No Remedy for Disappointed Trust? The Liability Regime for Certification Authorities Towards Third Parties Outwith the EC Directive in England and Germany Compared (Continued)
Notes
1 . This paper was originally presented to the University of Sheffield, Department of Law, as a Dissertation for the attainment of a Masters' Degree in International, Commercial and European Law, in August 2001. It was supervised by Geraint Howells, Professor of Law at the University of Sheffield. The paper was updated in March 2002, in order to embrace the newer legislative development in the United Kingdom.
2 . In this connection, this term is not used in a technical sense.
3 . The pair of keys is usually provided by a CA as part of its services.
4 . The private key is usually stored on a smart card and can be accessed only through entering a personal identification number.
5 . The system derives its name from this idea.
6 . Also called 'hash value' or 'hash result'. The result of the operation of the hash function is a very short file in comparison to the word document but nevertheless substantially unique to it. In the case of a secure hash function it is 'computationally infeasible' to derive the original message from knowledge of its 'hash value'.
7 . Bob may get Alice's public key either from her (as part of a certificate, if certified), or from Alice's (or the CA's) web page, etc. In some cases, the choice might affect the legal regime that applies to the CA.
8 . If the 'message digest' had been encoded with the private key of a person other than Alice, the usage of Alice's public key on this electronic signature will result in the awareness that the message has been sent by someone else than Alice, since in theory only the person behind the synonym 'Alice' is in possession of the private key.
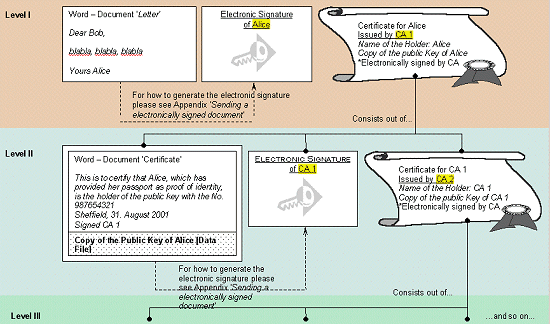
9 . Hierarchical CA structures are not the only solution. Confidence may also be achieved by cross-certification. This means that two CA's certify each other's public key. It is also possible that CAs certify themselves by simply signing their own public keys and posting the certificate on their own web sites. Self-certification is possible because the CAs rely on trust gained from other activities, such as postal services or banking activities ( Angel, 1999 ).
10 . So-called identifying certificates ; The CA connects (binds) a name to a public key. The act of the CA in checking that the name corresponds to something in the non-digital world binds the name to an identity ( Froomkin, 1996 ).
11 . So-called authorising certificates .
12 . Under English law, contracts signed with forged 'signatures' might (!) allow the party adversely affected by a fraudulent transaction to repudiate or revoke the transaction. [see for the legal situation in the 'offline world', Guest, et al (eds), 1989 . For example, somebody could use the identity of a certificate holder, different from himself, to enter into a contract with a relying third party; whereby using a forged 'signature'. The legal relation between the relying third party and the forger, however, is to be distinguished from the relation between the CA and the relying third party. The latter is the concern of this paper. Therefore, for our purposes, one has to ask the question: whether the ascribable behaviour of the CA, which may have facilitated the fraud, amounts to an infringement of the (own) contractual or tortuous duty toward the relying party.
13 . Entry into force of the EC Directive 1999/93.
14 . E.g; the German Digital Signature Law 1997, Italian legislation (DPR of 10. November 1997, no.513).
15 . N.B: Electronic Communications Act 2000. Part 1 (voluntary approval/ accreditation of 'trust service providers') has not been commenced since the industry is creating 'tScheme', a self-regulatory body, < http://www.tscheme.org >.
16 . Synonymous with the term 'certification authority'
17 . The requirements for a qualified certificate are set out in Annex I and II of the ESD: Qualified certificates must contain:
'(a) an indication that the certificate is issued as a qualified certificate;
(b) the identification of the certification-service-provider and the State in which it is established;
(c) the name of the signatory or a pseudonym, which shall be identified as such;
(d) provision for a specific attribute of the signatory to be included if relevant, depending on the purpose for which the certificate is intended;
(e) signature-verification data which correspond to signature-creation data under the control of the signatory;
(f) an indication of the beginning and end of the period of validity of the certificate;
(g) the identity code of the certificate;
(h) the advanced electronic signature of the certification-service-provider issuing it;
(i) limitations on the scope of use of the certificate, if applicable; and
(j) limits on the value of transactions for which the certificate can be used, if applicable.'
A certification-service-provider issuing qualified certificates must meet the following requirements: They must:
'(a) demonstrate the reliability necessary for providing certification services;
(b) ensure the operation of a prompt and secure directory and a secure and immediate revocation service;
(c) ensure that the date and time when a certificate is issued or revoked can be determined precisely;
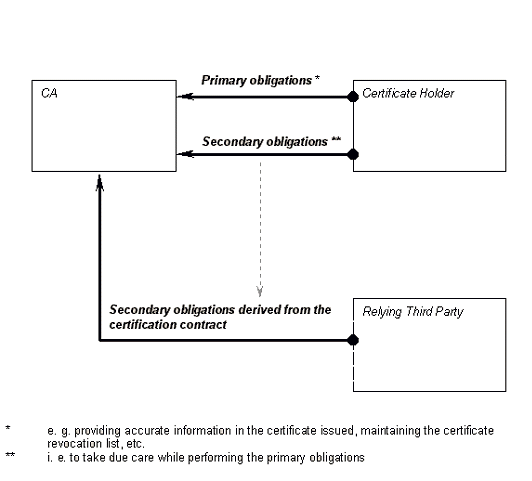
(d) verify, by appropriate means in accordance with national law, the identity and, if applicable, any specific attributes of the person to which a qualified certificate is issued;
(e) employ personnel who possess the expert knowledge, experience, and qualifications necessary for the services provided, in particular competence at managerial level, expertise in electronic signature technology and familiarity with proper security procedures; they must also apply administrative and management procedures which are adequate and correspond to recognised standards;
(f) use trustworthy systems and products which are protected against modification and ensure the technical and cryptographic security of the process supported by them;
(g) take measures against forgery of certificates, and, in cases where the certification-service-provider generates signature-creation data, guarantee confidentiality during the process of generating such data;
(h) maintain sufficient financial resources to operate in conformity with the requirements laid down in the Directive, in particular to bear the risk of liability for damages, for example, by obtaining appropriate insurance;
(i) record all relevant information concerning a qualified certificate for an appropriate period of time, in particular for the purpose of providing evidence of certification for the purposes of legal proceedings. Such recording may be done electronically;
(j) not store or copy signature-creation data of the person to whom the certification-service-provider provided key management services;
(k) before entering into a contractual relationship with a person seeking a certificate to support his electronic signature inform that person by a durable means of communication of the precise terms and conditions regarding the use of the certificate, including any limitations on its use, the existence of a voluntary accreditation scheme and procedures for complaints and dispute settlement. Such information, which may be transmitted electronically, must be in writing and in readily understandable language. Relevant parts of this information must also be made available on request to third-parties relying on the certificate;
(l) use trustworthy systems to store certificates in a verifiable form so that:
- only authorised persons can make entries and changes,
- information can be checked for authenticity,
- certificates are publicly available for retrieval in only those cases for which the certificate-holder's consent has been obtained, and
- any technical changes compromising these security requirements are apparent to the operator.'
