user classes referred to later in the claim.
- The technical argument is that, as noted above, if one wants to be able to convert any normally privileged user class into a privileged user class, then each of the normally privileged user classes must have its own access class bit. Vodafone argue that [0020] of the specification (quoted in paragraph 26 above) refers to changing a normally privileged user class (e.g. everyone whose mobile phone number ends with 1) into a privileged user class which is able to bypass the lottery, thereby achieving dynamic control of access. In addition, Vodafone rely upon what is now claim 5 which is directed to this feature.
- IPCom's response to the linguistic argument is that, in this integer of the claim, the term "user class" is being used as a generic term, and not as a collective term for both privileged and normally privileged user classes. In context, the user classes being referred to are the user classes that make use of an access class bit (i.e. the privileged user classes), not the user classes that do not (i.e. the normally privileged ones). It should be borne in mind that the claim allows for a plurality of user classes each of which is privileged (e.g. fire, police, ambulance).
- IPCom's response to the technical argument is that the claimed method only uses access class information, and hence the access class bits, in respect of the privileged user classes. It would be wasteful to send bits for user classes that are not privileged, and if all classes had access class bits then the distinction between privileged and normally privileged user classes would fall away. IPCom contends that neither [0020] nor claim 5 assist Vodafone.
- The judge agreed with IPCom, and so do I. I acknowledge the superficial attraction of the linguistic argument, but it should be noted that this integer not only forms part of the pre-characterising portion of the claim (a factor which cannot be accorded much weight given that it has been introduced by amendment), but is also prior to the introduction of the privileged and normally privileged user classes. The focus of the integer is upon the presence of access class bits each of which represents one user class when they come to be used in the method.
- In any event, it is the technical considerations which carry most weight. It was common ground between the experts that (i) only privileged users require access class bits in the claimed method and (ii) it would be wasteful of transmission overhead to transmit access class bits for user classes that will not use such bits. Furthermore, I consider that IPCom is correct that the effect of Vodafone's construction is to collapse the distinction in the claimed method between privileged and normally privileged users. Even if Vodafone is correct that the skilled reader would understand that it would be advantageous to be able dynamically to transform all normally privileged user classes into privileged user classes, it does not follow that the claim is so limited.
- [0020] of the specification does not say that all user classes must be capable of being privileged, either temporarily or permanently. All it says is that particular user classes of mobile stations (i.e. a subset) may be permitted access on either a temporarily or a permanently privileged basis. Claim 5 is directed to this feature. It is common ground that claim 5, as a dependent claim, must fall within the scope of claim 1, and on IPCom's construction it does.
- Integer [6] of claim 1 requires a check to be carried out as to "whether the user class is a normally privileged user class or a privileged user class". Vodafone contend that these are mutually exclusive classes. The judge accepted this, but added at [80] that he saw no reason why, in the real world, a given user could not belong to both classes if their SIM card was set up in that way. Vodafone say that this is inconsistent and wrong. As counsel for IPCom explained, however, there is no dispute as to construction: it is common ground that the classes are mutually exclusive. The judge's comment was looking forward to an issue on infringement which is better addressed in context. It is nevertheless convenient to note at this juncture that, as counsel for IPCom pointed out, there is nothing in the specification or the claim about the way in which user classes are stored on the user's SIM card.
- Integer [9] of claim 1 requires that the evaluation unit in step (iv) "allocates an access right for the telecommunication channel to the subscriber station on the basis of the comparison result". Vodafone contend that the "access right" means a positive right of access. IPCom contends that "allocates an access right" covers permitting or denying access. The judge concluded at [74]-[76] that IPCom was correct.
- It is convenient to get two points out of the way before turning to the principal arguments. First, the judge gave four reasons for preferring IPCom's construction, the last of which concerned a dependent unconditional claim. IPCom accepts that this reason does not apply to conditionally amended claim 1. Secondly, counsel for Vodafone submitted that Vodafone's construction was supported by reasoning of Floyd J concerning another divisional of the same parent in Nokia Oyj v IPCcom GmbH & Co KG [2011] EWHC 1470 (Pat) at [46]-[52]. The judge did not accept this, and neither do I. Floyd J was considering a differently worded claim directed to a different inventive concept. Moreover, the arguments appear to have been somewhat different.
- In this instance, Vodafone's argument is primarily linguistic. The argument is straightforward: the claim says that the evaluation unit "allocates an access right" on the basis of the comparison result, it does not say that it permits or denies access to the RACH. Furthermore, similar language appears in the specification: "the right of access to a telecommunications channel is granted" in [0007] (quoted in paragraph 24 above); "rights have been assigned … for sending on the RACH" in [0021] (paragraph 27 above); "assigned access rights" in [0022] (paragraph 27 above); "rights for using the RACH 30" in [0024] (paragraph 29 above); and "assigned access rights" in [0039] (paragraph 42 above). Vodafone accept that the claimed method is one which permits or denies access to the RACH depending on the lottery result, but say that the language of the claim, supported by these passages in the specification, is clear that the way in which this is achieved is by allocating an access right.
- Although their argument is primarily linguistic, Vodafone contend that their interpretation of this feature of the claim is consistent with the inventive concept. Vodafone also contend that it is supported by much of the expert evidence; but as counsel for Vodafone accepted, (a) the expert evidence was not all one way and (b) the words "access right" are ordinary English words, from which it follows that expert evidence as to their meaning is inadmissible.
- Although Vodafone's linguistic argument has considerable force, as IPCom points out, the language of the claim and the specification is not all one way. Thus the claim is to a method "for ascertaining an authorisation for access" i.e. determining whether access is authorised or not (integer [1]); and the method involves checking whether privileged users are "authorized for access to" the RACH (integer [7]). Furthermore, the specification says "access to a telecommunications channel being granted" at [0009] (paragraph 24 above); "access to the RACH 30 permitted" in [0023] (paragraph 28 above); "authorized for access to the RACH 30" in [0037] (paragraph 35(i) above); "ascertains no access authorization to the RACH 30" in [0037] (paragraph 37 above); explicitly, "permit or block access to the RACH" in [0038] (paragraph 41 above); and "a prerequisite for access authorization" (paragraph 42 above).
- Furthermore, the language of "access right" does not compel the conclusion that the claim requires a positive right of access. First, a right can be negative: a patent is a right, but it is negative right to exclude others rather than a positive right to do anything. Secondly, a right of access is not meaningful unless access can be denied. Although counsel for Vodafone relied on an analogy involving a human being being granted the right to access a physical space such as a lawn or a building, I do not find this persuasive because the claim is not talking about either human beings or physical spaces, but about a logic flow to determine utilisation of a resource (as depicted in the flowchart set out under paragraph 32 above).
- In my judgment, the key consideration is that the claim should be construed purposively. Step (iv) in the claim follows step (iii). As the skilled reader will appreciate, the result of the comparison in step (iii) is binary: the mobile either wins the lottery or it loses. The phrase "allocates an access right" must be understood in that context, and must refer to granting or refusing access to the RACH. Furthermore, as counsel for IPCom submitted, it is clear from Figure 4 and [0037]-[0038] that the method embraces both outcomes. This is highlighted by the statement in [0038] that the method permits the network operator to "permit or block access to the RACH" depending on the level of traffic. The effect of Vodafone's construction is that the method is only performed when access is granted. I therefore conclude that the judge was correct on this issue.
- Claim 7 requires that at least one base station is "set up to send information signals with access threshold value and access class information as access authorization data". The judge recorded at [89] that Vodafone contended that "set up to send" meant that either there was appropriate programming in the base station to send the relevant signals or that the base station was adapted or configured for such purpose, and that IPCom accepted this.
- Despite this common ground, two issues of construction emerged on the appeal. First, IPCom contends that the judge overlooked a dispute as to what constitutes the "base station" in the claim. IPCom contends that what constitutes the base station must be considered from a functional perspective, and thus can include an associated user interface operated from a central control room. I did not understand counsel for Vodafone to dispute the premise of this contention. Although he disputed the conclusion, in principle it seems to me to be correct. Whether this matters is a separate question which I will return to in the context of infringement.
- Secondly, counsel for Vodafone submitted during the course of his oral submissions that "set up to send" meant "sending". Not only is this submission inconsistent with the common ground recorded by the judge, which is not challenged either by any of Vodafone's grounds of appeal or by any Respondents' notice from Vodafone, but also it is manifestly wrong. Again, whether this matters is a separate question.
- Section 76(3)(b) of the Patents Act 1977 provides that no amendment of a patent shall be allowed after grant if it "extends the protection conferred by the patent". Vodafone contend that the conditional amendments to claim 1 which the judge permitted extend the protection conferred by that claim, and therefore should be disallowed. There is no dispute that, if the amendments to claim 1 are impermissible for this reason, then the same objection feeds through into the other claims. The consequence would be to leave IPCom without any claims it could assert (since the granted claims have been abandoned and the unconditional amendments were unallowable).
- For convenience, I will set out granted claim 1:
- It is common ground that it is sufficient for Vodafone to show that one example which was not covered by the granted claim is covered by the amended claim. Vodafone submitted to the judge that the example could be a hypothetical one. The judge accepted this, but said that the example must at least be a possible one. I did not understand counsel for Vodafone to take issue with this as a statement of principle, but in any event I consider that the judge was plainly correct.
- Vodafone postulate a hypothetical example in which a user is a member of a class 16 which always has access to the RACH (e.g. Cabinet ministers). Vodafone argue that such a user would not be privileged since there would be no need to check the access class bit for that class. Nor would such a user be normally privileged since there would be no need to do the lottery. Vodafone further argue that such a method would be excluded by the granted claim because the granted claim is exhaustive with respect to classes of users: it contemplates that all users are either privileged or not privileged. By contrast, Vodafone argue, the method would fall within the conditionally amended claim because it only requires the lottery to be performed for certain categories of non-privileged user and not all classes.
- The judge dealt with this argument at [122] as follows:
- Counsel for Vodafone submitted that the judge was simply wrong to say that the example was not a possible one. As counsel for IPCom pointed out, this submission amounts to a challenge to a finding of fact. As counsel for IPCom also pointed out, however, Vodafone adduced no evidence to show that the example was a possible one.
- Counsel for Vodafone sought to meet this point by emphasising that the example was a hypothetical one in which class 16 users are defined as ones who always have access to the RACH. In my view this is not an answer to the judge's objection, since it amounts to an assertion of a technical result without explaining how that technical result may feasibly be achieved. The claimed method is a complete method for controlling access to a specific telecommunications channel. According to that method (whether according to the granted or conditionally amended claim), there are only two types of non-privileged user: those that have an assigned user class that is normally privileged and those that have no assigned user class at all. Users who have a user class that is not privileged are normally privileged and must do the lottery. If one postulates, as Vodafone do, that there is some unspecified way of accessing the RACH without either doing the lottery or being permitted to bypass the lottery because the user is privileged, then that can only be because the entirety of the claimed method (or, to put it another way, the entirety of the logic flow set out in Figure 4) is being circumvented. Even if this is feasible, it will not infringe either the granted claim or the conditionally amended claim.
- IPCom contends that the Patent was essential to the LTE standard, specifically 3GPP TS 36.331. I reproduce the judge's explanation of the relevant parts of the standard in abbreviated form below.
- Section 6.3.1 defines SystemInformationBlockType2 ("SIB2"). It has various parameters including ac-BarringForSpecialAC (a five bit string) and ac-BarringFactor (which can have a range of values from p00 to p95).
- More particularly it states as follows:
- ac-BarringForSpecialAC allows the string to identify which special user classes from 11 to 15 are allowed to bypass the lottery. In ac-BarringFactor the number following p is the lottery threshold. If the value is p05, then all random numbers below 0.05 (which means 5% of all lottery attempts) will win the lottery. If the value is p00, then it is not possible to win the lottery since participants cannot generate a number which is lower than zero. The last sentence provides that, unless all of the special user classes are allowed to bypass the lottery, the threshold will be set at a level which means all lottery participants lose. The thinking appears to be that, if any of the special user classes are barred, then nobody else should be allowed access either.
- Section 5.3.3.11 sets out the "Access barring check" in the form of pseudocode, some of which is immaterial for present purposes. The logic in the relevant parts proceeds as follows:
- The fields ac-BarringForSpecialAC and ac-BarringFactor both need to be transmitted for this method to work. Otherwise, the system does not know whether users in the special classes have an active bypass for the lottery, nor what the winning score in the lottery is. The judge used the terms "considered not barred" and "considered barred" both because that is what the standard says, and because Vodafone point out that the mobile does not actually gain access to the relevant telecommunications channel as a result of the process.
- It is common ground that another part of the standard, 3GPP TS 22.011 version 12.3.0 release 12, makes it clear that it is optional whether or not to operate access control in LTE. The network operator can choose either to address the problem of overloading in a different way or simply to put up with it (or rather, force its users to put up with it). The judge held that this did not prevent the Patent being essential to the standard if and insofar as the network operator chooses to implement section 5.3.3.11 of TS 36.331. Vodafone do not challenge that conclusion (but do challenge the form of the declaration made by the judge, a point I shall address below).
