Neutral Citation Number: [2019] EWHC 562 (Ch)
Case No: HP-2017-000045
IN THE HIGH COURT OF JUSTICE
BUSINESS AND PROPERTY COURTS
INTELLECTUAL PROPERTY LIST (ChD)
PATENTS COURT
Royal Courts of Justice
7 Rolls Building, Rolls Building
Fetter Lane, London
EC4A 1NL
Date: 11/03/2019
Before :
MR JUSTICE HENRY CARR
- - - - - - - - - - - - - - - - - - - - -
Between :
|
|
TQ DELTA, LLC |
Claimant |
|
|
- and - |
|
|
|
(1) ZYXEL COMMUNICATIONS LIMITED
(2) ZYXEL COMMUNICATIONS A/S |
Defendant |
- - - - - - - - - - - - - - - - - - - - -
- - - - - - - - - - - - - - - - - - - - -
Adrian Speck QC and Nicholas Saunders QC (instructed by Gowling WLG (UK) LLP) ) for the Claimant
Iain Purvis QC, Brian Nicholson and David Ivison (instructed by Pinsent Masons LLP ) for the Defendant
Hearing dates: 24,25,28,29 January, 7 and 8 February 2019
- - - - - - - - - - - - - - - - - - - - -
Approved Judgment
I direct that pursuant to CPR PD 39A para 6.1 no official shorthand note shall be taken of this Judgment and that copies of this version as handed down may be treated as authentic.
.............................
MR JUSTICE HENRY CARR
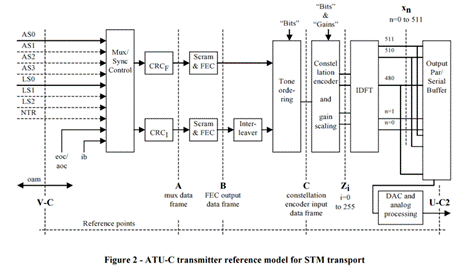
Contents
|
Section / heading |
Paragraph(s) |
|
Introduction |
1-5 |
|
Technical background to DSL / common general knowledge |
6-23 |
|
Introduction to DSL |
6-13 |
|
DSL Standardisation |
14-23 |
|
The Witnesses |
24-35 |
|
Judgment Part A – the 268 Patent |
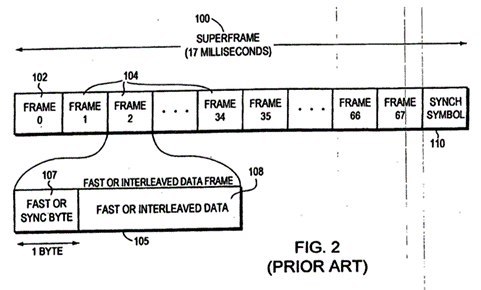
36-187 |
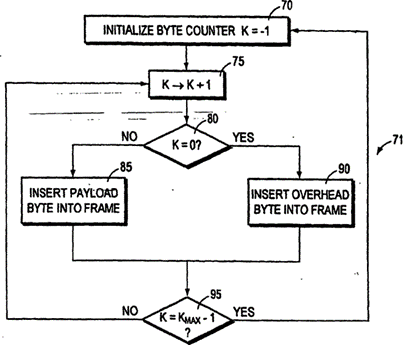
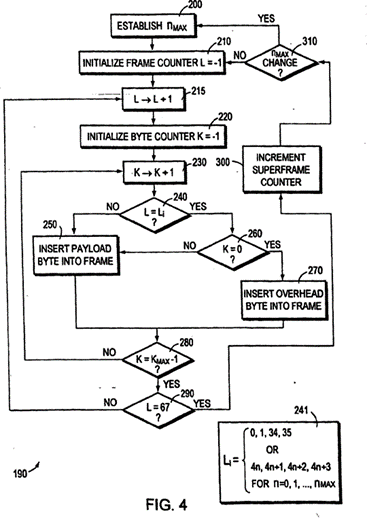
|
Technical background to the 268 Patent / common general knowledge at the priority date |
37-41 |
|
The 268 Patent |
42-67 |
|
The skilled addressee of the 268 Patent |
68 |
|
The issues in dispute in relation to the 268 Patent |
69 |
|
Interpretation of Claim 1 |
70-103 |
|
Legal principles |
70 |
|
Interpretation of “frame” – the parties’ contentions in outline |
71 |
|
A term of art? |
72-78 |
|
“Frame” in the context of the 268 Patent |
79-93 |
|
“specifies” |
94-95 |
|
“n max ” |
96-103 |
|
The prior art cited against the 268 Patent (“Alabama”) |
104-117 |
|
Anticipation by Alabama |
118-120 |
|
Obviousness in the light of Alabama |
121-177 |
|
ZyXEL’s case in outline |
121- 132 |
|
TQ Delta’s case in outline |
133-138 |
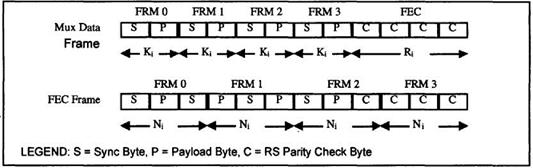
|
Discussion |
139-156 |
|
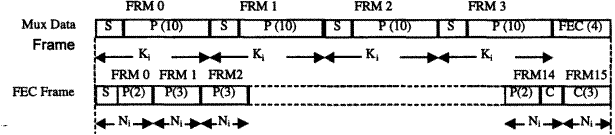
|
Conventional obviousness |
140-147 |
|
|
Lack of technical contribution |
148-156 |
|
ZyXEL’s four alternative cases |
157-176 |
|
Conclusion |
177 |
|
Conditional Amendment |
178-179 |
|
Infringement |
180-187 |
|
Judgment Part B – the 430 Patent |
188-270 |
|
Technical background relevant to Patent 430 / common general knowledge at the priority date |
189-194 |
|
The 430 Patent |
195-208 |
|
Claims in issue |
209-210 |
|
Issues in dispute in relation to the 430 Patent |