18 . The requirements for secure signature-creation devices are set out in Annex III of the ESD:
'1. Secure signature-creation devices must, by appropriate technical and procedural means, ensure at the least that:
(a) the signature-creation-data used for signature generation can practically occur only once, and that their secrecy is reasonably assured;
(b) the signature-creation-data used for signature generation cannot, with reasonable assurance, be derived and the signature is protected against forgery using currently available technology;
(c) the signature-creation-data used for signature generation can be reliably protected by the legitimate signatory against the use of others.
2. Secure signature-creation devices must not alter the data to be signed or prevent such data from being presented to the signatory prior to the signature process.'
19 . Germany, in §§ 15 and 16 of the Gesetz über Rahmenbedingungen für elektronische Signaturen (Signaturgesetz - SigG) (Act for a Basic Framework for Electronic Signatures 2001 (Signature Act) (translation by the author), has chosen to provide such an option.
20 . '(2) Damages need not be reimbursed if the certification-service provider has incurred no culpability.
(3) If a qualified certificate restricts the use of the signature code to certain applications by type or extent, damages shall be payable only within the limits of these restrictions.
(4) The certification-service provider shall be liable for third parties commissioned under [§] 4(5) and when guaranteeing foreign certificates under [§] 23(1) No. 2 as for his own actions. [§] 831(1) Sentence 2 of the German Civil Code shall not apply'.
21 . §12 SigG (minimum coverage 500,000 DM).
22 . Contracts 'made by courts' are well known to English Law (Atiyah, 1995). The situation is for example informed by Collen v. Wright (1857) 8 E. & B. 647, New Zealand Shipping Co. Ltd. v. A. M. Satterthwaite & Co. Ltd. [1975] A C 154 (also known as The Eurymedon )].
23 . [1893] 1 Q B 256.
24 . Currie v. Misa (1875) L. R. 10 Ex. 153, 162; please see in general Treitel, 1999 , 63-93.
25 . As for example in Mansukhani v. Sharkey [1992] 2 E. G. L. R. 105.
26 . Along the lines outlined by Bowen, LJ in Carlill v. Carbolic Smoke Ball Co. [1893] 1 Q B 256.
27 . So-called 'objective test' (Treitel, 1999); case law: First Energy (UK) Ltd. v. Hungarian International Bank Ltd. [1993] 2 Lloyd's Rep. 195, 201; Ignazio Messina & Co. v. Polskie Linie Oceaniczne [1995] 2 Lloyd's Rep. 566, 571; Bowerman v. Association of British Travel Agents Ltd. [1995] N. L. J. 1815.
28. The Hannah Blumenthal [1983] 1 A. C. 854; as interpreted in The Leonidas D [1985] 1 W. L. R. 925; Beatson 102 L. Q. R. 19; The Agrable [1987] 2 Lloyd's Rep. 223, 235; Cie. Française d'Importation, etc., S. A. v. Deutsche Continental Handelsgesellschaft [1985] 2 Lloyd's Rep. 592, 597; Amherst v. James Walker Goldsmith and Silversmith Ltd, [1983] Ch. 305.
29 . The Golden Bear [1987] 1 Lloyd's Rep. 330, 341; approved in The Antclizo [1987] 2 Lloyd's Rep. 130, 143; The Multibank Holsatia [1988] 2 Lloyd's Rep. 486, 492; The Maritime Winner [1989] 2 Lloyd's Rep. 506, 515; as dictum in The Amazonia [1990] 1 Lloyd's 238, 242.
30 . For a more comprehensive discussion please see Treitel, 1999 , 9.
31 . Treitel, 1999 , 780; case law: e. g. Clark v. Kirby-Smith [1964] Ch. 506 (solicitor); Bagot v. Stevens, Scanlan & Co. Ltd. [1966] 1 Q. B.197 (architect); O'Connor v. Kirby [1972] 1 Q. B. 90 (insurance broker).
32 . Trumpet Software Pty Ltd. v. OzEmail Pty Ltd. [1996] 34 I. P. R. 481; Reed, 2000a, 139.
33 . For example, the British Telecom (BT) TrustWise Relying Third Party Charter states the following: 'To the extent permitted by the law of England and Wales, BT makes no representations and holds out no warranties in respect of Certificates or the Repository other than those expressly set out in the CPS and this Charter' ( BT, 2000b ).
34 . The BT TrustWise Relying Third Party Charter refers to the BT Certification Practice Statement (CPS) ( BT, 1999 ) where it explains the technical and legal standard procedures which are applied before a certificate is issued. To verify a BT certificate or to establish the representations and warranties BT makes or does not make, the recipient of a electronic message accompanied by a BT certificate is required only to read comprehensively about 70 pages, heavily loaded with technical and legal phrases.
35 . Robinson v. Harman (1848) 1 Ex. 850; Oughton and Lowry, 2000 , 126.