- It is also common ground that TS 36.331 makes it clear that UEs are all members of one of access classes 0-9 and may also be members of one or more of access classes 11-15 (the special user classes).
- There are a number of issues on infringement, some of which depend at least in part on the construction of the claims and some of which are independent. In this section of the judgment I will address the issues which depend at least in part on construction. I will address the issues of Crown use and de minimis use separately.
- Before proceeding further, I should explain that Vodafone served a Product and Process Description which described seven different modes of operation of the Vodafone network (or, in some cases, parts of it) identified by the letters A-G. Annex A, which described the normal mode of operation, was not alleged by IPCom to infringe. The infringement issues which are live on the appeals concern Annex C (responses to emergency requests in accordance with MTPAS, as to which see below), Annex E ("Limited Historical Operation") and Annex F ("Anomalous Testing Operation"). I shall describe what these involve below.
- Vodafone rely upon the fact that in LTE none of access classes 0-9 (i.e. the normally privileged user classes viewed from the perspective of the claim) has an access class bit transmitted, only access classes 11-15 (i.e. the privileged user classes) do. This non-infringement argument depends on Vodafone's construction of integer [5] of claim 1, which I have not accepted.
- As discussed above, it is common ground that these classes are mutually exclusive. Vodafone contend that it follows that operating in accordance with LTE does not infringe because, as noted above, it is common ground that the standard requires any user allocated to access classes 11-15 also to be allocated to an access class 0-9.
- IPCom's answer to this is that users allocated to access classes 11-15 in LTE are privileged within the meaning of the claim because they have the opportunity to bypass the lottery (depending on the value of the access class bits sent by the base station). Users who are not allocated to access classes 11-15 have to do the lottery and therefore are normally privileged within the meaning of claim. Thus the privileged and normally privileged classes of user are mutually exclusive as required by the claim even though the privileged users are allocated to both one of access classes 11-15 and one of access classes 0-9. IPCom say that this is the point the judge was attempting to express at [80].
- It does not matter whether IPCom's reading of the judgment is correct. Either way, I accept IPCom's argument on this point. It is the privileged and normally privileged classes which the claim requires to be mutually exclusive. Vodafone's argument wrongly equates these with access classes 11-15 and access classes 0-9 respectively.
- Vodafone rely upon the fact that, if ac-BarringFactor is always set at p00, there would be no possibility of a lottery winner being allocated an "access right" because everyone would fail the lottery. Vodafone argue that this falls outside the claim because the claim requires that it be possible for what Vodafone call "privileged non-bypass users" to access the RACH sometimes.
- The judge rejected this argument at [157]-[159] for three reasons. The first was that, on IPCom's construction of the claim, which he accepted, the claim did not require a positive right of access to be allocated. The second was that setting ac-BarringFactor to p00 did not make any difference to whether the lottery was performed or the invention, it merely made a difference to the possible outcomes. The third was that infringement could not depend how long ac-BarringFactor was set at p00.
- I agree with the judge's reasons except that I would express the third one slightly differently. The standard allows ac-BarringFactor to take a range of values from p00 to p95, which allows the operator to turn the dial (to adopt Vodafone's metaphor) over time. It does not require it to be set permanently to p00. I think the judge made this point later in his judgment at [180].
- Vodafone contend that conditionally amended claim 1 is not infringed because, as is common ground, there is only one check in LTE (is the mobile associated with a privileged user class?) whereas integer [6] of the claim requires two checks (is there a user class and is the user class privileged or normally privileged?). The judge held at [162]-[171] that for this reason the claim was not infringed on a normal interpretation, but was infringed by virtue of the doctrine of equivalents.
- In order to determine whether there is infringement by virtue of the doctrine of equivalents, the court must normally ask and answer the three questions set out in the judgment of Lord Neuberger in Actavis UK Ltd v Eli Lilly and Co [2017] UKSC 48, [2017] Bus LR 1731 at [66]:
- The judge recorded at [167] that it was undisputed before him that the answers to the first two questions were both "yes" since the number of checks was not material to the inventive concept and Figure 4 itself rolled up the two checks into a single diamond. Moreover, in the real world, every user will have a user class. The judge went on to conclude that there was no reason why the skilled reader would have concluded that strict compliance with the two-step language was an essential requirement of the invention.
- Vodafone repeat the argument which they advanced before the judge that the skilled reader would understand that strict compliance was an essential requirement because the skilled reader is to be deemed to know that claim 1 has been amended in order to ensure the validity of the claim. More specifically, the judge held at [108]-[110] that, whereas the application for the Patent as filed only disclosed two checks, unconditionally amended claim 1 not merely claimed, but positively disclosed, a single check. Thus it disclosed subject matter which was not disclosed in the application, and amounted to an impermissible intermediate generalisation.
- Like the judge, I do not accept this argument, although I would express my reasoning slightly differently. I am content to assume that Vodafone is correct that the skilled reader is deemed to know that claim 1 has been amended for the reason explained above. On that basis, the skilled reader would appreciate that the problem with the unconditionally amended claim was what it disclosed compared to the application, a problem that was cured by the conditionally amended claim. As Lord Neuberger explained in Actavis at [74], however, one should not confuse the disclosure of a patent with the scope of protection of the relevant claims. In my judgment the skilled reader would not conclude from the mere fact that the disclosure of the Patent had been pegged back to what was disclosed in the application that this limited the scope of protection of the conditionally amended claims to two checks. The argument advanced by counsel for Vodafone in this case is an argument of the same genus as, and a weaker one on the facts than, the one that he successfully overcame in the Supreme Court in Actavis.
- Vodafone also argue that, independently of the history, the skilled reader would appreciate that conditionally amended claim 1 was essentially a claim to Figure 4 of the Patent, and for that reason would conclude that strict compliance with the requirement for two checks was intended. In my view this is a worse argument than the previous one, because, as noted above, Figure 4 itself rolls the two checks into one.
- IPCom contends that Vodafone's base stations, which do not send barring parameters in normal use (i.e. operating in accordance with Annex A) but do transmit them when responding to an emergency request (i.e. operating in accordance with Annex C), are "set up to send" such barring parameters. Vodafone dispute this. The judge agreed with Vodafone.
- It is important to appreciate that the issue here is one of infringement of claim 7, which is a product claim, pursuant to section 60(1) of the 1977 Act. There is no claim for infringement pursuant to section 60(2) ("means essential"), and counsel for IPCom accepted that no such claim would lie against Vodafone. This issue does not arise in relation to the method claims.
- As explained above, IPCom accepts that "set up to send" means either that there is appropriate programming in the base station to send the relevant signals or that the base station is adapted or configured for that purpose. The issue is whether the base stations satisfy this criterion. IPCom's argument focusses attention on what happens when the base stations are instructed to respond to an emergency request.
- This was described in the evidence of Vodafone's witness Mr White which was not challenged by IPCom at trial. Counsel for Vodafone summarised this evidence in an annex to Vodafone's skeleton argument in reply on IPCom's appeal in a manner which counsel for IPCom accepted as accurate. It consists of seven steps as follows:
- Vodafone added that, prior to 28 March 2017, Vodafone did not have LIMA and had to either (a) use alternative tools to create scripts which had to be manually loaded onto the relevant supplier's OSS or (b) manually configure the relevant base stations.
- For reasons that will appear, I should set out the way in which the judge described steps 2 to 5 in paragraph 6 of Confidential Annex 2 to his judgment (Vodafone did not maintain its claim to confidentiality in respect of the relevant material in this Court):
- In the context of considering the construction of the "set up to send" integer of claim 7 the judge referred to a number of earlier first instance decisions concerning computer-implemented inventions, including Koninklijke Philips Electronics NV v Nintendo of Europe GmbH [2014] EWHC 1959 (Pat). In that case Birss J (as he then was) said:
- On the appeal counsel for IPCom did not take issue with this approach to claim construction, but relied upon what Birss J went on to say about infringement at [133]:
- As counsel for IPCom pointed out, this reasoning shows that a computer may be appropriately programmed to satisfy a claim to means suitable for carrying out a function if the relevant software is present in the apparatus even though the software has not yet been loaded into memory because the apparatus has not yet been switched on.
- Turning to the present case, the judge held that the "set up to send" requirement of claim 7 was not satisfied for the following reasons:
- Although counsel for IPCom submitted that the judge had fallen into error because he had overlooked the point as to the meaning of "base station" discussed in paragraph 72 above, it does not appear to me that the judge's reasoning in this passage depended on divorcing the base stations from the user interface in the central control room. Indeed, as counsel for IPCom himself pointed out, elsewhere in his judgment (namely when dealing with the question of essentiality at [89]) he approached the system holistically:
- Rather, the crux of the judge's reasoning was that the base stations were not "set up to send" access information because that required "reprogramming the base station software". IPCom disputes this. Counsel for Vodafone submitted that this is a challenge to a finding of fact, and moreover one which is not open to IPCom because no such challenge was articulated in its grounds of appeal. I do not accept the latter point: I consider that paragraph 5 of IPCom's grounds of appeal ("The Judge ought to have held that the unchallenged evidence of Mr White …, as summarised in Confidential Annex 2 §6 … satisfies the requirement for 'set up to send'") adequately laid the foundation for this challenge, although it should have been more explicit (see Taylor v Rhino Overseas Inc [2020] EWCA Civ 353, [2020] Bus LR 1486 at [61]-[63] and [68]).
- As for the merits of the challenge, both this Court and the Supreme Court have in recent years repeatedly urged the need for appellate caution before interfering with findings of fact by first instance courts and tribunals. In the present case, however, not only is the relevant evidence in writing and unchallenged, but also there is an apparent inconsistency between what the judge said in Annex 2 and what he said in the body of the judgment. Annex 2 refers to "chang[ing] the settings" of the base stations, and does not mention any "reprogramming", whereas the body of the judgment refers to "reprogramming" the base stations, rather than changing their settings.
- In my judgment the language which the judge used in Annex 2 is more accurate, as can be seen from Vodafone's own summary quoted in paragraph 107 above. Even so, I do not accept IPCom's argument that "chang[ing] the settings" of the base stations is equivalent to the scenario considered by Birss J in Philips v Nintendo. In that case, all that had to be done was for the apparatus to be switched on, at which point the software would be loaded into memory and would start running, when it would satisfy the functional requirements of the claim. In the present case, the settings of the base stations had to be changed by the operator in order to make the base stations operate in a different way. This is true whether the settings were changed using LIMA, a different tool or manually. It is true that the base stations were capable of altering their mode of operation so as to send the relevant signals as soon as their settings were changed, but without that change the base stations could not operate in Annex C mode. I do not accept counsel for IPCom's submission that this is analogous to a radio which has a switch to change from mono (non-infringing) to stereo (infringing), because in that scenario there would be infringing circuitry present at all times even if it was not in operation at any particular time. In my judgment the judge was therefore correct to conclude that in normal use the base stations were not appropriately programmed or adapted or configured to send the barring parameters.
- For completeness I would add two footnotes. First, counsel for IPCom submitted that the approach taken in Philips v Nintendo was consistent with the "kit of parts" doctrine discussed in Virgin Atlantic Airways Ltd v Delta Airways Inc [2010] EWHC 3094 (Pat), [2011] RPC 8 (the point did not arise on the appeal in that case). I remain somewhat sceptical about the kit of parts doctrine for the reasons explained at [131] in Virgin v Delta, but it is not necessary or profitable to consider the doctrine further in the present case given that it is not about dealings in a kit of parts.
- Secondly, counsel for IPCom suggested that problems of this kind might be better analysed in terms of the doctrine of equivalents than in the way in which they had been analysed in cases like Philips v Nintendo. Given that he did not suggest that IPCom could succeed by that route if it did not succeed on the arguments discussed above, however, it is not necessary to consider that interesting suggestion on this occasion.
- The judge held that Vodafone had a defence of Crown use in relation to Vodafone's base stations which operated in accordance with Annex C of Vodafone's Product and Process Description when responding to an emergency request as part of a scheme known as the Mobile Telecommunications Privileged Access Scheme ("MTPAS") or during testing for this purpose. The consequence is that compensation is payable by the relevant Government department rather than Vodafone. Both IPCom and SSD contend that the judge fell into error when construing section 55(1) of the 1977 Act. The issue is what is meant by "authorised in writing by a government department", or more specifically what form of authorisation is required for this purpose. There is no challenge to the judge's conclusion that Vodafone's acts were "for the services of the Crown".
- MTPAS is described in a document produced by the Cabinet Office Civil Contingencies Secretariat, of which the current version (4.01) is dated March 2019. This document describes the Cabinet Office as the "owner of MTPAS" and sets out how the scheme works. In short, MTPAS provides a mechanism for the government to privileged access to mobile phone networks to organisations involved in responding to an "emergency" as defined in the Civil Contingencies Act 1994. It is activated by way of a request sent to mobile phone networks by or on behalf of the senior police officer in charge of the emergency response (known as the Police Gold Commander). The format of this request is set out in a memo which was sent by the Cabinet Office to Chief Constables in March 2008: see Annex A thereof. More specifically, the MTPAS protocol is activated by an initial telephone call, which is then followed up with "a completed form sent by either email or facsimile … as the official notification and written audit trail": see section 6 of the MTPAS document at paragraph 80. When Vodafone receive such a request, but not before, they activate access control in line with the request they have received. Vodafone do not charge for this service.