211 |
|
Interpretation of “normalising” in Claim 1 |
212-216 |
|
Infringement |
217 |
|
The skilled addressee of the 430 Patent |
218-240 |
|
Legal principles |
219 |
|
Assimilation of complex documents |
220-227 |
|
Internet service providers |
228-231 |
|
Common general knowledge – CRCs and SESs |
232-238 |
|
CRC anomalies expressed as a percentage |
239-240 |
|
Perception of the problem – legal principles |
241-244 |
|
Obviousness in the light of ADSL2/02 |
245-247 |
|
TQ Delta’s submissions in outline |
248-249 |
|
ZyXEL’s submissions in outline |
250 |
|
Discussion |
251 |
|
Focus on CRCs/SESs |
252-254 |
|
Superhuman ability/cherry picking |
255-258 |
|
Step by step approach and hindsight |
259-260 |
|
Secondary evidence – events subsequent to the publication of ADSL2/02 |
261-267 |
|
|
|
|
Overall conclusions |
272
|
|
Annex 1 - Standards of relevance to the 268 Patent and the 430 Patent |
|
|
Annex 2 – Summary diagram prepared by Counsel for TQ Delta |
|
|
Annex 3 - Tables extracted from First Report of Dr Jacobsen |
|
Mr Justice Henry Carr:
Introduction
1. This is a patent claim in respect of two patents which, according to the Claimant (“TQ Delta”), are “essential” in that the relevant standards cannot be practised without infringement of the patents. This trial concerns only technical issues of validity and infringement. The issues of infringement depend on whether the patents are, in fact, essential.
2. The patents in suit (“the Patents”) are EP 1 453 268 “Multicarrier communication with variable overhead rate” (“the 268 Patent”); and EP 1 792 430 “CRC counter normalisation” (“the 430 Patent”). The 268 Patent has a priority date of 26 June 1998. The 430 Patent has a priority date of 25 September 2004. The case in respect of the 268 Patent involves the application of settled principles of law to complex facts. The case in respect of the 430 Patent is more unusual, in that TQ Delta accepted that once the problem addressed by the patent is known, the claimed solution is obvious. However, it contends that invention lay in perceiving the problem at the priority date.
3. The Patents are concerned with Digital Subscriber Line (“DSL”). They have been chosen by TQ Delta from within a substantial portfolio of patents which are DSL related, which it acquired from a company known as Aware Inc. in 2012. DSL technologies are those commonly used to provide fixed line broadband internet to residential and commercial premises. DSL technology is prescribed by internationally recognised technical standards which allow for interoperability between DSL products.
4. The Defendants (“ZyXEL”) are part of the worldwide ZyXEL group of companies, headed by Unizyx Holding Corporation in Taiwan. The group manufactures DSL equipment in China and sells it worldwide for use by consumers and telecoms companies.