36 . Hadley v. Baxendale (1854) 9 Ex 341
37 . Koufos v. Czarnikow Ltd . [1969] 1 A C 350
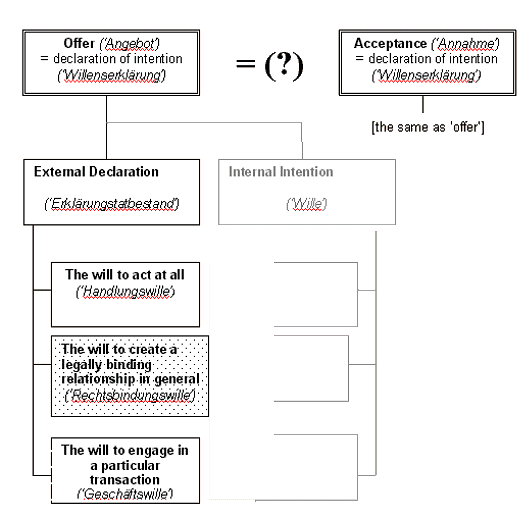
38 . The position is also informed by cases such as Thornton v. Shoe Lane Parking [1971] 2 Q.B.163; Interfoto Picture Library Ltd. v. Stiletto Visual Programmes Ltd. [1988] 1 All. E.R.348 (notice must be adequate relative to clause's scope and circumstances); Olley v. Marlborough Court [1949] 1 All. E.R.127 (notice of the exclusion must be given before the contract is made - not after).
39 . Photo Production Ltd. v. Securicor Transport Ltd. [1980] A C 827, 843 per Lord Wilberforc; Smith v. Eric S. Bush [1990] 1 AC 831, 858-9 per Lord Griffiths; Qughton and Lowry, 1999 , 397.
40 . N.B. S.4 (1); schedule 3, S.1 (b) of the UTCCR 1994.
41 . ESD, Art: 6 (3) see above; The DTI Consultation on EC Directive 1999/93/EC contains no response to this question.
42 . This point is supported by the DTI, Consultation on EC Directive 1999/93/EC, § 40.
43 . The form contract stipulates the following in point 3.8: 'By providing a Certificate for the Customer; BT promises to the Customer and only to the Customer: ...'; in point 6.2: 'The Customer expressly acknowledges that BT accepts no liability of any kind in relation to or arising from any representation or warranty or other statement made by the Customer to any third party or by the third party to a Customer, including without limitation any such communication which incorporates a Certificate.'; in point 12.4: 'BT excludes all liability of any kind in respect of any transaction into which the Customer may enter with any third party' ( BT, 2000a ).
44 . S.3 (2) of the Contracts (Rights of Third Parties) Act 1999.
45 . Liability in Tort also exists concurrently with contract. [ Henderson v. Merrett Syndicates Limited [1995] A. C. 145; White v. Jones [1995] 2 A C 207.
46 . Exceptions may exist, Nicoll, 2000 , 26-7.
47 . Ultramares Corporation v. Touche Niven & Co. (1931) 255 NY 170 (Cardozo J).
48 . Harpwood, 2000 , 31. The so-called three-stages-test has been re-confirmed in Caparo Industries plc v. Dickman [1990] 2 A C 605.
49 . [1964] A.C.465; notion expanded in Howard Marine v. Odgen [1978] Q B 574 to include any business or professional context.
50 . Hedley Byrne & Co. Ltd. V. Heller & Partners Ltd. [1964] A.C.465, 530 (Lord Devlin).
51 . E.g; Caparo Industries plc v. Dickman [1990] 2 A.C.605.
52 . [1990] 2 A.C.605, 638.
53 . The limitation (through purpose-test) of the range of persons to whom duty is owed was reaffirmed in Al Nakib Investments (Jersey) Ltd. v. Longcroft [1990] 1 W. L.R.1390.
54 . The check of the certificate is an integral part of the electronic signature technology.
55 . Even if the decision to transact is not solely based on the identity or another attribute of the certificate holder, the true identity, etc. is one criteria in the decision-making process before entering into a contract. It is sufficient that it is '... very likely [emphasis added] that the plaintiff would rely on that information ... in deciding whether or not to engage in the transaction in contemplation' Caparo Industries plc v. Dickman [1990] 2 A.C.605, 620 (Lord Bridge).
56. Hedley Byrne & Co. Ltd. v. Heller & Partners Ltd.[1964] A C 465 (Lord Reid 482, Lord Morris 493)
57 . In theory even a certificate with a minimal 'permitted' transaction value of (lets say) £10, if enough people rely only on this and suffer loss, can cause a damage of millions of £ in no time.
58 . [1991] All.E.R.134.
59 . [1990] 2 A.C.605, 620.
60 . Osman v. UK (1998) 5 B. H.R.C.293; Jones, 2000 , 72.
61 . Froomkin, 1996 , III. A.2.b. Froomkin provides some good examples of how the standard of care can be ascertained: 'For Example, if [the CA] says in [its] certification practise statement, incorporated by reference in the certificate, that [it] requires applicants to show their passports, but in fact failed to ask [the holder] to show [his], [the CA] is guilty of negligence. Or, if [the CA] says that [it] checks passports, and did so, but failed to notice that [the holder] presented a crude forgery that could have been detected with ordinary care [footnote omitted], [it] is guilty of negligence. Conversely, if [the CA] did everything [it] said [it] would do, but [the holder] proffered a superbly faked passport, then [the CA] is not guilty of negligence.
62 . 'Wagon Mount' Overseas Tankship (UK) Ltd. v Morts Dock & Engineering Co. [1961] A.C.388.
63 . [1933] A.C.449.
64 . Ibid, N.B. ABA, 1996 , Comment 2.2.3.
65 . S.2 (2) in connection with s. 1 (1) (b), S.13 of the Unfair Contract Terms Act 1977.
66 . Brown v. Rolls-Royce Ltd. [1960] 1 W. L.R.210.
67 . Pan Atlantic Insurance Co. Ltd. v. Pine Top Insurance Co. Ltd. [1995] 1 A.C.501, 542.
68 . ...an offer by the relying party to 'rely' on the certificate, and the response by the CA that the certificate in question is still valid.
69 . ...the unilateral offer of the CA to the whole world along the lines of Carlill v. Carbolic Smoke Ball Co.
70 . Under German law any limitation of the contractual duties as well as the liability, also have an effect against the third party beneficiary, as the rights of the latter are derived from the contract between the CA and the certificate holder. However, in contrast to English law, it is not allowed to exclude or limit the protective effect of the contract only in relation to the third party. This would infringe the principle of good faith ( Larenz, 1986 ), § 17 II, deferring opinion BGH, Official Series (Civil Matters), vol. 56 , 269, 274].
71 . Instead of construing a contract, scholars resort to a non-contractual obligation ('gesetzliches Schuldverhältnis'), based on trust or confidence, generated by a special professional position, expert knowledge or even a 'social role', claimed by certain professional or business groups, i. e. banks, solicitors, notaries public, insurance companies, etc. ( Larenz, 1986 ).