- It is common ground that:
- Patents for inventions were originally granted by the Crown in the exercise of the Royal prerogative subject to the constraints imposed by the Statute of Monopolies 1623. Prior to 1883, the Crown, acting by its servants and agents, was entitled to use patented inventions without the consent of the patentee and without compensation (Feather v R (1865) 6 B & S 157), although by the nineteenth century it was the practice to reward the patentee ex gratia. The House of Lords held in Dixon v London Small Arms Co Ltd (1876) 1 App Cas 632 that the exemption did not extend to contractors who supplied articles in accordance with a patent to the Crown. The contract in that case did not refer to patents, and it would have been possible to fulfil it without infringing the plaintiff's patent.
- Lord Hatherley addressed this point at 649:
- Lord Penzance said at 655:
- Lord O'Hagan said at 658:
- Lord Selborne said at 660:
- Although the House did not speak entirely with one voice, it seems to me that the general tenor of the speeches is that, if the Crown exemption was to apply, it could only do so if use of the patented invention without the consent of the patentee either had been expressly authorised by the Crown or such authorisation was necessarily to be implied. That would not be a surprising conclusion looking at the matter from the perspective of the law of agency.
- The decision in Dixon led to a legislative response in the form of section 27 of the Patents, Designs and Trade Marks Act 1883, which provided:
- This provision contains the essential elements of the modern law, which accommodates private property rights with the public interest. A patent has effect against the Crown, but the Crown may, acting by its employees, agents or contractors, use the invention "for the services of the Crown" provided that compensation is paid. It was re-enacted in very similar terms in section 29 of the Patents and Designs Act 1907, except that the two sub-sections were combined into one section.
- In Pyrene Co Ltd v Webb Lamp Co Ltd (1920) 37 RPC 57 the defendant was requested by the Ministry of Munitions during the First World War to manufacture and supply fire extinguishers which were copies of the plaintiff's patented fire extinguishers. The defendant supplied a quantity of such fire extinguishers under contracts headed "Pyrene type fire extinguishers" which specified "Fire Extinguishers (charged) one quart pump operated type, Pyrene or equivalent". P.O. Lawrence J held that the defendant had a defence to infringement under section 29 of the 1907 Act.
- He stated the law as it was prior to the 1883 Act in the following terms at 64:
- Having recorded counsel for the plaintiff's submission that there was no Crown use defence "unless the contract expressly or by necessary implication provides that [the contractor] is to make use of the patented invention in fulfilling the contract", he held that this criterion was satisfied for reasons he expressed as follows at 65:
- Thus, consistently with my reading of Dixon, Pyrene established that a contractor was acting for the Crown if the contract by necessary implication authorised the use of the patented invention.
- Section 29 of the 1907 Act was substituted by section 8 of the Patents and Designs Act 1919. The substituted section provided, so far as relevant:
- For present purposes the key change to the law which this made was to require the authorisation to be in writing (although it also provided for disputes to be determined by the court). The editors of the 6th edition of Terrell on the Law of Patents (1921), Courtney Terrell and Arthur Jaffé, considered the effect of this at 398:
- In AG for Autogene Aluminium Schweissung v London Aluminium Co Ltd (No 2) (1923) 40 RPC 107 an issue arose during an inquiry as to damages for patent infringement as to the extent to which the defendant's acts attracted a defence under section 29 of the 1907 Act. Although Sargant J mistakenly referred to section 29 as substituted by the 1919 Act, which was not in force at the relevant times, this does not appear to me to affect his reasoning at 117:
- This reasoning seems to me to be consistent with Pyrene, which was cited in argument although not in the judgment. The same view appears to have been taken by the editors of the 7th edition of Terrell (1927), Courtney Terrell and D.H. Corsellis, at 426:
- The Crown use provisions were substantially recast in sections 46-48 of the Patents Act 1949. It is not necessary for present purposes to set these out. The leading authority under the 1949 Act was the decision of the House of Lords in Pfizer v Ministry of Health [1965] AC 512. In that case Pfizer was the proprietor of a patent with product and process claims covering tetracycline, an antibiotic, and processes for making it. Until September 1961 supplies of tetracycline for use in NHS hospitals were obtained from Pfizer's licensees. In May 1961 the Minister of Health announced that he had decided to use the powers conferred by section 46 of the 1949 Act to obtain certain patented drugs from sources other than the patentees or their licensees in order to save money. To this end the Ministry of Health invited tenders for the supply of tetracycline. The form of tender specified that the contract would be subject to a clause which provided that "Under the provisions of section 46 of the Patents Act, 1949 … the contractor is hereby authorised for the purpose of tending for or performing the contract … to make, use and exercise in accordance with the said provisions any invention …". The defendant was successful in its tender and fulfilled the contract by importing tetracycline from Italy where there was no patent protection. The House of Lords held by a majority that the supply of the drug to NHS hospitals was a use "for the services of the Crown", and hence within section 46. No point was taken about the form of the authorisation.
- The Crown use provisions were recast once more in sections 55-59 of the 1977 Act. I shall set out the provisions relevant to this appeal below, but at this stage two points may be noted. First, as will appear, section 55(6) expressly permits authorisation to be given retrospectively. In Dory v Sheffield Health Authority [1991] FSR 221 the plaintiff brought an action against two health authorities for infringing a patent relating to machines known as lithotriptors for treating kidney stones. After the action had been commenced, the Ministry of Defence issued an authorisation to the defendants' supplier RW. This provided that "Under the provisions of sections 55-58 of the Patents Act 1977 … RW is hereby authorised for (a) tendering for the supply of Lithotriptors to Her Majesty's Government; and (b) importing and making Lithotriptors to Her Majesty's Government; and (c) selling or supplying Lithotriptors to Her Majesty's Government, but not otherwise, to use … any invention ….". It went on to state that it applied retrospectively and to any claim in respect of the patent in suit. Falconer J held that the effect of the retrospective authorisation was to take away the plaintiff's cause of action as at the date of the writ. No point was raised on the form of the authorisation.
- The second point is that, in order to enable the United Kingdom to become a member state of the World Trade Organisation and hence the Agreement on Trade-Related Intellectual Property Rights (TRIPs) which forms Annex IC to the Marrakesh Agreement Establishing the World Trade Organisation of 15 April 1994, the 1977 Act was amended in 1999, in particular so as to replace section 48 (compulsory licensing) with sections 48A and 48B. No amendment was made to sections 55-59, however. I shall return to the significance of this point below.
- Section 55 provides, so far as relevant:
- Section 56 contains some interpretative provisions. Subsection (1) makes it clear that a patented invention is one for which a patent has been or is subsequently granted. Subsection (2) contains a partial definition of "services of the Crown". Section 57 contains provisions granting third parties, having rights under a patent whose invention is used pursuant to section 55, the right to recover compensation either as if they were the proprietor or in conjunction with the proprietor. Section 57A gives additional rights to compensation in certain circumstances. Section 58 provides for disputes as to Crown use to be referred to the court. Nothing turns on the details of these provisions.
- Section 59 provides:
- It should be noted that similar Crown use provisions are contained in the Copyright, Designs and Patents Act 1988, the Registered Designs Act 1949 and the Defence Contracts Act 1958. It is not necessary for present purposes to consider those provisions, however.
- Article 31 of TRIPs provides, so far as relevant:
- Three possible interpretations of "authorised in writing by a government department" were canvassed before the judge:
- Before the judge Vodafone supported the third interpretation, while IPCom supported the second. The judge held that the third interpretation was the correct one. On IPCom's appeal SSD contends that the first interpretation is the correct one save that SSD says that an express authorisation to work any patent will suffice.
- In my judgment the third interpretation is not correct. It is not strictly necessary for the purposes of this appeal to decide whether the first or second interpretations is correct, but in my opinion the second interpretation is to be preferred. My reasons are as follows.
- First, there is the language of section 55(1). This states that "any person authorised in writing by a government department may … do any of the following acts in relation to a patented invention without the consent of the proprietor of the patent … and anything done by virtue of this subsection shall not amount to an infringement of the patent concerned [emphasis added]". The judge thought that the third construction was the most natural interpretation of this language. I respectfully disagree. The authorisation must be an authorisation to do acts in relation to a patented invention, not merely an authorisation to do acts.
- Secondly, although section 55(1) extends beyond agents of the Crown, the concept of authorisation is one which is familiar from the law of agency. In that context actual authority may be either express or implied. The usual basis for implication is necessity (as it is in the case of implied terms in contracts). It is difficult to see why section 55(1) should exclude an authorisation to do an act which necessarily infringes a patent. It is equally difficult to see why it should extend to an authorisation to do an act which does not necessarily infringe a patent. I will return to this point below.
- Thirdly, for the reasons explained above, I consider that Dixon, Pyrene and Autogene support the second interpretation. Although the facts of all three cases pre-dated the introduction of the requirement for authorisation in writing, and in the case of Dixon any statutory provision, the reasoning remains persuasive. The judge thought that the case law showed a divergence of judicial opinion between the second and third interpretations, but that is not how I read it.
- Fourthly, the second interpretation has the support of successive editors of Terrell over the course of nearly a century. It is to the judge's credit, as an editor of Terrell since the 16th edition, that he was open-minded and prepared to reach a different conclusion; but the editors' view remains persuasive.
- Fifthly, as counsel for SSD submitted, it is difficult to see why retrospective authorisation under section 55(6) would be necessary if an authorisation to do an act was sufficient. This is illustrated by the Dory case, where the allegedly infringing machines had been purchased by the NHS. It is inherently probable that the purchases were made under one or more written contracts, yet a retrospective authorisation was clearly considered to be necessary.
- Sixthly, I do not accept the submission of counsel for SSD that section 55(7) demonstrates that express authorisation is required. If, as SSD also contends, an authorisation to work any patent would suffice, it might be very difficult, if not impossible, for the relevant Government Department to comply with this obligation. The same is true if an authorisation to do any act would suffice. In my view section 55(7) suggests that the authorisation must either be an express authorisation to work a specific patent or an authorisation to do a particular act which necessarily involves working a specific patent.
- Seventhly, I do not accept the submission of counsel for SSD that express authorisation is required for the Crown to make an informed decision. He postulated an example in which an invitation to tender is put out the performance of which requires the use of a patented invention. Contractor A, who is ignorant of the patent, bids without allowing for the cost of obtaining a licence. Contractor B, who knows of the patent, makes an allowance for the cost as a result of which his bid is higher and he loses the contract to Contractor A. Contractor A having won the contract is then threatened with infringement proceedings. If he were able to plead that he had an implied authorisation for Crown use, he would be able to offload the cost of compensating the patentee onto the Crown, negating his competitive advantage at the bidding stage and possibly even causing the Crown a loss. Counsel submitted that such an outcome cannot have been within the contemplation of the legislature and should accordingly be rejected.
- I do not think that this example supports SSD's interpretation. If performing the contract necessitates working the patented invention, on the second interpretation the authorisation will cover this. Then both A and B would have the benefit of a Crown use defence if they won the contract. Accordingly B would not need a licence from the patentee and would not have to allow for the cost of royalty payments to the patentee. It may be the case that the Crown ends up with higher costs (as a result of compensating the patentee) than it anticipated if it did not know about the patent; but the same would happen if an express authorisation was granted to work any invention and that turned out to cover a patent which the Crown did not know about.
- On the other hand, a variant of this example does support SSD's and IPCom's case that the third interpretation cannot be correct. Suppose a contract is let which can be performed either by working the patent or by not working the patent. Contractor A chooses to work the patent, while Contractor B chooses not to. Both quote the same price, and the contract goes to A. On the third interpretation A has a Crown use defence, and the Crown is landed with the costs of compensating the patentee even though the Crown may not have known of the existence of the patent. By contrast, on the first or second interpretations, the Crown can, once it discovers the patent, make an informed decision as to whether or not to grant a retrospective authorisation to A.
- Eighthly, the judge considered that the third interpretation was "much easier to operate" than the second interpretation since the only question which needed to be answered was whether the act in question was duly authorised. It is true that the third interpretation avoids having to consider the question of necessity, but I do not agree that this means that section 55(1) is easier to operate. On the contrary, for the reasons given above, I consider that the third interpretation places a much greater burden on the Crown than the second.
- Ninthly, the judge considered that the third interpretation was supported by an example postulated by Vodafone in which an act can only be done in one of two ways, each of which infringes a different patent. I agree that it follows from the first and second interpretations that, if the Crown merely authorises the act, then there is no defence of Crown use either way. I do not see, however, why this shows that the third interpretation is to be preferred. On the contrary, it would potentially expose the Crown to a greater liability if the contractor chose to work a patent which was subject to a higher royalty rate than the other. By contrast, the first and second interpretations would enable the Crown, if it chose, expressly to authorise the working of the lower cost patent.