5. Each side complained bitterly about the conduct of the other. The usual allegations of “hold-out” and “hold-up” have been asserted, and there have been substantial disputes about the date (if any) for a trial to determine a reasonable and non-discriminatory (“RAND”) set of licence terms. None of those complaints or disputes have any relevance to this judgment, which concerns technical issues only
Technical background to DSL/ common general knowledge
Introduction to DSL
6. The parties did not provide an agreed primer. However, Counsel provided a helpful summary of a much longer explanation which is contained in the expert reports. I consider that the following is a sufficient introduction to the technology and was common general knowledge at the priority date.
7. Standard telephone wiring to premises has for many years been in the form of a twisted pair of copper wires over which voice calls can be carried as analogue signals. In the late 1980s to early 1990s there was an increasing need for homes and businesses to access data networks and this led to using modems to transmit signals at the same analogue frequencies used by telephones for transmitting voice signals. So-called dial-up modems had a relatively low maximum theoretical transmission speed of about 56 kbps. This was because they were constrained to using voice band frequencies. It followed that there was a need to develop higher data rate transmission methods which could utilise the existing twisted pair (it being very expensive to replace the cables installed to each home and business or install additional cables).
8. The basic infrastructure of DSL is shown below:
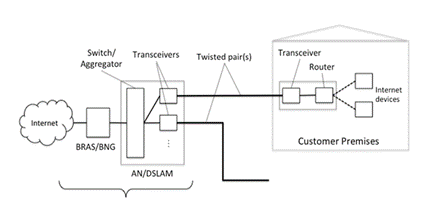
9. The consumer premises are shown on the right hand side with the DSL transceiver connected via the twisted pair to the transceiver at the internet service provider (“ISP”). The DSLAM is the DSL Access Multiplexer which is the central office equipment operated by the internet service provider/telecoms company. It has many ports and switches within it, which aggregate DSL data from many hundreds of households (only one being shown above) before passing it via the broadband remote access server (“BRAS”) to the internet.
10. The key to DSL is that it uses a much wider range of frequencies than those carried by voice signals and this enables higher data rates to be carried across the twisted pair.
11. DSL transmission along the twisted pair is, like the telephone signal, analogue but uses discrete multi-tone (“DMT”) modulation techniques. The idea behind DMT is that signal processing is used to generate a composite signal using multiple sub-carrier frequencies on a single cable. Each of the sub-carriers (or “tones”) is amplitude and phase modulated to transmit digital data using a scheme known as Quadrature Amplitude Modulation (“QAM”). This is a modulation technique in which the carrier signal frequency remains constant but the transmitter varies both the amplitude and phase of a carrier signal based on the data which is being transmitted. If, for example, there are four different combinations of amplitude and phase that can be supported at a particular frequency it is possible to transmit 2 bits (as there are four bit combinations – 00, 01, 10 and 11). The bit combinations are transmitted at a symbol rate which is the number of times each second that a particular combination of amplitude and phase can be transmitted.
12. Some tones will support higher order QAM than others – it follows that the data rates on the various sub-channels thus formed can differ from each other.
13. QAM is used in many wireless systems (such as WiFi and LTE), however unlike wireless systems in DSL bandwidth is not shared amongst a number of users. In DSL each subscriber has his or her own twisted pair which is permanently connected. DSL transceivers typically stay in communication at all times (called either “steady state mode” or “Showtime”) once they have completed initialisation sequences.
DSL Standardisation
14. There have been two main standardisation bodies involved in the development of standards in relation to DSL. The North American ATIS T1E1.4 committee was the first body to develop standards for DSL systems. ATIS (Alliance for Telecommunications Industry Solutions) is a standards developer of ANSI (the American National Standards Institute). The first DSL standard was ADSL and Issue 1 was approved by the T1E1.4 committee in 1995. ADSL means asymmetric DSL. The standard was developed primarily with residential applications in mind – as those applications require a higher transmission rate in the downstream (download) direction than in the upstream (hence the connection is “asymmetric”). ADSL uses frequencies from near 0 to 1.104 MHz. In short transmission loops the maximum required downstream transmission rate in ADSL is of the order of 6Mbps. Issue 2 was approved by the T1E1.4 committee of ATIS in 1998.
15. The ITU Telecommunications Standardization Sector (“ITU-T”) is a division of the International Telecommunications Union (“ITU”) which is a United Nations specialised agency. It adopted the international standardisation of ADSL borrowing heavily from the North American work of ATIS/ANSI. Its first standard, G.992.1 issued in July 1999, is an almost wholesale adoption of T1.413 Issue 2.
16. Following the commencement of standardisation by ITU-T, ANSI stopped developing its own standards, focusing instead on contributing to the international ITU-T developments.