72 . N.B: Annex V 'Contract in German Civil Law'.
73 . 'Auslegung' is conducted in the light of §§ 133, 157 BGB , which provide general rules of interpretation of a declaration of will and contracts. The remaining rules are contained in case law and doctrine. For the translated text of § 133 BGB , please see Youngs, 1994 , 266-7.
74 . So-called 'Auslegung vom objetiven Empfängerhorizont'.
75 . BGH NJW 1991 , 32; 1992 , 2080.
76 . BGH NJW 1989 , 2882
77 . BGH, Official Series (Civil Matters), vol. 100 , 117.
78 . If no consideration, in the form of remuneration, is provided, the 'Auskunftserteilungsvertrag' is governed by the rules on the contract of instruction, §§ 662ff ('Auftrag') ( Bassenge et al, 1999 , § 676, margin number 3).
79 . The check of the certificate is an integral part of the electronic signature technology.
80 . BGH, Official Series (Civil Matters), vol. 133 , 36 [42].
81 . BGH, VersR 1986 , 35.
82 . The same conclusion is reached by Leier, 2000 . In contrast Haas, 1998 .
83 . Larenz, 1987 ,§ 17 II; E.g; liability in contract includes strict liability of a principal (' Geschäftsherr') for misconduct ('Fehlverhalten') of person employed by the principal (debtor) in the performance of his obligation (' Gehilfen' ), § 278 BGB . In contrast, § 831 BGB imposes liability upon a master ('Geschäftsherr') only if he acted negligently while choosing and supervising his servants ('Verrichtungsgehilfen').
84 . BGH, Official Series ( Civil matters ), vol. 49, 354; vol. 70, 329; vol. 129, 168.
85 . Same conclusion reached by Leier, 2000 , 15 and Haas, 1998 , 273.
86 . Reichsgericht, Official Series (Civil Matters), vol. 127, 222; BGH, Official Series (Civil Matters), vol. 56, 273, BGH NJW 1984, 356.
87 . ...by the means of an interpretation which amends the contract ('ergänzende Vertragsauslegung'). Scholars instead derive the legal justification from judicial development of the law ('richterliche Rechtsfortbildung') of the optional law ('dispositives Recht') based on § 242 BGB (good faith). In practice both approaches achieve almost the same results ( Heinrichts , § 328, margin number 14).
88 . BGH, Official Series (Civil Matters), vol. 127, 378; vol. 128, 168/173; BGH NJW 1976, 1844; 1983, 1053; 1984, 356; 1985, 489.
89 . Same conclusion reached by Leier, 2000 and Haas, 1998 , 273.
90 . BGH NJW 1984, 355; 1987, 1758, 1760.
91 . BGH, Official Series (Civil Matters), vol. 51 , 91, 96; BGH NJW 1968 , 1929.
92 . Leier, Haftung , 15 also Haas, Haftung , 276.
93 . BGH NJW 1995, 392.
94 . This point of view is, for example, supported by Timm, 1997 .
95 . However, should the court be prepared to accept the protective effect of the certification contract, then the plaintiff will be able to recover the loss he suffered due to the non-performance of the owed secondary contractual duty. This recovery is legally based on the principle of 'positive violation of contractual duty' ('positive Vertragsverletzung', §§ 280, 286, 352, 326 BGB ) in connection with the rules developed for the contract with protective effect for the benefit of a third party. A contractual limitation of liability is possible. However, a limitation of the liability towards the third party only, contained in the certification contract, would infringe the principles of good faith embodied in § 242 BGB ( Larenz, 1987 ).
96 . In the case of fraud, wilfulness is required.
97. The reckless provision of information, however, can only establish the objective element of § 826 BGB - the conduct contra bonus mores. The 'Schädigungsvorsatz' must still be established ( Larenz and Canaris, 1994 , § 78 II 2.d).
98 . i.e; that the person seeking or using his incorrect information could suffer harm.
99 . Literally translated 'will to harm'.
100 . Gross negligence does not itself qualify as wilfulness for the purposes of § 826 BGB, although in practice the distinction between cross negligence and wilfulness in the form of 'dolus eventualis' is fluent and the trail judge has considerable discretion ( Larenz, and Canaris, 1994 , § 78 III 1.c, Van Gerven et al, 1999 , 277).
101 . BGH WM 1956 1229.
102 . ...which he accepts as inevitable even though he might not specifically desire them.
103 . Translation from Youngs, 1994 , 489.
104 . The damage must have been caused by a person to whom the master had 'entrusted the performance of a function' ('zu einer Verrichtung bestellt'), § 831 (1) 1 st sentence BGB . Furthermore, the damage must have been inflicted by the servants 'in the exercise of the function assigned to him', by an 'unlawful' ('widerrechtlich') act.
105 . Reichsgericht, Official Series (Civil Matters), vol. 78 , 108; BGH, Official Series (Civil Matters), vol. 4 , 2.
106 . BGH JZ 1985 , 951.
107 . BGH NJW 1973 , 322; von Bar, 1994, 123.
Bibliography *
American Bar Association (ABA) (1996), Digital Signature Guidelines - Legal Infrastructures for Certification Authorities and Secure Electronic Commerce , American Bar Association, Chicago.
Angel, J (1999), Why use Digital Signatures for Electronic Commerce?, Journal of Information Law and Technology, 1999, (2)
< http://www2.warwick.ac.uk/fac/soc/law/elj/jilt/1999_2/angel/>.
Atiyah, P S (1995), An Introduction to the Law of Contract , 5 th ed; Clarendon Press, Oxford.
Bassenge, P, Diederichsen, U, Edenhofer, W, Heinrichs, H, Heldrich, A, Putzo, H, Sprau, H, Thomas, H (1999), Palandt - Kurzkommentar zum Bürgerlichen Gesetzbuch , 58 th ed., Verlag C H Beck, München, Munich.
Beale, H G, Bishop, W D and Furmston, M P (1995), Contract - Cases and Materials , 3 rd ed; Butterworths, London, Dublin and Edinburgh.
Brazier, M and Murphy, J (1999), Streets on Tort , 10 th ed; Butterworths, London, Edinburgh and Dublin.
BT (1999), BT Certification Practice Statement , BT, < http://www.trustwise.com/repository/PDF/cps.pdf >.