- Tenthly, the judge considered that the burden more fairly rested upon the person authorising the acts than on the person doing them. I disagree with this. In the normal commercial scenario where A buys goods from B, then in the absence of express contractual terms B impliedly warrants, as part of the warranty of quiet possession, that the goods do not infringe third party intellectual property rights: see Microbeads AG v Vinhurst Road Markings Ltd [1976] RPC 19. Thus the burden is on the supplier to ensure that the goods are non-infringing or licensed, not on the purchaser. This makes sense: the supplier is in a position to know what technology it is using, to conduct patent searches and take legal advice, to negotiate for a licence if required and to re-design if necessary. I do not see why the position should be different here if the Crown does not authorise use of the patent either expressly or by necessary implication.
- Counsel for Vodafone emphasised the difficulty, particularly in the context of standardised telecommunications networks, of conducting freedom-to-operate analyses. Patents can be hard to find (although over-declaration of patents as being standard-essential is a much more common problem than under-declaration), and being confident as whether to a particular patent is essential to the operation of a particular standard can be even harder, particularly now that the United Kingdom has embraced infringement by equivalents. I accept that, but I do not see that it supports the third interpretation. It remains the case that suppliers are better placed to conduct such analyses than purchasers, including the Crown. Moreover, as discussed above, the Crown should not be unduly exposed to unforeseen liabilities.
- Eleventhly, we heard a certain amount of argument as to Crown practice with respect to contractual terms. We were informed that, unsurprisingly, the Crown often contracts on terms that either expressly provide that no authorisation is granted under section 55 or require the supplier to indemnify the Crown against any liability under section 55. I do not see that this assists in interpreting the requirement for authorisation, however.
- Twelfthly, I accept the submission of counsel for IPCom that policy considerations support a narrow rather than a broad interpretation of section 55(1): as discussed above, the policy which underpins section 55(1) is one of respect for private intellectual property rights unless State exploitation is in the public interest and in that case the owner of the right is to be notified and compensated.
- Lastly, it is common ground that, if possible, the 1977 Act should be interpreted consistently with TRIPs. I consider that the first and second interpretations of section 55(1) are more consistent with Article 31 of TRIPs than the third. There are a number of aspects to this point.
- It is common ground that section 48A is intended to comply with Article 31. Contrary to the suggestion advanced in Vodafone's skeleton argument, this is irrelevant. What matters is whether section 55 is compliant. Evidently the Government considered in 1999 that section 55 did not require amendment in order to comply with Article 31. The question is whether, on a proper interpretation, it is compliant.
- Article 31(b) requires prior negotiation with the right holder. Vodafone contend that section 55 reflects the two exceptions to Article 31(b): the first being "national emergency or other circumstances of extreme urgency" and the second "public non-commercial use". I will consider these in turn.
- So far as the first exception is concerned, it appears to me that this is primarily implemented by section 59 of the 1977 Act. The effect of section 59 is to widen the class of uses that qualify as services for the Crown in an emergency, and hence enable use of patented inventions to be authorised, including retrospectively. Counsel for Vodafone submitted that the procedure prescribed by section 59 was too slow, but the COVID-19 pandemic has shown that Parliament can approve secondary legislation very rapidly indeed if required.
- In any event, I am not persuaded by Vodafone's argument that the need for authorisations to be granted speedily in some circumstances supports the third interpretation of section 55(1). It seems to me to be entirely neutral. (Although it is immaterial to the issue of construction, I would add that I also do not accept Vodafone's suggestion that the need for urgent authorisation is illustrated by the facts of the present case. The relevant authorisation in the case of MTPAS is the Cabinet Office documentation, which was not issued in circumstances of urgency, but by way of careful advance planning.)
- Turning to the second exception to Article 31(b), this is limited to "public non-commercial use". In my view section 55 extends beyond that, including for example to sales for foreign defence purposes (i.e. of arms to foreign Governments) and the supply of specified drugs: see section 56(2)(a),(b) and (3). Even if MTPAS qualifies as public non-commercial use, as Vodafone contend, that is beside the point.
- To the extent that section 55 extends beyond the two exceptions, the possibility conferred by section 55(6) for retrospective authorisation is inconsistent with Article 31(b). The more broadly section 55(1) is construed, the more inconsistent it is.
- Furthermore, neither of the exceptions to Article 31(b) applies to Article 31(a), which requires authorisation of the use of the subject matter of a patent to be "considered on its individual merits". As IPCom and SSD contend, the third interpretation of section 55(1) is inconsistent with this requirement. SSD contends that only the first interpretation is consistent with it, but I consider that the second interpretation is at least as, if not, more consistent with it given SSD's stance that an express authorisation may be in respect of any patent.
- It follows that I consider that the judge was wrong to conclude that Vodafone had a defence of Crown use in relation to the Annex C mode of operation.
- Vodafone contend that, even if the Annex C, E and F modes of operation fall within the method claims of the Patent, they do not infringe because the extent of Vodafone's use of those modes was de minimis. The judge rejected this contention in respect of all three modes.
- There was no dispute either before the judge or this Court that I had accurately stated the law in Napp Pharmaceuticals Holdings Ltd v Dr Reddy's Laboratories (UK) Ltd [2016] EWHC 1517 (Pat) (the point did not arise on the appeal in that case):
- As counsel for IPCom submitted, what I said in [148] needs to be read in context, the context being consideration of a situation where a process produces products which have a statistical distribution of values of a certain parameter due to inherent variations in the manufacturing process, and the result of that statistical distribution is that 99.99% of the products fall outside the claim.
- In the present case the judge held that Vodafone's acts were not de minimis for the following reasons:
- Before turning to the arguments on the appeal, it is necessary to say a little more about the facts relied on by Vodafone. With regard to Annex C (MTPAS), the judge recorded in paragraph 10 of Annex 2 to the judgment an undisputed calculation by Vodafone that the duration of MTPAS testing (150 hours per year) amounted to 0.000166% of total base station time over the relevant period. As for Annex E (Limited Historical Operation), Vodafone rely upon the fact that this involved eight base stations out of a total of approximately 10,500. Annex F (Anomalous Testing Operation) involved 10 base stations for a five month period.
- On the appeal Vodafone relied, as they did before the judge, on evidence that the Annex E and F modes of operation were inadvertent, in that Vodafone did not know that the relevant base stations had operated in the relevant way until they had made enquiries of their suppliers for the purposes of the proceedings, whereupon Vodafone took steps to ensure that these modes of operation ceased. In my judgment the judge was correct to hold that this was irrelevant. Save to the extent specifically provided in section 60, patent infringement is a strict liability tort. It does not matter whether the alleged infringer deliberately infringed or wrongly thought it had a good defence to a claim for infringement or had no idea that it could be infringing. Furthermore, Vodafone did not contend that they had a defence to IPCom's claims for financial relief on the grounds that they were not aware, and had no reasonable grounds for supposing, that the Patent existed within section 62(1) of the 1977 Act. If Vodafone infringed the Patent because of the way in which equipment purchased from suppliers functions, then Vodafone may have a contractual remedy against the suppliers for the reasons explained in paragraph 161 above.
- Vodafone also relied, as they did before the judge, on evidence that Vodafone made no profit from any of the Annex C, E or F modes of operations. In my judgment this is equally irrelevant. Patent infringement does not depend on making a profit out of the infringement.
- Vodafone also described the acts, as they did before the judge, as "non-commercial". This begs the question of what is meant by "non-commercial" in this context. If it simply means "non-profit making", that is irrelevant. If it refers to the purposes for which the acts were carried out, the judge found that the acts in question were all carried out in connection with the operation of a commercial network. In that sense, they were commercial. Moreover, Vodafone did not contend that they had a defence that the acts had been "done privately and for purposes which are not commercial" within section 60(5)(a).
- Accordingly, it seems to me that Vodafone's case that their acts were de minimis must depend solely upon the scale of the uses in question. In considering this question it is important to bear in mind that the issue here is one of infringement of method claims of a patent. Furthermore, there is no question here of statistical variation of a parameter due to a manufacturing process. Rather, the case concerns the operation of network in a number of different modes. As noted above, there is no dispute that the network did not infringe during normal operation (Annex A). The issue concerns the operation of the network otherwise than during normal operation.
- So far as Annex C (MTPAS) is concerned, the metric relied upon by Vodafone is the percentage of total base station time occupied by MTPAS testing. I do not accept that this is a relevant metric, however. As counsel for IPCom submitted, the whole point of products and processes intended for use in emergency situations, such as fire extinguishers and life jackets, is that one hopes never to have to use them for real. The purpose of testing is to ensure that the product or method can be used if and when an emergency occurs. It is unsurprising in such circumstances that the duration of use for testing purposes is very short compared to the duration of normal use. Moreover, the fact that the method was not used in an actual emergency does not detract from the fact that it was available for use at all times during the relevant period. Accordingly, I agree with the judge's assessment at [221]. Certainly, it was an assessment he was entitled to make.
- In the case of Annex E, the metric relied upon by Vodafone is the number of base stations out of the total. I do not accept that this is a relevant metric either. Each base station is an independent unit which serves a particular cell in the network. The Annex E base stations were configured to transmit the Barring Parameters so as to bar 5% of all access requests. Thus they were configured in a different way to the other base stations in the network. I therefore consider that these eight base stations fall to be considered separately from the others. As such, in my judgment the use was not de minimis.
- In the case of Annex F, Vodafone rely upon the combination of the small number of base stations (10) with the short duration of use (five months). But the so-called Anomalous Testing Operation was a discrete exercise conducted by Vodafone using a specially-created network of just 10 base stations in order to test Vodafone's 5G capability. This exercise therefore falls to be considered separately from the normal operation of Vodafone's 4G network. As such, in my judgment the use was not de minimis.
- Vodafone contend that, if the claims are construed in the manner contended for by IPCom and accepted by the judge, then they are invalid on the grounds that the claimed inventions are obvious in the light of the IS-95 approach of giving access to classes 0-9 by a persistence test, combined with the skilled person's common general knowledge, and specifically their common general knowledge of access barring in GSM/GPRS.
- Before proceeding further, three points should be noted. First, Vodafone pleaded both IS-95 and GSM/GPRS as items of prior art. Secondly, Vodafone disclaimed reliance upon common general knowledge alone. Thirdly, Vodafone advanced a case at trial through the evidence of Mr Bishop that unconditionally amended claim 1 was obvious which involved no less than 14 steps. The judge rejected this case, and a three-step variant of it, for reasons that it is unnecessary to go into because Vodafone do not pursue either case in this Court. Nor do Vodafone pursue the suggestion made in closing submissions at trial that the invention was a mere collocation.
- As Vodafone accept, the squeeze argument which is pursued arose out of Dr Irvine's evidence in cross-examination. Vodafone's position throughout this litigation has been that conditionally amended claim 1 could not be both valid and infringed. As discussed above, a key plank of Vodafone's non-infringement argument is based upon the feature in the claim requiring the subscriber station to be a member of either a "privileged user class" or a "normally privileged user class". Vodafone contend that these are mutually exclusive classes and therefore the claim does not read onto LTE, in which subscriber stations which are members of access classes 11-15 are also members of access classes 0-9. Vodafone say that they had understood Dr Irvine to have agreed with this both in his third report and during cross-examination as to the disclosure of the Patent. During cross-examination as to infringement, however, Dr Irvine gave evidence that in his opinion the claim covered a "privileged" user of the claim who was associated with both a normal access class (0-9) and a special access class (11-15). As discussed above, the Judge accepted this in the context of infringement by LTE, and I consider that he was correct to do so.
- The judge recorded the squeeze argument which Vodafone advanced on this basis at [136] as follows:
- I interpose that it is common ground that, as in LTE, it was compulsory in GSM/GPRS for a member of a special access class (e.g. class 12) also to be a member of a normal access class (e.g. class 7). Vodafone claim that the result of taking these steps would be a system that was functionally identical to LTE: a member of classes 12 and 7 would either bypass the lottery (if class 12 had a GSM access barring "0") or otherwise participate (because of its membership of class 7). Thus if LTE is within the claim, it follows that the claim is bad for obviousness.
- The judge rejected this argument at [137] for the following reasons:
- Vodafone contend that these reasons are either erroneous or do not justify the judge's conclusion. I shall consider them in turn.
- So far as the first reason is concerned, Vodafone submit that this does not support the judge's conclusion. I agree with this. As the judge rightly held, Dr Irvine's evidence on construction was inadmissible. But his evidence on what would have been technically obvious to the skilled person was not only admissible, but described by the judge as helpful. It follows that the judge should at least have taken it into account in reaching his conclusion.
- As for the second reason, Vodafone again submit that this does not support the judge's conclusion. I again agree with this. As discussed above, it is common ground that, in the claim, the privileged and normally privileged classes are mutually exclusive. The judge held the fact that mobiles were members of both access classes 11-15 and access classes 0-9 did not prevent LTE from falling within the claim. If that is correct, then it would not prevent an obvious development of IS-95 which had the same feature from doing so.
- Turning to the third reason, Vodafone submit that this is partly wrong. Although Dr Irvine was discussing LTE, he was explaining why he considered that LTE fell within the claim. In any event, for the reasons discussed in the preceding two paragraphs, this reason does not support the judge's conclusion either.