17. Annex 1 to this judgment is a table which sets out the standards of relevance to the 268 Patent (as well as the 430 Patent which I shall consider separately), together with their dates and colloquial names. The standards generated by the ITU-T are referred to as “Recommendations”. It is common for the Recommendations to have been issued and then updated. Where it is necessary to distinguish between different versions of the same standard, the experts have noted the date of release, e.g. ADSL2/02 to refer to the 2002 version of ADSL2.
18. ADSL2 was approved by the ITU-T in 2002 (as Recommendation G992.3) – it uses similar frequency ranges as ADSL but its maximum required downstream transmission rate is 8Mbps. It was followed the next year by ADSL2+ (Recommendation G992.5, written as a delta document relative to ADSL2) which was approved in May 2003. ADSL2+ increased the maximum downstream transmission rate to about 20Mbps.
19. The Very-High-Speed DSL 2 (VDSL2) standard was approved in 2006 (Recommendation G.993.2). This considerably increased the range of frequencies that could be used for transmission and in short loops enables download speeds exceeding 100 Mbps.
20. Because of the short distance over which VDSL2 can operate at high speed it is generally used with so-called “fibre to the cabinet” in which a fibre optic connection is run by the telecoms company to a cabinet in the street and then the existing twisted pairs to each premise are used to carry the DSL signal for the final step. The obvious benefit of this approach is that it is considerably cheaper to run fibre to a single cabinet than to have to install it into each individual building.
DSL Management and reporting Systems
21. The main DSL standards (ADSL, ADSL2, G.lite, VDSL etc.) are concerned with defining how the modems at each end of the subscriber line (e.g. the ATU-C and ATU-R) work and interoperate at the physical level.
22. However, in a practical implementation of ADSL, the ISP will have thousands, if not tens of thousands, of ADSL modems at each local exchange, one for each consumer. A multi-consumer central office terminator (i.e. a collection of ATU-Cs in a single unit) is often referred to as a DSLAM.
23. In practical terms, it is not possible for an ISP to manually monitor the performance of individual ATU-Cs, or even DSLAMs. Instead, automated monitoring and reporting systems are used to determine which lines are working well, and which require attention from maintenance personnel. G.997.1 (also referred to as G.ploam) “Physical layer management for digital subscriber line transceivers” defines the management interfaces which have to be provided by ADSL equipment to allow automated central management.
The Witness
24. The only witnesses were the parties’ respective experts. The Claimant’s technical expert was Dr Georgios Ginis. Dr Ginis has an MSc and PhD in Electrical Engineering from Stanford. His doctoral research concerned signal processing techniques for increasing DSL speeds by eliminating cross-talk. Following completion of his work at Stanford he has been involved in a number of DSL focussed roles at Ikanos (who produced high speed chips for DSL), Texas Instruments, and ASSIA (which provided a software management system for monitoring and diagnosing DSL based internet connections). He is now Head of Technology and co-founder of Sail Internet which delivers internet services to homes and businesses. He was elected a fellow of the IEEE in 2013 “for contributions to transmission optimisation in Digital Subscriber Loops.”
25. The Defendants’ expert was Dr Krista Jacobsen. Like Dr Ginis, Dr Jacobsen has a masters and PhD from Stanford. Her doctoral research concerned multi-tone communications in the reverse channel of hybrid fibre-coax networks (an alternative to DSL). Dr Jacobsen also worked for Texas Instruments following her studies. She has over ten years of experience working in the development and standardization of DSL technologies, including those embodied in the ITU-T Recommendations. Her experience includes work in DSL technologies and the DSL industry both before and after the priority dates of the patents.
26. Dr Jacobsen is also a patent agent and lawyer (admitted to the US-PTO and California bars). She was an IP litigation associate at Covington & Burling for almost two years before leaving to become head counsel for Headwater Partners. She then founded her own law firm in 2014 focussing on IP law and has published widely as a lawyer including on the meaning of RAND terms and duties to disclose patents to standards development organisations.
27. Dr Jacobsen has previously provided expert witness assistance in patent litigation proceedings. She has been retained by ZyXEL and another party, 2Wire , in US District Court proceedings involving TQ Delta. On behalf of 2Wire, she appeared as a technical expert at a claim construction hearing in November 2017 .