BT (2000a), Conditions for BT TrustWise Class 1 Personal Digital Certificates , BT, < http://www.trustwise.com/repository/pdf/class1_personal_contract.pdf >.
BT (2000b), BT TrustWise Relying Third Party Charter , BT, < http://www.trustwise.com/rpa/index.html >.
Cane, Peter (1996), Tort Law and Economic Interests , 2 nd ed; Clarendon Press, Oxford.
Furmston, M P (1996), Cheshire, Fifoot and Furmston's Law of Contract , Butterworths, London.
Department of Trade and Industry (DTI) (1999a), Building Confidence in Electronic Commerce - A Consultation Document , DTI,< http://www.dti.gov.uk/cii/ecommerce/ukecommercestrategy/archiveconsultationsdocs/index.shtml >.
Department of Trade and Industry (DTI) (1999b), Promoting Electronic Commerce - Consultation on Draft Legislation and the Government's Response to the Trade and Industry Committee's Report , DTI, London.
Department of Trade and Industry (DTI) (2001a), Consultation on EC Directive 1999/93/EC of the European Parliament and Council on a Community Framework for Electronic Signatures , DTI, London.
DTI (2001b), Consultation on EC Directive 1999/93/EC of the European Parliament and Council on a Community Framework for Electronic Signatures - Summary of Responses , < http://www.dti.gov.uk/cii/datasecurity/electronicsignature/signatures2.shtml >.
Dawe, T (2001), The E-key to Safe Business on the Net , The Times, 12. June 2001, < http://www.thetimes.co.uk/article/0,,349-2001194780,00.html >.
Der Spiegel Online, (2000a), Bald ohne Kreditkarte Online Shoppen , Der Spiegel Online, 22/2000, < http://www.spiegel.de/netzwelt/technologie/0,1518,78630,00.html >.
Der Spiegel Online (2000b), Verwaltung Signiert Digital , Der Spiegel Online, 04/2000, < http://www.spiegel.de/netzwelt/politik/0,1518,61041,00.html >.
Edwards, L and Waelde, C (2000), Law and the Internet , Hart Publishing, Oxford and Portland (Oregon).
Fisher, H D (1999), The German Legal System & Legal Language , 2 nd ed; Cavendish Publishing, London and Sydney.
Froomkin, M A (1996), The Essential Role of Trusted Third Parties in Electronic Commerce , Oregon Law Review, 1996 (75) 49.
Gründel, N (2000), Fineid zum Ersten, Fasme zum Zweiten , Der Spiegel Online, 23/2000, < http://www.spiegel.de/netzwelt/politik/0,1518,79665,00.html >.
Guest, A G. et al . (eds.) (1989), Chitty on Contracts - General Principles , 26 th ed; Sweet & Maxwell, London.
Haas, L (1998), Zur Haftung der Zertifizierungsstellen nach dem SigG gegenüber Dritten published in Heldrich, A.; Schlechtinger, and Schmidt, (eds.) (1998), Recht im Spannungsfeld von Theorie und Praxis - Festschrift für Helmut Heinrichts zum 70. Geburtstag , Verlag C. H. Beck, München (Munich), 261.
Harpwood, V (1996), Law of Torts , 2 nd ed; Cavendish Publishing, London and Sydney.
Harpwood, V (2000), Principles of Tort Law , 4 th ed; Cavendish Publishing, London and Sydney.
Harrison, R (2000), Public Key Infrastructure: Risks of Being Trusted , 2000 11 C & L 28.
Heinrichts (n.d), Palandt , § 328, margin number 14.
House of Commons - Select Committee on Trade and Industry (1999), Seventh Report , Trade and Industry Committee Publications, London.
Howells, G G and Weatherill, S (1995), Consumer Protection Law , Dartmouth Publishing, Aldershot, Brookfield (USA), Singapore, Sydney.
Jagmann, R (1995), J. von Staudinger - Kommentar zum Bürgerlichen Gesetzbuch mit Einführungsgesetz und Nebengesetzen , vol. containing §§ 328 - 361, 13 th ed., Sellier - de Gruyter, Berlin.
Jones, M A (2000), Textbook on Tort , 7 th ed; Blackstone Press Limited, London.
Larenz, K (1986), Lehrbuch des Schuldrecht s , 2 nd vol., 1 st half-binding, 13 th ed., Verlag C. H. Beck, München (Munich).
Larenz, K (1987), Lehrbuch des Schuldrecht s , 1 st vol., 14 th ed., Verlag C. H. Beck, München (Munich).
Larenz, K and Canaris, CW (1994), Lehrbuch des Schuldrecht s , 2 nd vol., 2 nd half-binding, 13 th ed; Verlag C H Beck, München (Munich).
Larenz, K and Wolf, M (1997), Allgemeiner Teil des Bürgerlichen Rechts , 8 th ed., Verlag C. H Beck, München (Munich).
Leier, Barbara, (2000), Haftung der Zertifizierungstellen nach dem SigG - Betrachtung der geltenden und Überlegung zur zukünftigen Rechtslage , Multimedia und Recht (MMR), 2000 (13).
Lockett, N and Egan, M (1995), Unfair Terms in Consumer Agreements - The New Rules Explained , John Wiley & Sons, Chichester, New York, Brisbane, Toronto, Singapore.
Lorenz, W (1994), Contracts and Third-Party Rights in German and English Law, in Markesinis, Basil S. (ed.) (1994), The Gradual Convergence - Foreign Ideas, Foreign Influences and English Law on the Eve of the 21st Century , Clarendon Press, Oxford.
Markesinis, B S (1994), The German Law of Torts - A Comparative Introduction , 3 rd ed., Clarendon Press, Oxford.
Mason, Stephen, (1999/2000), Electronic Signatures: The Technical and Legal Ramifications , 1999/2000 10 C & L 37.
Medicus, D (1999), Bürgerliches Recht , 18 th ed. Carl Heymanns Verlag, Köln (Cologne), Berlin; Bonn and München (Munich).
Miller, C J (1998), Harvey, B W and Parry, D L (1998), Consumer and Trading Law - Text, Cases and Materials , Oxford University Press, Oxford.
Nicoll, C (2000), Internet Regulations: Potential Liabilities , Commercial Liability L. Rev. 2000 (1) 15.
Oughton, D and Lowry, J (2000), Textbook on Consumer Law , 2 nd ed; Blackstone Publishing, London.