- As to the fourth reason, Vodafone accept that the court should be cautious before concluding that claimed inventions are obvious over common general knowledge alone since, as a number of judges have pointed out, such attacks risk being unencumbered with inconvenient details which might point to non-obviousness and are particularly prone to hindsight. Counsel for Vodafone relied, however, on what Floyd J said when rejecting such an argument in Nokia v IPCom (cited above) at [116]:
- As counsel for Vodafone pointed out, Vodafone's present argument is squarely based on seeing what methods of access control had been used in the past, and in particular in IS-95 and GSM/GPRS, both of which were pleaded items of prior art. It is not based on an a priori assessment of the problem or upon isolating aspects of the common general knowledge from their surrounding detail. Accordingly, I accept Vodafone's submission that the judge's fourth reason involves a mischaracterisation of their case.
- It is convenient next to consider the judge's sixth reason. Vodafone contend that this criticism is unjustified. The prior art they rely upon had been pleaded; the argument is a squeeze argument, which did not have to be specifically pleaded (although Vodafone had pleaded reliance upon the fact that users were members both of access classes 0-9 and special classes 11-15) or supported by Vodafone's evidence (although Vodafone say it did form part of Mr Bishop's evidence); it arose out of the evidence given by the patentee's own expert during cross-examination; and in those circumstances there was nothing unfair to IPCom in Vodafone advancing it. With respect to the judge, I consider that these points are well founded.
- This leaves the judge's fifth reason. As counsel for IPCom pointed out, obviousness involves a multi-factorial evaluation and therefore this Court is not justified in intervening in the absence of an error of law or principle on the part of the judge: see Actavis Group PTC EHF v ICOS Corp [2019] UKSC 15, [2019] Bus LR 1318 at [78]-[81] (Lord Hodge). If a court concludes that an allegation of obviousness involves hindsight, the court should reject the allegation, since the question is what was obvious without hindsight. In order to attack such an assessment, an appellant must demonstrate that the judge has erred in law or principle.
- Vodafone point out, however, that the judge did not explain why he considered that Vodafone's argument involved hindsight. Furthermore, the judge had previously stated at [16] that "I do not consider that Dr Irvine's evidence was tainted by hindsight". Yet further, he set out Vodafone's summary of Dr Irvine's evidence on the point in issue in [136] without suggesting that Vodafone had mischaracterised Dr Irvine's evidence. Thus Vodafone argue that the assessment is purely conclusory.
- In my judgment the judge's laudable desire to express himself concisely has in this instance led him to state his conclusion without giving any reasons which substantiate that conclusion (other than reasons I have already rejected). It does not necessarily follow that the judge's conclusion was wrong. Rather, it means that this Court must re-revaluate the matter.
- IPCom points out that the judge did not explicitly find that the two steps relied upon by Vodafone were obvious ones for the skilled person to take at the priority date in the light of the prior art relied on and disputes that Dr Irvine accepted this. Despite this, neither side took this Court through all of the relevant cross-examination. In those circumstances, and given the absence of any adverse comment from the judge on Vodafone's summary of what Dr Irvine is said to have accepted, I consider that this Court should proceed on the basis that the judge agreed with Vodafone's summary as recorded by him at [136]; but no more than that.
- More significantly, IPCom contends by a Respondent's notice that the judge's conclusion that conditionally amended claim 1 was not obvious was correct for another reason, namely that the combination of features of IS-95 and GSM/GPRS relied upon by Vodafone would not fall within the claim. In other words, IPCom disputes that there is a squeeze between infringement and obviousness. The basis for this contention is that there is no lottery bypass in the putative system which the skilled person would arrive at by taking the two steps described by the judge at [136]. Rather, the system would involve class barring as in GSM/GRPS. In GSM there is no lottery to bypass, while in GPRS the special users that are not barred go on to do the lottery.
- In my judgment this contention is well founded. Not only did the judge make no finding that these steps would lead to a system in which privileged users bypassed the lottery (indeed, some of the judge's analysis in [131] indicates that further steps would be required), but also Dr Irvine gave evidence that the result would not be the same as the bypass in the Patent. Thus counsel for Vodafone's assertion that the resulting system would be functionally identical to LTE is supported neither by any finding of the judge nor by the evidence of Dr Irvine relied on by Vodafone as the foundation for its case.
- Accordingly I conclude, albeit for somewhat different reasons, that the judge was correct to reject Vodafone's obviousness attack.
- The judge made a declaration as to essentiality as follows:
- If their non-infringement arguments are unsuccessful, Vodafone do not challenge the judge's conclusion as to essentiality, nor do they challenge his decision to make a declaration. Rather, they contend that the declaration made by the judge does not accurately reflect his conclusion in his judgment. Vodafone say that the declaration should be worded as follows:
- Leaving aside some minor and inconsequential differences, the key difference between what Vodafone seeks and the declaration made by the judge is that the former includes the statement "If and insofar as the option … is being exercised". Vodafone contend that their version correctly reflects the judge's conclusion set out in paragraph 87 above.
- There was a rather enervating dispute both before the judge and this Court as to the admissibility and relevance of evidence given by both parties' solicitors directed to this question which was adduced at the form of order hearing. For my part I doubt that either side's evidence was admissible. Be that as it may, it seems to me that the form of the declaration was a matter for the discretion of the judge. Unless he made some error of principle in framing the declaration then I do not consider that this Court should interfere. No such error has been identified. The most that is suggested is that Vodafone's form of declaration more accurately reflects the underlying judgment. The judge thought otherwise. Moreover, as the judge pointed out, if there is any doubt or dispute as to the meaning and effect of the declaration, then reference may be made not only to the judgment, but also to the relevant section of the standard.
- For the reasons given above, I would dismiss Vodafone's appeal. I would dismiss IPCom's appeal on "set up to send", but allow its appeal on Crown use.
- I agree.
- I have had the benefit of reading Arnold LJ's comprehensive judgment. I have found the interpretation of "access right" more difficult than my colleagues; but otherwise I agree with his compelling analysis.
- Until the decision of the Supreme Court in Actavis UK Ltd v Eli Lilly and Co [2017] UKSC 48, [2017] RPC 21 the extent of the protection given to a patentee by a patent claim was regarded as a unitary process of construction. In applying principles of construction to patents, the court often found it useful to ask itself the three Improver questions (or Protocol questions) which could have the effect of expanding the ordinary meaning of the claim: see Improver Corpn v Remington Consumer Products Ltd [1990] FSR 181. The construction of a written instrument is a commonplace in our courts. Despite the differences between patents and contracts, the underlying principles are broadly the same. In Trump International Golf Club Scotland Ltd v Scottish Ministers [2015] UKSC 74, [2016] 1 WLR 85 at [33] Lord Hodge said:
- In Actavis, the patent claimed a medicament manufactured with a sodium salt. The question was whether a similar medicament, manufactured with a potassium salt, would infringe the patent. The Supreme Court held that, contrary to what had previously been supposed, the scope of protection given by a patent claim involved two separate steps. The first step was to decide the "normal" meaning of the claim. At [53] Lord Neuberger (giving the unanimous judgment of the court) described the previous approach as one in which the courts had applied an "extended version of the ordinary concept of "construction" or "interpretation." At [54] he proposed a modified way of approaching the scope of patent claims:
- There are, therefore, now two separate questions. I agree with the suggestion made by Mr Richard Meade QC (sitting as a judge of the Patents Court) that the overall process is best described as ascertaining "claim scope" rather than as "claim construction"; since it is only the first of the two steps that is claim construction properly so-called: Fisher and Paykel Healthcare Ltd v ResMed Ltd [2017] EWHC 2748 (Ch).
- In referring to the "normal" meaning of the claim, or the ordinary concept of construction, Lord Neuberger said at [58]:
- Wood was, of course, a case about the interpretation of a contract.
- Accordingly, what the claims mean is to be determined in accordance with the normal principles of interpretation applicable to any written instrument. Normal interpretation does not, however, mean a literal interpretation. It includes considerations of purpose and context: Icescape Ltd v Ice-World International BV [2018] EWCA Civ 2219, [2019] FSR 5 at [60]. Under normal principles of interpretation "sodium" could not be construed as "potassium". But the infringement claim in Actavis succeeded because of the newly introduced principle of "equivalence". I do not consider that in Actavis the Supreme Court intended to extend the scope of protection afforded to the patentee by interpretation. On the contrary, because of the division of the process into two separate steps, the Supreme Court, if anything, had narrowed the scope of protection as a matter of interpretation, because the previous Improver or Protocol questions now form part of step 2. Indeed, as Arnold LJ has pointed out at [99], in describing the role of equivalents, Lord Neuberger began by asking whether the alleged infringement fell within the "literal" meaning of the claim. The overall extent of the protection given by a patent claim may have been expanded, but that is because the new approach involves two separate steps.
- At the end of the day, in step 1 a "normal" interpretation must be one which the words of the claim are capable of bearing. There is no need to distort their meaning; not least because the patentee may still succeed in establishing infringement through the doctrine of equivalents.
- In this appeal IPCom advanced no case on equivalents in relation to the integer dealing with the phrase "access right". So the scope of that expression depends entirely on step 1: the "normal" interpretation. As Arnold LJ has said at [67] the words "access right" are ordinary English words. So I begin by considering what, as ordinary English words, they would be understood to mean. Mr Nicholson QC submitted, and the judge accepted, that an "access right" could be either positive or negative. It is perfectly true, as Arnold LJ says at [69], that intellectual property rights are often characterised as negative rights. They are negative rights in the sense that they are rights to stop other people from doing things (working the invention, copying a literary work etc). But the question is not whether, in the abstract, a right can be positive or negative. It is whether there can be a negative access right. I regret that I simply do not understand the concept of a negative right of access. Patent claims have often been likened to boundary markers intended to show third parties "the exact boundary of the area within which they will be trespassers": Electric and Musical Industries Ltd v Lissen Ltd (1938) 56 RPC 23, 39. Let me pursue the analogy a little further.
- Suppose that in order to enter a building you need a card which can be read by an electronic card reader. Some people have the cards, but others do not. The building owner decides who is entitled to a card and who is not. The building owner's right could, I suppose, be described as a negative right in the sense that he can stop people from coming in without a card; and he can decide who gets a card and who does not. But it is a real right. It could also be described as a positive right, in the sense that the building owner can also decide (positively) who is allowed to cross the boundary without becoming a trespasser. A person who has a card can fairly be described as having an access right. But what I find impossible to accept is that a person who does not have a card has a negative access right. You might just as easily say that I have a negative right of access to 10 Downing Street; or to the MoD's top secret laboratories at Porton Down. To have no right of access is not a right of any kind. To describe it as a "negative right" is, in my judgment, a meaningless oxymoron. So here: I fail to see how a person who has been denied access to the system because he is neither privileged nor has "won the lottery" can be said to have any access right at all as a matter of ordinary English. Even though the patent is dealing with a logic flow, I still find it difficult to see how a right of access can encompass no right of access at all as a matter of ordinary English.
- That, at any rate, is the meaning of that phrase that strikes me. Would the explanation of the invention contained in the specification cause the skilled reader to adopt a different meaning? At [68] Arnold LJ has cited a number of passages from the specification that bear on the question. Those passages do suggest that the method described in the specification both grants and blocks access. But does that lead to the conclusion that the claim means what Mr Nicholson says it means; or is it a pointer to possible success on an unpleaded and unargued case of equivalents?
- I have found this a very difficult question to decide. I see the force of what Arnold LJ says at [70]. In particular his statement that the effect of Vodafone's construction is that the method is only performed when access is granted may lead to the conclusion that in the real world the claimed method is never performed at all. Although I have my doubts whether this is impermissibly stretching the "normal" interpretation of the claim, I do not push my doubts to a dissent.
- Accordingly, I agree with Arnold LJ's proposals for the disposition of the appeals.
Covid-19 Protocol: This judgment was handed down remotely by circulation to the parties' representatives by email, release to BAILII and publication on the Courts and Tribunals Judiciary website. The date and time for hand-down is deemed to be at 10:30am on 19 February 2021
Lord Justice Arnold:
Contents
Topic Paragraphs
Introduction 1-6
The skilled person 7
Common general knowledge 8-22
The Patent 23-42
The conditionally amended claims 43-46
The inventive concept 47-52
Construction of the claims 53-73
Extension of protection 74-80
Essentiality and infringement 81-119
Crown use 120-173
De minimis 174-185
Obviousness 186-205
Form of declaration 206-209
Disposition 210
Introduction
The skilled person
Common general knowledge
Contention on a shared channel
The "lottery"
Access classes
Transmission capacity
Class barring in GSM/GPRS
i) access class 15 for PLMN staff ("PLMN" stands for Public Land Mobile Network and is just the network operator);
ii) access class 14 for the emergency services;
iii) access class 13 for public utilities (e.g. water/gas suppliers);
iv) access class 12 for the security services; and
v) access class 11 for PLMN use (for example, for test mobiles while setting up a cell).