Rebel, T F and Koenig, W (1999), Ensuring Security and Trust in Electronic Commerce in Sudweeks, Fay and Romm, Celia T. (1999), Doing Business on the Internet - Opportunities and Pitfalls , Springer Verlag, London, Berlin, Heidelberg, 101.
Reed, C (2000a), Internet Law : Text and Materials , Butterworths, London, Edinburgh, Dublin.
Reed, Christopher (2000b), What is a Signature?, Journal of Information, Law & Technology (JILT) 2000 (3) < http://elj.warwick.ac.uk/jilt/00-3/reed.html >.
Rogers, W V H (1994), Winfield and Jolowicz on Tort , 14 th ed; Sweet & Meaxwell, London.
Roßnagel, A (1998), Das Gesetz und die Verordnung zur digitalen Signatur - Entstehung und Regelungsgehalt , Recht der Datenverarbeitung (RDV), 1998 (5).
Sinisi, V (2001), Digital Signature Legislation in Europe , 2001, 16 BJIBFL 17.
Smedinghoff, T J (1998), Certification Authority Liability Analysis , American Bankers Association, Washington D C.
The Economist (2000), SURVEY: GOVERNMENT AND THE INTERNET - Handle with Care , 22. June 2000.
Thomas, (?) Palandt , [Details to be advised].
Timm, B (1997), Signaturgesetz und Haftungsrecht , Datenschutz und Datensicherheit (DuD) 1997 (21), 52.
Treitel, G H (1999), The Law of Contract , 10 th ed; Sweet & Maxwell, London.
Uwer, H (2000), Kostendruck fördert eGovernment , Frankfurter Allgemeine Zeitung, FAZ.net, 28 November 2000,< http://www.faz.net/IN/INtemplates/faznet/default.asp?tpl=uptoday/content.asp&doc={ABFED30B-E81 7-437F-ADCC-99E88CB70C0E}&rub={9E7BDE6C-469E-11D4-AE7B-0008C7F31E1E}>.
Van Gerven, W (ed.), Lever, J, Larouche, P, von Bar, C, Viney, G (1999), Cases, Materials, and Text on National, Supranational and International Tort Law - Scope of Protection , Hart Publishing, Oxford.
v on Bar, C (1994), Liability for Information and Opinions causing pure economic Loss to Third Parties: A Comparison of English and German Case Law , in Markesinis, B S (ed.) (1994), The Gradual Convergence - Foreign Ideas, Foreign Influences and English Law on the Eve of the 21st Century , Clarendon Press, Oxford.
von Bar, C (1998), Verträge mit Schutzwirkung zugunsten Dritter , Drittschadensliquidation and extension of duty of care , 5, in The Institute of Comparative Law (Chuo University) (ed.) (1998), Toward Comparative Law in the 21 st Century - The 50 th anniversary of The Institute of Comparative Law in Japan Chuo University , Chuo University Press, Tokyo.
Youngs, R (1994), Sourcebook on German Law , Cavendish Publishing, London and Sydney.
Zweigert, Konrad and Kötz, Hein (1998), An Introduction to Comparative Law , 3 rd ed., Clarendon Press, Oxford
Table of Cases
England and Wales
Al Nakib Investments (Jersey) Ltd. v. Longcroft [1990] 1 W. L. R. 1390.
Amherst v. James Walker Goldsmith and Silversmith Ltd.[1983] Ch. 305.
Bagot v. Stevens, Scanlan & Co. Ltd.[1966] 1 Q. B.197.
Bowerman v. Association of British Travel Agents Ltd.[1995] N. L. J. 1815.
Brown v. Rolls-Royce Ltd.[1960] 1 W. L. R. 210.
Caparo Industries plc v. Dickman [1990] 2 A C 605.
Carlill v. Carbolic Smoke Ball Co.[1893] 1 Q B 256.
Cie. Française d'Importation, etc., S. A. v. Deutsche Continental Handelsgesellschaft [1985] 2 Lloyd's Rep. 592.
Clark v. Kirby-Smith [1964] Ch. 506.
Collen v. Wright (1857) 8 E. & B. 647.
Currie v. Misa (1875) L. R. 10 Ex. 153.
First Energy (UK) Ltd v. Hungarian International Bank Ltd [1993] 2 Lloyd's Rep. 195.
Hadley v. Baxendale (1854) 9 Ex 341.
Hedley Byrne & Co. Ltd. v. Heller & Partners Ltd.[1964] A C 465.
Henderson v. Merrett Syndicates Limited [1995] A. C. 145.
Howard Marine v. Odgen [1978] Q B 574.
Ignazio Messina & Co. v. Polskie Linie Oceaniczne [1995] 2 Lloyd's Rep. 566.
Mansukhani v. Sharkey [1992] 2 E. G. L. R. 105.
Interfoto Picture Library Ltd. v. Stiletto Visual Programmes Ltd.[1988] 1 All E R 348.
James McNaughton Papers Group Ltd. v. Hicks Anderson & Co.[1991] All. E. R. 134.
Koufos v. Czarnikow Ltd . [1969] 1 A C 350.
Liesbosch Dredger v. SS Edison [1933] A C 449.
New Zealand Shipping Co. Ltd. v. A. M. Satterthwaite & Co. Ltd.[1975] A C 154
(also known as The Eurymedon ).
O'Connor v. Kirby [1972] 1 Q. B. 90.
Olley v. Marlborough Court [1949] 1 All. E. R. 127.
Osman v. UK (1998) 5 B. H. R. C. 293.
Pan Atlantic Insurance Co. Ltd. v. Pine Top Insurance Co. Ltd.[1995] 1 A. C. 501, 542.
Photo Production Ltd. v. Securicor Transport Ltd.[1980] A C 827.
Robinson v. Harman (1848) 1 Ex. 850.
Smith v Eric S. Bush [1990] 1 A C 831.
The Agrable [1987] 2 Lloyd's Rep. 223.
The Amazonia [1990] 1 Lloyd's Rep. 238.
The Antclizo [1987] 2 Lloyd's Rep. 130.
The Golden Bear [1987] 1 Lloyd's Rep. 330.
The Hannah Blumenthal [1983] 1 A. C. 854.
The Leonidas D [1985] 1 W. L. R. 925.
The Maritime Winner [1989] 2 Lloyd's Rep. 506.
The Multibank Holsatia [1988] 2 Lloyd's Rep. 486.
Trumpet Software Pty Ltd. v. OzEmail Pty Ltd.[1996] 34 I. P. R. 481.
Thornton v. Shoe Lane Parking [1971] 2 Q B 163.
White v. Jones [1995] 2 A C 207.
'Wagon Mount' Overseas Tankship (UK) Ltd. v Morts Dock & Engineering Co.[1961] A C 388.
USA
Ultramares Corporation v. Touche Niven & Co.(1931) 255 NY 170 (Cardozo J.).
Germany
Reichsgericht, Official Series (Civil Matters), vol. 78 , 108.
Reichsgericht, Official Series (Civil Matters), vol. 127 , 222.
BGH, Official Series (Civil Matters), vol. 4 , 2.
BGH, Official Series (Civil matters), vol. 49 , 354.
BGH, Official Series (Civil Matters), vol. 51 , 96.
BGH, Official Series (Civil Matters), vol. 56 , 274.
BGH, Official Series (Civil Matters), vol. 56 , 273.
BGH, Official Series (Civil Matters), vol. 70 , 329.
BGH, Official Series (Civil Matters), vol. 100 , 117.
BGH, Official Series (Civil Matters), vol. 127 , 378.
BGH, Official Series (Civil Matters), vol. 128 , 168.
BGH, Official Series (Civil Matters), vol. 129 , 168.
BGH, Official Series (Civil Matters), vol. 133 , 42.
BGH Wertpapiermitteilungen -Zeitschrift für Wirtschafts- und Bankrecht (WM) 1956 1229.
BGH Neue Juristische Wochenschrift (NJW) 1968 , 1929.
BGH NJW 1973 , 322.
BGH NJW 1976 , 1844.
BGH NJW 1983 , 1053.
BGH NJW 1984, 355.
BGH NJW 1984, 355.
BGH NJW 1985 , 489.
BGH Juristen-Zeitung (JZ) 1985 , 951.
BGH Versicherungsrecht (VersR) 1986 , 35.
BGH NJW 1987 , 1760.
BGH NJW 1989 , 2882.
BGH NJW 1991 , 32.
BGH NJW 1992 , 2080.
BGH NJW 1995, 392.
Table of Legislation
European Community
Directive 1993/13/EC on unfair terms in consumer contracts.
Directive 1999/93/EC on a Community framework for electronic signatures (ESD).
England and Wales
Contracts (Rights of Third Parties) Act 1999.
Electronic Communications Act 2000.
Unfair Terms in Consumer Contracts Regulations 1994 (UTCCR).
Uniform Contract Terms Act 1977 (UCTA).
Germany
Act for a Basic Framework for Electronic Signatures 2001 (Gesetz über Rahmenbedingungen für elektronische Signaturen (Signaturgsetz (SigG))) and respective Ordinance.
Civil Code (Bürgerliches Gesetzbuch (BGB)).
Criminal Code (Strafgesetzbuch (StGB)).
Digital Signature Act 1997 (Signaturgesetz).
Italy
Italian legislation (DPR of 10. November 1997, no. 513).
* all electronic sources were accessed: 10 th August 2001.
Appendix
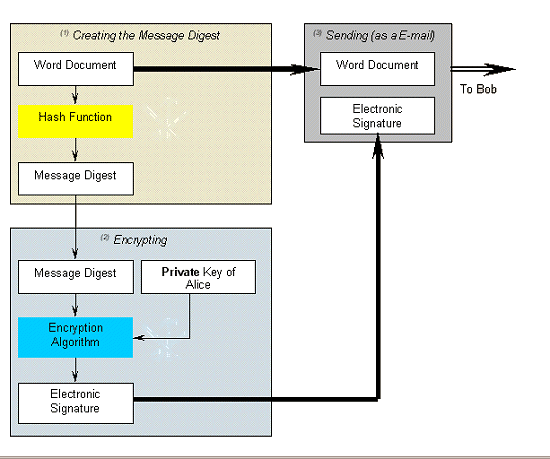
Figure 1: Sending an Electronically Signed Document
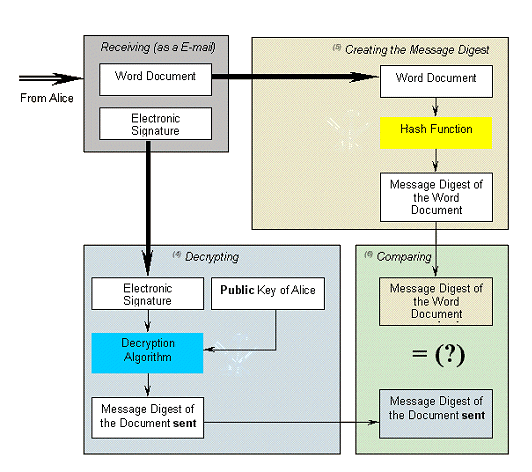
Figure 2: Validating an Electronically Signed Document
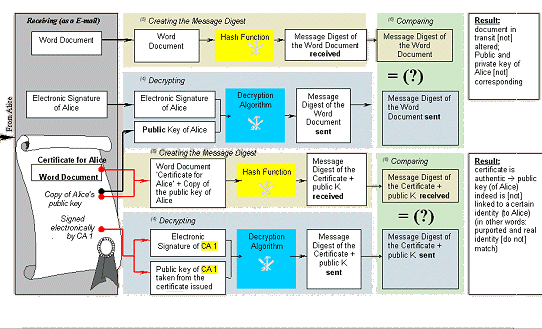
Figure 3: Validating an Electronically Signed Document with Certificate
Figure 4: Certification Structure
Figure 5: Contract in German Civil Law
Figure 6: Contract with a Protective Effect Towards a Third Party ('Vertrag mit Schutzwirkung zugunsten Dritter')
Glossary of CA Specific Terms
a dvanced electronic signatures (EC Directive term)
- will have the same value as a hand written signature and be admissible as evidence in legal proceedings
- is based on a qualified certificate and is created by a secure signature creation device
c ertification authority (CA)
- also certification-service-provider (term used in the EC Directive 1999/93)
- is a body, either public or private, that seeks to fill the need for trusted third party services in electronic commerce by issuing digital certificates that attest to some fact about the subject of the certificate
Certification Practice Statement (CPS)
- defines the representations CAs make and warranties they hold out in respect of certificates
certification-service-provider (EC Directive term)
- see certification authority
certificate
- means an electronic attestation which links a public key to a person and confirms the identity or other attributes
- see also qualified certificate
certificate revocation list
- since personal circumstances change and the reality represented by the certificate is out of date, certificates have limited periods of validity or are subject to periodic re-confirmation by the CA. Certificates which are outdated or have been compromised, e. g. by disclosing the private key, are listed in this list which is maintained by the issuing CA
- when, for example, the relying party is suspicious about the validity of the certificate, he interrogates the CA's Certificate Revocation List
' d igest' function
- see 'hash' function
e lectronic signature (in a technical sense)
- also called 'ciphertext'
- is the result of the encryption of the message digest with the private key (Encryption is carried out by performing a series of mathematical functions (an encryption algorithm) which has two inputs: the 'message digest' which is nothing more than a string of 1s and 0s and the private key which is itself a number) producing a series of different numbers
' h ash' function
- also 'digest' function
- is an algorithm which creates a digital representation or 'fingerprint' in form of a 'hash value' or 'hash result' or message digest of a standard length which is usually much smaller than the message but nevertheless substantially unique to it. Any change to the message invariably produces a different hash result when the same hash function is used. In the case of a secure hash function it is 'computationally infeasible' to derive the original message from knowledge of its 'hash value'.