IS-95
The Patent
"[0007] … the inventive subscriber station, and the inventive telecommunications system with the features of the independent claims have … the advantage that, with the information signals, access authorization data are transmitted to at least one subscriber station, that, upon receipt of the access authorization data in an evaluation unit of the at least one subscriber station, a check is carried out as to whether the access authorization data comprise an access threshold value, wherein the access threshold value is compared to a random number or a pseudo-random number, and that the right of access to a telecommunications channel is granted to the at least one subscriber station on the basis of the comparison result, preferably on the condition that the random number or a pseudo-random number is greater than or equal to the access threshold value. It is advantageous if in this manner a random distribution of the access authorization to this telecommunications channel is produced for one or more subscriber stations. This access control demands a minimum of transmission capacity for transmitting the information signals, since it is effected merely by transmitting the access threshold value.
…
[0009] It is particularly advantageous that checking is carried out in the evaluation unit of the at least one subscriber station as to whether the access authorization data comprise access authorization information with access class information for at least one prescribed user class, with, in this case and on the assumption that the at least one subscriber station is associated with the at least one prescribed user class, access to a telecommunications channel being granted to the at least one subscriber station on the basis of the access class information for this user class. This permits subscriber stations of a prescribed user class to be authorized to use the telecommunication even if the random distribution by means of access threshold value would not authorize them to access this telecommunications channel. Thus, by way of example, subscriber stations for emergency services, such as the police or the fire brigade, can be associated with such a prescribed user class and can then access the telecommunications channel with priority irrespective of the random distribution by corresponding access threshold value information.
…
[0013] Another advantage is that access to this telecommunications channel is enabled for the at least one subscriber station on the basis of the volume of message traffic on at least one telecommunications channel. This make it possible to achieve an optimum distribution of the resources of the telecommunications network over the subscriber stations with the best possible use of the transmission capacity."
"It is possible to prevent the RACH 30 from being overloaded by virtue of the network operator restricting, in a targeted manner, access to the RACH by the individual mobile stations 5, 10, 15, 20. In this case, access to the RACH can be permitted, for example, only for particular user classes of mobile stations on a temporarily or permanently privileged basis. In line with the described exemplary embodiments in figure 1, a first user class 35 is provided which comprises the first mobile station 5 and the second mobile station 10. In addition, a second user class 40 is provided which comprises the third mobile station 15 and the fourth mobile station 20. Provision may also be made for a separate user class to be provided for each mobile station, however. It could also be possible to provide user classes containing a different number of mobile stations. It is also possible to provide more than two mobile stations in one user class. The network operator can then enable access to the RACH for the individual mobile stations on the basis of their association with one of the two user classes 35, 40. This means that the two mobile stations 5, 10 in the first user class 35 are assigned equal rights for sending on the RACH. Similarly, the mobile stations 15, 20 in the second user class 40 are also assigned equal rights for sending on the RACH."
i) If the associated access class bit for the user class to which the mobile belongs is 0, the mobile can access the RACH irrespective of the access threshold value. It does not have to do the lottery.
ii) Conversely, if the relevant associated access class bit is 1, the mobile has to participate in the lottery using whatever access threshold value has been transmitted.
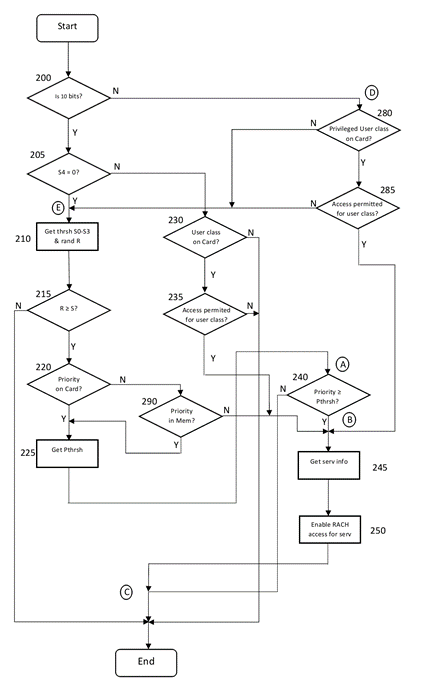
"At program point 280, the evaluation unit 60 has recognized that a bit pattern having a bit length of 13 bits has been received, and checks whether the access authorization card 75 stores an affiliation of the associated mobile station to a user class. In addition a check is carried out at program point 280 to determine whether the user class belongs to a first group of user classes or to a second group of user classes. The first group of user classes is also referred to as normally privileged below. The second group of user classes is also referred to as privileged hereafter."
i) If the answer is yes (i.e. there is a "privileged" user class on the card), then the system goes to box 285 and asks whether access is permitted for that user class (as the specification puts it, "whether the user class ascertained for the mobile station is authorized for access to the RACH 30").
ii) If the answer is again yes, then the system proceeds to boxes 245 and 250, whereby the "privileged" user whose access is permitted is given access to the RACH.
iii) If the answer to diamond 280 is no, either because there is no user class stored on the card or because the user is "normally privileged", then the system goes to point E, just above box 210. It then has to perform the lottery in order to see if it is permitted access.
iv) Similarly if the answer to diamond 285 is no (i.e. the user is in a "privileged" class, but access is not permitted for that particular privileged class), the same path is followed.
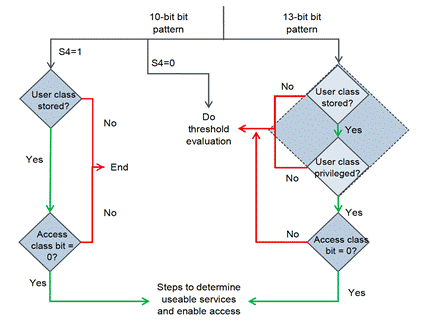
"The information signals are transmitted from the base station 100 to the mobile station 5, 10, 15, 20 at prescribed times, preferably at regular intervals. The network operator can, in line with the method described, permit or block access to the RACH for the individual mobile stations 5, 10, 15, 20 on the basis of the volume of message traffic in a telecommunications network and hence on the basis of an expected utilization level of the RACH 30. Since the volume of message traffic in the telecommunications network varies over time, the expected utilization level for the RACH 30 also changes over time, so that the various mobile stations 5, 10, 15, 20 are, in general, granted access to the RACH at different times using correspondingly altered bit pattern configuration."
The conditionally amended claims
"[1] Method for ascertaining an authorization for access toat least onea telecommunication channel (30) of a telecommunication network by a subscriber station (5, 10, 15, 20),
[2] wherein information signals sent by a base station (100) with access threshold value and access class information as access authorization data (55) are received by a transmission/reception unit (65) of the subscriber station (5, 10, 15, 20),
[3] wherein the access authorization data (55) are transmitted as a bit pattern (55),
[4] wherein the access authorization data comprise access class bits (Z0, Z1, Z2, Z3) as well as access threshold bits (S3, S2, S1, S0),
[5] wherein each access class bit represents one user class and wherein each of the user classes is assigned one access class bit,
characterized in that
[6] an evaluation unit (60) of the subscriber station (5, 10, 15, 20) has a check (280) performed in it to determine whether an access authorization card (75) of the subscriber station (5, 10, 15, 20) stores an association between the subscriber station (5, 10, 15, 20) and a privileged user class (35, 40) or stores an association of the subscriber station (5, 10, 15, 20) to a normally privileged user class (35, 40), in which it is checked whether an association of the subscriber station (5, 10, 15, 20) to a user class (35, 40) is stored on the access authorization card (75) and whether the user class is a normally privileged user class or a privileged user class,
[7] ifthis is the casean association of the subscriber station (5, 10, 15, 20) to a privileged user class (35, 40) is stored on the access authorization card (75), then the evaluation unit (60) takes the access classinformationbit (Z0, Z1, Z2, Z3) which corresponds to the privileged user class as a basis for checking whether the privileged user class (35, 40) ascertained for the subscriber station (5, 10, 15, 20) is authorized for access to theat least onetelecommunication channel (30) irrespective of an access threshold value evaluation,
[8] if this is not the case because an association of the subscriber station (5, 10, 15, 20) with a privileged user class (35, 40) is stored on the access authorization card (75) but the determined privileged user class (35, 40) is not authorized to access the telecommunication channel (30) independent of an access threshold evaluation or if the access authorization card (75) stores no association with a privileged user class (35, 40) because an association of the subscriber station (5, 10, 15, 20) to a normally privileged user class is stored on the access authorization card (75) or no association to a user class (35, 40) is stored on the access authorization card (75), then the evaluation unit (60) performs the access threshold value evaluation with the following steps:
[9](i) the evaluation unit (60) ascertains an access threshold value (S) from the access threshold bits (S3, S2, S1, S0) of the access authorization data (55),
(ii) draws a random or pseudo-random number (R),
(iii) compares the access threshold value (S) with the random or pseudo-random number (R), and
(iv) allocates an access right for theat least onetelecommunication channel (30) to the subscriber station (5, 10, 15, 20) on the basis of the comparison result,
[10] wherein the telecommunication channel is a random access channel."
"Method according to one of the preceding claims, characterized in that access to theat least onetelecommunication channel (30) is permitted on a temporarily or permanently privileged basis only for particular user classes (35, 40) of subscriber stations (5, 10, 15, 20)."
"Telecommunication system having
a telecommunication network that is in the form of a mobile radio network and that providesat least onea telecommunication channel (30),
at least one base station (100) that is set up to send information signals with access threshold value and access class information as access authorization data (55) as a bit pattern,
wherein the access authorization data comprise access class bits (Z0, Z1. Z2, Z3) as well as access threshold bits (S3, S2, S1, S0) wherein each access class bit represents one user class and wherein each of the user classes is assigned one access class bit, and each access class bit indicates whether the user class to which the access class bit corresponds is authorized to access the telecommunication channel independent of an access threshold evaluation,
and at least one subscriber station (5, 10, 15, 20) according to Claim 612,
wherein the telecommunication channel is a random access channel."
The inventive concept
"the key inventive concept … is the combination of two different access regimes into one system: a bypass mechanism available to a group of privileged users only; and a threshold evaluation for those users not granted access via this bypass mechanism. The proportion of privileged users that are granted bypass access can be changed dynamically by way of the access class information broadcast by the network, and the proportion of the remaining users who will successfully gain access using the threshold evaluation can be controlled by way of the access threshold value broadcast by the network. This system combines the flexibility of a threshold with a bypass mechanism so that high priority mobiles in privileged user classes can gain direct access to RACH and escape the constraint of the threshold, all with limited signalling overhead."
Construction of the claims
Each of the user classes is assigned one access class bit
A normally privileged user class or a privileged user class
Access right
Set up to send
Extension of protection
"Method for ascertaining an authorization for access to at least one telecommunication channel (30) of a telecommunication network by a subscriber station (5, 10, 15, 20),
wherein information signals sent by a base station (100) with access threshold value and access class information as access authorization data (55) are received by a transmission/reception unit (65) of the subscriber station (5, 10, 15, 20)
characterized in that
an evaluation unit (60) of the subscriber station (5, 10, 15, 20) has a check (280) performed in it to determine whether an access authorization card (75) of the subscriber station (5, 10, 15, 20) stores an association between the subscriber station (5, 10, 15, 20) and a privileged user class (35, 40),
if this is the case, then the evaluation unit (60) takes the access class information (Z0, Z1, Z2, Z3) as a basis for checking (285) whether the privileged user class (35, 40) ascertained for the subscriber station (5, 10, 15, 20) is authorized for access to the at least one telecommunication channel (30) irrespective of an access threshold value evaluation,
if this is not the case or if the access authorization card (75) stores no association with a privileged user class (35, 40), then the evaluation unit (60) performs the access threshold value evaluation with the following steps:
(i) ascertains an access threshold value (S) from the access authorization data (55),
(ii) draws a random or pseudo-random number (R),
(iii) compares the access threshold value (S) with the random or pseudo-random number (R),
and
(iv) allocates an access right for the at least one telecommunication channel (30) to the subscriber station (5, 10, 15, 20) on the basis of the comparison result."
"Vodafone did put forward a fictional example which they said showed that the scope of protection had been extended. This was a notional class 16 user 'that is not Privileged and not required to do the lottery'. But no reason was given as to why the user in the fictional example was not required to do the lottery and I do not consider the example to be a possible one."
Essentiality and infringement
"ac-BarringForSpecialAC
Access class barring for AC 11-15. The first/leftmost bit is for AC 11, the second bit is for AC 12, and so on.
ac-BarringFactor
If the random number drawn by the UE [User Equipment i.e. mobile] is lower than this value, access is allowed. Otherwise the access is barred. The values are interpreted in the range (0,1): p00 = 0, p05 = 0.05, p10 = 0.10,…, p95 = 0.95. Values other than p00 can only be set if all bits of the corresponding ac-BarringForSpecialAC are set to 0."
i) Does the SIB2 block include ac-BarringForSpecialAC and ac-BarringFactor barring parameters?
ii) If yes:
a) Does the SIM card on the mobile have a valid access class between 11 and 15; and if yes:
b) For at least one of those valid access classes on the SIM between 11 and 15, is the corresponding bit in the ac-BarringForSpecialAC set to 0?
c) If yes to both (a) and (b), consider access to the cell as not barred.
iii) If the SIB2 block includes barring parameters and either 2(a) or 2(b) is not satisfied, do the lottery and compare the result to the value indicated by ac-BarringFactor. Winners are considered not barred and losers are considered barred.
iv) If the SIB2 block does not include barring parameters, consider the cell as not barred.