hash result
- see message digest
- also hash value
hash value
- see message digest
- also hash result
m essage digest
- also 'hash value' or 'hash result'
- a digital representation or 'fingerprint' of a standard length which is usually much smaller than the message but nevertheless substantially unique to it. Any change to the message invariably produces a different hash result when the same hash function is used.
' n on-qualified' certificate
- see certificate
' p ublic key cryptography'
- uses two different but mathematically related keys, each of which will decrypt documents encrypted by the other key. One key, chosen arbitrarily, is used to transform data into a seemingly unintelligible form and is kept secret, while the other is made public. All effective electronic signatures require the use of a 'one-way function' (irreversibility). This means that if a document, signed electronically by Alice with her private key, is sent to Bob, Bob must be able to decrypt the document's signature element with the help of Alice's public key, but must not be able to re-encrypt it with this key. In other words it must be 'computationally infeasible' to derive the private key from the knowledge of the public key. Otherwise the discovered private key could be used to forge digital signatures of the holder.
q ualified certificate (EC Directive term)
- the requirements for an qualified certificate (Art. 2 Nr.10 ESD) are set out in Annex I and II of the ESD: Qualified certificates must contain:
'(a) an indication that the certificate is issued as a qualified certificate;
(b) the identification of the certification-service- provider and the State in which it is established;
(c) the name of the signatory or a pseudonym, which shall be identified as such;
(d) provision for a specific attribute of the signatory to be included if relevant, depending on the purpose for which the certificate is intended;
(e) signature-verification data which correspond to signature-creation data under the control of the signatory;
(f) an indication of the beginning and end of the period of validity of the certificate;
(g) the identity code of the certificate;
(h) the advanced electronic signature of the certification-service-provider issuing it;
(i) limitations on the scope of use of the certificate, if applicable; and
(j) limits on the value of transactions for which the certificate can be used, if applicable.'
- Certification-service-provider issuing qualified certificates must meet the following requirements: They must:
'(a) demonstrate the reliability necessary for providing certification services;
(b) ensure the operation of a prompt and secure directory and a secure and immediate revocation service;
(c) ensure that the date and time when a certificate is issued or revoked can be determined precisely;
(d) verify, by appropriate means in accordance with national law, the identity and, if applicable, any specific attributes of the person to which a qualified certificate is issued;
(e) employ personnel who possess the expert knowledge, experience, and qualifications necessary for the services provided, in particular competence at managerial level, expertise in electronic signature technology and familiarity with proper security procedures; they must also apply administrative and management procedures which are adequate and correspond to recognised standards;
(f) use trustworthy systems and products which are protected against modification and ensure the technical and cryptographic security of the process supported by them;
(g) take measures against forgery of certificates, and, in cases where the certification-service-provider generates signature-creation data, guarantee confidentiality during the process of generating such data;
(h) maintain sufficient financial resources to operate in conformity with the requirements laid down in the Directive, in particular to bear the risk of liability for damages, for example, by obtaining appropriate insurance;
(i) record all relevant information concerning a qualified certificate for an appropriate period of time, in particular for the purpose of providing evidence of certification for the purposes of legal proceedings. Such recording may be done electronically;
(j) not store or copy signature-creation data of the person to whom the certification-service-provider provided key management services;
(k) before entering into a contractual relationship with a person seeking a certificate to support his electronic signature inform that person by a durable means of communication of the precise terms and conditions regarding the use of the certificate, including any limitations on its use, the existence of a voluntary accreditation scheme and procedures for complaints and dispute settlement. Such information, which may be transmitted electronically, must be in writing and in readily understandable language. Relevant parts of this information must also be made available on request to third-parties relying on the certificate;
(l) use trustworthy systems to store certificates in a verifiable form so that:
- only authorised persons can make entries and changes,
- information can be checked for authenticity,
- certificates are publicly available for retrieval in only those cases for which the certificate-holder's consent has been obtained, and
- any technical changes compromising these security requirements are apparent to the operator.'
' r egular' electronic signature (EC Directive term)
- 'means data in electronic form which are attached to or logically associated with other electronic data and which serve as a method of authentication' (Art. 2 Nr. 1 ESD).
- may, at least, not be denied legal effectiveness and admissibility as evidence on the grounds that it is in electronic form, or not based upon a qualified certificate, or not based upon a qualified certificate issued by an accredited certification-service-provider, or not created by a secure signature-creation device (Art. 5 (2) ESD)
Relying Third Party Charter
- defines the representations CAs make and warranties they hold out in respect of certificates
s ecure signature creation device (EC Directive term)
- the requirements for secure signature-creation devices are set out in Annex III of the ESD:
'1. Secure signature-creation devices must, by appropriate technical and procedural means, ensure at the least that:
(a) the signature-creation-data used for signature generation can practically occur only once, and that their secrecy is reasonably assured;
(b) the signature-creation-data used for signature generation cannot, with reasonable assurance, be derived and the signature is protected against forgery using currently available technology;
(c) the signature-creation-data used for signature generation can be reliably protected by the legitimate signatory against the use of others.
2. Secure signature-creation devices must not alter the data to be signed or prevent such data from being presented to the signatory prior to the signature process.'
Back to Main Article
|