Access class bit
Privileged or normally privileged
Access right
One check rather than two
"i) Notwithstanding that it is not within the literal [i.e. normal] meaning of the relevant claim(s) of the patent, does the variant achieve substantially the same result in substantially the same way as the invention, i.e. the inventive concept revealed by the patent?
ii) Would it be obvious to the person skilled in the art, reading the patent at the priority date, but knowing that the variant achieves substantially the same result as the invention, that it does so in substantially the same way as the invention?
iii) Would such a reader of the patent have concluded that the patentee nonetheless intended that strict compliance with the literal meaning of the relevant claim(s) of the patent was an essential requirement of the invention?"
Set up to send
"1 Upon receipt of an MTPAS notice, a Vodafone engineer will first log into Vodafone's Network management software (LIMA).
2. In LIMA, the operator maps the location provided by the Police Gold Commander, and identifies the relevant base stations in the vicinity of the event.
3. The operator then selects the access classes to be barred (ensuring classes 11-15 are left unaffected), and networks (2G, 3G, 4G) to be altered.
4. LIMA creates scripts which automate the configuration changes that are required in order to implement the MTPAS response, as determined by the operator. The scripts created by LIMA are loaded onto the operations support system(s) ("OSS") for the relevant base stations (each supplier provides its own proprietary OSS – the MTPAS response may involve configuration changes in one or several OSS systems).
Without LIMA, an engineer would have to manually log in to each relevant OSS to make the changes necessary to cause a change of the settings on each base station (separately). The changes LIMA makes are to the settings/configuration of the relevant OSS
5. Based on the configuration changes caused by LIMA, each relevant OSS sends commands causing configuration changes in each relevant base station. Once the various configuration changes are achieved, the relevant base stations commence transmitting the parameters necessary to implement MTPAS (being the Barring Parameters prior to Vodafone's workaround).
6. Once MTPAS has been invoked, the operator activates call terminate to clear voice and data sessions off sites (that is, to halt all ongoing use of the network by users.
7. The operator must then access the relevant OSS and perform checks on a selection of the cells impacted to ensure MTPAS has been implemented."
I should explain that a "script" in this context is a set of instructions.
"Vodafone's evidence as to how it changed the settings of its LTE base stations was given by Mr White … Essentially Vodafone uses a software control management tool called LIMA to change the relevant settings. LIMA works by generating scripts and loading them on to the base station supplier's proprietary operations support system (OSS) software. The scripts themselves are activated using a graphical user interface on which the user identifies the area to which access control is to be applied (eg the area of the emergency) and the technologies (4G, 3G, 2G) which are relevant. LIMA then generates the relevant scripts based on the user inputs and the cha[n]ges are then automatically applied, via the relevant supplier's OSS software, to all LTE base stations providing coverage in the relevant area."
"103. … claim language of the means plus function type, and I regard 'virtual body modelling apparatus' as an example of that type, is generally taken by the granting authority (the EPO) to be read as means suitable for carrying out the function. That is a good reason on its own to interpret such words in that way.
104. … The fact that a general purpose computer can be programmed to become a virtual body modelling apparatus does not mean that a general purpose computer is a virtual body modelling apparatus nor is it an apparatus suitable for virtual body modelling. It is not. If the right software was installed in the computer but the computer was switched off then that might well be apparatus suitable for virtual body modelling but that is a different point."
"I will start with direct infringement under s60(1). For this purpose I take it that a Wii system with a Balance Board [an item of hardware] running Island Cycling [game software] is an apparatus within claim 1. The pleadings include an allegation that sale of a Wii in the UK is sale of a product within claim 1. I reject that argument. A Wii console sold by Nintendo to customers is not, in the state it is sold, an apparatus within the claim 1. The game software is available on optical disks which are placed in the Wii console in order to play the game. To be within claim 1 it seems to me that the relevant disk, such as a disk carrying the Island Cycling software, at least has to have been inserted into the Wii unit and a Balance Board has to be connected. In that state, whether the unit is switched on or switched off, it seems to me that the claim is satisfied on the assumption I have made."
"225. … changing a base station from one which does not operate an infringing method … into one which does, is not as simple as choosing whether or not to supply power to it. Assume for the moment that the base station is not transmitting any barring parameters. Now assume that the operator wants to transmit the barring parameters for purposes of access control. The fact evidence established that making the change was not a simple matter of supplying power. On the contrary Vodafone's evidence shows that the change requires reprogramming the base station software.
226. IPCom submitted that the reprogramming was akin to flicking a switch. I disagree. I agree with IPCom that the extent of the reprogramming might vary between what Mr Bishop accepted was quite a trivial change (eg a change to the base station software which reads the configuration file, if one has the base station software source code) to a wholesale rewrite of the relevant software, but the fact remains that until the additional programming is done – however extensive or otherwise that additional programming is – the base station does not send the barring parameters. Nor is it adapted or configured to send them. On the contrary, it is adapted and configured not to send the barring parameters."
"… I accept that if the LTE network is in such a state that it merely needs power in order to operate access control as per section 5.3.3.11, then it is 'set up to send' and hence acts done in relation to that network will infringe unconditional claim 13. Unconditional claim 13 is only 'essential' when the network is in this state. Conversely if the LTE network requires some form of adaptation, configuration, or additional programming going beyond the mere supply of power then it is not 'set up to send' and acts done in relation to it will not infringe unconditional claim 13."
Crown use
MTPAS
i) Vodafone are authorised by the Cabinet Office in writing to operate MTPAS;
ii) it is technically possible to comply with MTPAS requests without infringing the Patent; and
iii) during the period of time which is relevant for infringement purposes, Vodafone never received an actual MTPAS request, but they tested their system regularly to ensure that they were in a position to comply with any such request.
The legislative history and previous case law
"… if there was any intention of handing over, with the contract, by others, to supply what the Crown did not think it convenient to manufacture for itself; the power and authority to the contractors of providing themselves with patented articles for that purpose without obtaining a license from the patentee, or without purchasing them from the patentee—I apprehend that if that idea had crossed anybody's mind in framing this invitation to tender, we should have found some reference to patents in it, whereas we find none; we find only a contract to deliver a certain article patented or unpatented."
"I cannot help thinking that, whether the Crown should or should not, in any particular case, desire to take advantage of that immunity, must be a question upon which the Crown is entitled to exercise its discretion, and therefore that any bare contract (supposing that this were one of that character, which I have already pointed out I do not think it is) with an agent to do the work, if the Crown says nothing to the effect that he is to do it without reference to a patentee's rights, will not be sufficient to shew that the Crown was exercising such an election, and consequently the agent, without such express authority, would have no right to infringe the patent. My Lords, I say that with some hesitation, because my noble and learned friend on the woolsack appeared to think otherwise."
(Despite what Lord Penzance said in the last sentence quoted, Lord Cairns LC's speech was silent on this point; he may have been referring to something the Lord Chancellor said during the course of argument.)
"… it was competent for the contractor to have fulfilled his agreement to the letter by paying for the license of the patentee; and the contract does not, on any construction of it, expressly or implicitly declare that the Crown designed or directed the dispensing with that license. The order 'to provide and deliver' involved neither requirement nor approval of illegality, and cannot be assumed to have been issued with the desire that the contractor should act without the permission of the patentee, and therefore, so far as he was concerned, in fraud of individual right and in contravention of the law. Surely, the contrary assumption, if any, should be made. If the work could be done in one of two ways—legally or otherwise—ought we to suppose that the legal mode was not contemplated, in the absence of clear words forbidding it? But there are no such words."
"Nor is it like the case of a direct order to a contractor to do an unlawful act, to the injury of another person. Here there is no order to infringe any patent; and it cannot be inferred that this would have been intended or authorized by a private person entering into this contract, the use of patented articles or patented processes being, in the ordinary course of business, a thing which may be lawfully obtained in the proper market, just as any necessary materials might be, which the manufacturer, taking the contract, might not himself have in stock."
"Patent to bind Crown.
(1) A patent shall have to all intents the like effect as against Her Majesty the Queen, her heirs and successors, as it has against a subject.
(2) But the officers or authorities administering any department of the service of the Crown may, by themselves, their agents, contractors, or others, at any time after the application, use the invention for the services of the Crown on terms to be before or after the use thereof agreed on, with the approval of the Treasury, between those officers or authorities and the patentee, or, in default of such agreement, on such terms as may be settled by the Treasury after hearing all parties interested."
"… the Crown could use by its servants or agents any invention, notwithstanding that Letters Patent had been granted in respect of it, without the consent and notwithstanding the objection of the patentee, and, of course, without having to obtain any licence or make payment of any royalty. This right, however was held not to extend to persons who contracted with the Crown under such circumstances as that they could fulfil their contract by either not using a patented invention, or by using a patented invention. Dixon v. London Small Arms Company (1 App. Cas. 632) was referred to on this point, and especially what was said by Lord O'Hagan on page 658:- 'If the work could be done in one of two ways legally, or otherwise, ought we to suppose that the legal mode was not contemplated in the absence of clear words forbidding it?'"
"[Counsel for the plaintiff] is quite right in saying that the contract does not, in express terms, oblige the Defendants to manufacture the Plaintiffs' patented fire extinguisher. On the other hand, the facts are that the Ministry of Munitions entered into this contract with reference to that extinguisher, and to that extinguisher alone, and the tender which was signed … was in fact a tender for the manufacture of the Plaintiffs' patented extinguisher. The model of the Plaintiffs' machine was produced to Mr. Webb, and he was asked to tender for the making of a machine on that model, and … the prices [were] arranged after bargaining in reference to that very model.
It is not to be wondered at that contracts entered into at the time when this contract was entered were possibly not of the best draughtsmanship … I hold that, notwithstanding the particular wording of this contract, it was a contract which compelled the Defendants to copy as closely as they could the Plaintiffs' patented invention. I further come to the conclusion that it was the intention that the Defendants were not bound to obtain the leave of the Plaintiffs to make their machine …
In these circumstances I hold that this agreement was one which, within the exception admitted by [counsel for the plaintiff], compelled the manufacture of this particular machine without obtaining the leave or licence of the Patentee. In those circumstances … I unhesitatingly hold that the Defendants were contractors with the meaning of Section 29 …."
"Right of Crown to use patented inventions.
(1) A patent shall have to all intents the like effect as against His Majesty the King as it has against a subject:
Provided that any Government department may, by themselves or by such of their agents, contractors, or others as may be authorised in writing by them at any time after the application, make, use or exercise the invention for the services of the Crown on such terms as may, either before or after the use thereof, be agreed on, with the approval of the Treasury, between the Department and the patentee, or, in default of agreement, as may be settled in the manner hereinafter provided. And the terms of any agreement or licence concluded between the inventor or patentee and any person other than a Government department, shall be inoperative so far as concerns the making, use or exercise of the invention for the service of the Crown:
Provided further that, where an invention which is the subject of any patent has, before the date of the patent, been duly recorded in a document by, or tried by or on behalf of, any Government department, (such invention not having been communicated directly or indirectly by the applicant for the patent or the patentee), any Government department, or such of their agents, contractors, or others, as may be authorised in writing by them, may make, use and exercise the invention so recorded or tried for the service of the Crown, free of any royalty or other payment to the patentee, notwithstanding the existence of the patent. If in the opinion of the department the disclosure to the applicant or the patentee, as the case may be, of the document recording the invention, or the evidence of the trial thereof, if required, would be detrimental to the public interest, it may be made confidentially to counsel on behalf of the applicant or patentee, or to any independent expert mutually agreed upon.
(2) In case of any dispute as to the making, use or exercise of an invention under this section, or the terms therefor, or as to the existence or scope of any record or trial as aforesaid, the matter shall be referred to the court for decision, who shall have power to refer the whole matter or any question or issue of fact arising thereon to be tried before a special or official referee or an arbitrator upon such terms as it may direct. The court, referee, or arbitrator, as the case may be, may, with the consent of the parties, take into consideration the validity of the patent for the purposes only of the reference and for the determination of the issues between the applicant and such Government department. The court, referee, or arbitrator, further in settling the terms as aforesaid, shall be entitled to take into consideration any benefit or compensation which the patentee, or any other person interested in the patent, may have received directly or indirectly from the Crown or from any Government department in respect of such patent.
..."
"It is submitted that the authorisation in writing, required for the first time by the Act of 1919, need not refer explicitly to the patent in question, but may be inferred from the terms of the written contract as was done in Pyrene Co., Ltd, v. Webb Lamp Co. (37 R.P.C. 57) … Provided, therefore, the contract leaves no doubt as to the article which is to be made or the process which is to be used in making it, no specific reference to the patent need appear in it and, indeed, the officers of the department and the contractors may be in ignorance of the existence of the patent."
"In my judgment, the Section is primarily an agency section, that is to say, protection is afforded to the Government department, and to any person or persons, contractors or others, who are acting as agents for, or by the express or implied authority of, a Government department. In each case, it will have to be ascertained … whether the acts of the Defendant Company in that particular case were acts done for the purposes of the Crown, and with the authority, or by the direction, of the Crown. In that case, they will not be liable; but where the acts that have been done have not been done by virtue of some express or implied authority from the Crown, then it seems to me they will be liable."
"It is submitted that such written authorisation need not be directed specifically to the use of the particular patent concerned, and that a written authorisation or requirement of a department that a contractor should supply apparatus of a certain type would be sufficient if it were in fact impossible for the contract to supply such apparatus without infringing the patent concerned (c), that is to say, that the only difference made in this respect by the Act of 1919 is that the authorisation should be in writing and not that any greater or more specific degree of authorisation is required."
The authority cited at c for this statement was Pyrene, and the editors proceeded immediately to quote at length from Autogene. The statement of the law prior to the citation was repeated with only slight modifications in wording in subsequent editions of Terrell down to the 18th edition (2016, edited by Sir Colin Birss and others).
The current statutory provisions
"Use of patented inventions for services of the Crown.
(1) Notwithstanding anything in this Act, any government department and any person authorised in writing by a government department may, for the services of the Crown and in accordance with this section, do any of the following acts in the United Kingdom in relation to a patented invention without the consent of the proprietor of the patent, that is to say—
(a) where the invention is a product, may—
(i) make, use, import or keep the product, or sell or offer to sell it where to do so would be incidental or ancillary to making, using, importing or keeping it; or
(ii) in any event, sell or offer to sell it for foreign defence purposes or for the production or supply of specified drugs and medicines, or dispose or offer to dispose of it (otherwise than by selling it) for any purpose whatever;
(b) where the invention is a process, may use it or do in relation to any product obtained directly by means of the process anything mentioned in paragraph (a) above;
…
and anything done by virtue of this subsection shall not amount to an infringement of the patent concerned.
(2) Any act done in relation to an invention by virtue of this section is in the following provisions of this section referred to as use of the invention; and "use" in relation to an invention, in sections 56 to 58 below shall be construed accordingly.
(3) So far as the invention has before its priority date been duly recorded by or tried by or on behalf of a government department or the United Kingdom Atomic Energy Authority otherwise than in consequence of a relevant communication made in confidence, any use of the invention by virtue of this section may be made free of any royalty or other payment to the proprietor.
(4) So far as the invention has not been so recorded or tried, any use of it made by virtue of this section at any time either;
(a) after the publication of the application for the patent for the invention; or
(b) without prejudice to paragraph (a) above, in consequence of a relevant communication made after the priority date of the invention otherwise than in confidence;
shall be made on such terms as may be agreed either before or after the use by the government department and the proprietor of the patent with the approval of the Treasury or as may in default of agreement be determined by the court on a reference under section 58 below.
…
(6) The authority of a government department in respect of an invention may be given under this section either before or after the patent is granted and either before or after the use in respect of which the authority is given is made, and may be given to any person whether or not he is authorised directly or indirectly by the proprietor of the patent to do anything in relation to the invention.
(7) Where any use of an invention is made by or with the authority of a government department under this section, then, unless it appears to the department that it would be contrary to the public interest to do so, the department shall notify the proprietor of the patent as soon as practicable after the second of the following events, that is to say, the use is begun and the patent is granted, and furnish him with such information as to the extent of the use as he may from time to time require.
…"
"Special provisions as to Crown use during emergency.
(1) During any period of emergency within the meaning of this section the powers exercisable in relation to an invention by a government department or a person authorised by a government department under section 55 above shall include power to use the invention for any purpose which appears to the department necessary or expedient—
(a) for the efficient prosecution of any war in which Her Majesty may be engaged;
(b) for the maintenance of supplies and services essential to the life of the community;
(c) for securing a sufficiency of supplies and services essential to the well-being of the community;
(d) for promoting the productivity of industry, commerce and agriculture;
(e) for fostering and directing exports and reducing imports, or imports of any classes, from all or any countries and for redressing the balance of trade;
(f) generally for ensuring that the whole resources of the community are available for use, and are used, in a manner best calculated to serve the interests of the community; or
(g) for assisting the relief of suffering and the restoration and distribution of essential supplies and services in any country or territory outside the United Kingdom which is in grave distress as the result of war;
and any reference in this Act to the services of the Crown shall, as respects any period of emergency, include a reference to those purposes.
(2) In this section the use of an invention includes, in addition to any act constituting such use by virtue of section 55 above, any act which would, apart from that section and this section, amount to an infringement of the patent concerned or, as the case may be, give rise to a right under section 69 below to bring proceedings in respect of the application concerned, and any reference in this Act to 'use for the services of the Crown' shall, as respects any period of emergency, be construed accordingly.
(3) In this section 'period of emergency' means any period beginning with such date as may be declared by Order in Council to be the commencement, and ending with such date as may be so declared to be the termination, of a period of emergency for the purposes of this section.
(4) A draft of an Order under this section shall not be submitted to Her Majesty unless it has been laid before, and approved by resolution of, each House of Parliament."
Article 31 of TRIPs
"Other Use Without Authorization of the Right Holder
Where the law of a Member allows for other use of the subject matter of a patent without the authorization of the right holder, including use by the government or third parties authorized by the government, the following provisions shall be respected:
(a) authorization of such use shall be considered on its individual merits;
(b) such use may only be permitted if, prior to such use, the proposed user has made efforts to obtain authorization from the right holder on reasonable commercial terms and conditions and that such efforts have not been successful within a reasonable period of time. This requirement may be waived by a Member in the case of a national emergency or other circumstances of extreme urgency or in cases of public non-commercial use. In situations of national emergency or other circumstances of extreme urgency, the right holder shall, nevertheless, be notified as soon as reasonably practicable. In the case of public non-commercial use, where the government or contractor, without making a patent search, knows or has demonstrable grounds to know that a valid patent is or will be used by or for the government, the right holder shall be informed promptly;
…
(h) the right holder shall be paid adequate remuneration in the circumstances of each case, taking into account the economic value of the authorization;
…"
The rival interpretations
i) this requires an express authorisation to work the patent in question;
ii) it requires either an express authorisation to work the patent or an authorisation to do a particular act in circumstances where that act necessarily infringes the patent; and
iii) it extends to an authorisation to do a particular act even if that does not necessarily involve infringing the patent.
Analysis
De minimis
"147. In the present case counsel for Napp accepted that the de minimis principle applied to claims for patent infringement. Moreover, he accepted that, to take an extreme example, if only one patch in a trillion (1012) fell within the claim, then the Defendants would not infringe the claim. He nevertheless submitted that the Defendants would infringe if larger, but still very small, proportions of their patches infringed. By way of illustration, he postulated a scenario in which it could be shown that, out of 2 million patches sold by a defendant between now and the expiry of the Patent, 200 fell within the claim (i.e. 1 in 10,000 or 0.01%). He argued that a defendant who sold just 200 patches which fell within the claim would undoubtedly infringe, and that it made no difference if the 200 patches constituted a single hour's production out of a year's worth of production, nor even if the 200 patches were randomly distributed amongst 1,999,800 non-infringing patches.
148. I can only say that I disagree. It seems to me that most people, and specifically the skilled person, would be very surprised by the proposition that selling products only 0.01% of which fall within the claim constitutes patent infringement, particularly where the 0.01% are randomly distributed among the remainder. I consider that this is precisely the kind of situation covered by the de minimis principle.
149. Furthermore, while I accept the force of Lord Phillips' warning [in Sienkiewicz v Greif (UK) Ltd [2011] UKSC 10, [2011] 2 AC 229 at [108]] about the dangers of trying to define a quantitative limit, it seems to me that, for reasons which will become clear, in the present case the court is forced, as a matter of practical reality, to draw a line somewhere. Where that line should be I will consider below."
"220. I will here summarise the extent of the acts said to be de minimis as follows.
a) MTPAS testing takes place (1) every few weeks, for a few minutes, on a few base stations; and (2) on a larger scale up to 3 times a year, for up to a few hours, on tens of base stations.
b) Annex E acts took place on less than 10 base stations.
c) Annex F acts took place over a 5 month period on 10 base stations.
221. There is no doubt that in each case the actual volume of the acts concerned was very small. However given that access control is not performed in normal operation, but (in general) only in extreme circumstances, the fact that the actual volume of the acts is very small is not surprising. On the contrary it is what one would expect. Moreover Vodafone's intention is not directly relevant, so to characterise them as 'inadvertent' is not an answer either.
222. Finally I do not accept that just because the acts were performed on a small scale they are commercially insignificant, given the context. For instance Vodafone does not charge the Crown for providing its response under MTPAS, nor for its MTPAS testing. However I consider that its participation in MTPAS, taken as a whole, is a small but significant part of Vodafone's commercial operations as a network provider. The same is less true of the other acts said to be de minimis, but I do not accept that they are such that Vodafone must be allowed to use somebody else's invention with impunity (which is the end point of its argument, stripped of the Latin tag). The extent of relief to be granted may be another matter."
Obviousness
"The 2-step version is based on Vodafone's assertion that Dr Irvine made an important admission in his evidence, to the effect that the claim covered a privileged user of the claim who was associated with both a normal class (0-9) and a special class (11-15). It was then said to be common ground between the experts that the skilled person would take the following steps:
i) adopt the IS-95 approach of putting classes 0-9 together in a single large group, offered access by a persistence test;
ii) adopt GSM access barring for the special classes so that the network can signal (i) which of them just proceed to access the RACH (GSM access barring '0') and (ii) which are barred (GSM access barring '1')."
"First, whilst Dr Irvine's views on technical matters were helpful his views on what the claim covers are irrelevant. Secondly I have already explained that the 2 classes themselves are mutually inconsistent. Thirdly, as IPCom pointed out Dr Irvine's views were expressed in the context of LTE, not in the context of the claim. Fourthly, it is another example of the type of argument based solely on common general knowledge which is unencumbered by detail and against which the Court has to be cautious. Fifthly it again involves hindsight. Sixthly this argument was never pleaded nor was it ever advanced in Mr Bishop's evidence. It first emerged in an opportunistic fashion in Vodafone's closing submissions and that approach is unfair to IPCom."
"This is a very simple and attractive argument, untrammelled as it is by any of the details of a practical working system. Mr Gould's fundamental position was that the skilled team would be much more likely to start from one of the known standard proposals, such as GSM/GPRS or IS-95. His cross-examination required him to clear his mental decks of all such proposals and start with a system solely based on the lottery. He plainly thought this whole exercise unrealistic, as I believe it to have been. The skilled person's first port of call would have been to see what methods of control had in fact been used in the past. This is particularly so in a case where such methods have been through standardisation processes. I have already considered whether the methods disclosed in GSM/GPRS or IS-95 would have led to the invention and concluded that they would not. The obviousness argument from common general knowledge requires instead an a priori re-assessment of the problem without reference to these methods. I must take this decision into account in assessing whether the approach adopted in the patent is inventive."
Form of declaration
"Operating access control in accordance with 3GPP TS 36.331, version 12, section 5.3.3.11 by an LTE Base Station (each an eNodeB) transmitting the LTE parameters 'ac-BarringConfig' and 'ac-BarringForSpecialAC' (the 'ACB Method'), necessarily infringes claims 1 and 7 of the Patent. Claims 1 and 7 of the Patent are accordingly essential to the implementation of the ACB Method."
"If and insofar as the option to perform access control in accordance with 3GPP TS 36.331, version 12, section 5.3.3.11 is being exercised by an LTE Base Station (each an eNodeB) transmitting the LTE parameters 'ac-BarringConfig' and 'ac-BarringForSpecialAC' (the 'ACB Option'), then claims 1 and 7 of the Patent are necessarily infringed by such LTE Base Station (eNodeB). Claims 1 and 7 of the Patent are accordingly essential to the optional implementation of the ACB Option by an LTE Base Station (eNodeB)."
Disposition
Asplin LJ:
Lewison LJ:
"There is a modern tendency in the law to break down divisions in the rules on the interpretation of different kinds of document, both private and public, and to look for more general rules on how to ascertain the meaning of words. In particular, there has been a harmonisation of the interpretation of contracts, unilateral notices, patents and also testamentary documents."
"… a problem of infringement is best approached by addressing two issues, each of which is to be considered through the eyes of the notional addressee of the patent in suit, ie the person skilled in the relevant art. Those issues are: (i) does the variant infringe any of the claims as a matter of normal interpretation; and, if not, (ii) does the variant nonetheless infringe because it varies from the invention in a way or ways which is or are immaterial? If the answer to either issue is "yes", there is an infringement; otherwise, there is not."
"… issue (i), as already mentioned, involves solving a problem of interpretation, which is familiar to all lawyers concerned with construing documents. While the answer in a particular case is by no means always easy to work out, the applicable principles are tolerably clear, and were recently affirmed by Lord Hodge JSC in Wood v Capita Insurance Services Ltd … paras 8–15."