28. Mr Purvis QC , on behalf of ZyXEL, made no criticism of Dr Ginis. I find that Dr Ginis was very knowledgeable and was conscious of his duty to assist the court. His evidence was helpful. Mr Speck QC, on behalf of TQ Delta, accepted that Dr Jacobsen was also very knowledgeable and did her best to comply with her obligations to assist the court. I agree, and I also found her evidence helpful. At certain points during her cross-examination she showed fairness and objectivity in accepting points that were put to her during cross-examination, even if they were adverse to ZyXEL’s case. She was an articulate witness, and I received a useful education in the relevant fields from both experts.
29. However, Mr Speck had some observations as to Dr Jacobsen’s dual role as US patent lawyer and expert witness, which, he suggested, placed her in a difficult position. These observations were primarily directed to Dr Jacobsen’s written reports in relation to the 268 Patent. In summary:
i) Dr Jacobsen became involved in these proceedings at a relatively late stage, and this resulted in wholesale changes to ZyXEL’s case . In relation to the 268 Patent, the prior art previously relied upon was abandoned and Alabama was pleaded, a piece of prior art identified by Dr Jacobsen herself from searching through her files. Similarly, the prior art pleaded against the 430 Patent was abandoned, and the claim that the Patent was obvious over the ADSL 2 standard was substituted in its place.
ii) Dr Jacobsen explained during cross-examination that the various non-infringement arguments which were relied upon by ZyXEL (at least at one stage in the proceedings) were formulated by her.
iii) Dr Jacobsen has had considerable involvement in acting against TQ Delta. She is acting against TQ Delta in respect of five patent families in the US litigation. With the addition of the 268 Patent, which is not in issue in the US proceedings, she is acting in proceedings against six of TQ Delta’s patent families and last year this work accounted for a significant proportion of her income.
iv) She has repeatedly argued that TQ Delta was wrong on numerous issues and had sent an email to ZyXEL’s solicitors which suggested (albeit in a humorous tone) that TQ Delta was generally wrong.
30. In the light of this, Mr Speck suggested that Dr Jacobsen had failed to take steps to insulate herself against the risk of being an advocate for ZyXEL and had in certain instances in her reports descended into argument.
31. As to Mr Speck’s points, I see no reason why an expert should not identify relevant prior art. I reject any suggestion that Dr Jacobsen was in any way influenced in her testimony by the income that she had received in acting against TQ Delta. The number of cases in which she is acting against TQ Delta raised a legitimate concern about Dr Jacobsen’s objectivity, but I was satisfied from her oral evidence that she was conscious of her duty to be fair and objective.
32. It is, however, correct that her first report contains a variety of non-infringement arguments that were, wisely, not pursued by Mr Purvis. The arguments that were abandoned were extremely weak. In relation to the 268 Patent, Dr Jacobsen’s first report contains much argument as to claim construction, which would have been better left to the lawyers. In this respect, her report had no regard to the basic principles for admissibility of expert evidence, as set out by Floyd J, as he then was, in Qualcomm v Nokia [2008] EWHC 329 (Pat) at [9] and [11]:
“9. It is for the court and not the witnesses to come to conclusions about what the claim means. Subject to the well known exception about technical terms with a special meaning, the construction of a patent is a question of law. So an expert report which seeks to parse the language of the claim, and opine that a particular ordinary English word can only in his opinion have a particular meaning is not admissible, or helpful. Both sides in the present case are guilty of adducing evidence of this kind.
….
11. None of the above requires the expert to go through the claim and give his definition (wide or narrow) of every word or phrase in it. The written evidence in the present case suffered from this excess. Some of the cross examination did as well. It sometimes takes longer to intervene and stop it than it does to let it happen. It should not start.”
33. Having heard her evidence, I do not attribute this to a lack of objectivity on behalf of Dr Jacobsen, but rather to some confusion about her role in respect of the 268 Patent. She explained that she was asked to give an opinion as to whether she agreed with the non-infringement arguments pleaded by ZyXEL at the time of her first report, and she agreed with all of them (and added some reasons of her own). In my view, she was put in an unfortunate position, which was not of her own making. This meant that her cross-examination was a more difficult experience than it ought to have been. Dr Jacobsen should have been instructed by ZyXEL’s legal team that arguments as to claim construction were not a matter on which she should give evidence. It does not appear that she was made aware of the principles applied by the UK Courts as to claim construction, and therefore it is perhaps unsurprising that arguments contained in her report do not have regard to those principles.
34. In the end, this question is far from central to the issues which I have to decide. As I have said, certain arguments of non-infringement of the 268 Patent, which were previously relied upon by ZyXEL, are no longer pursued. What continues to matter is the experts’ views as to the live issues in the litigation, and the technical reasons which they have provided to support those views. In some instances I accept the reasoning of Dr Ginis, and in other instances the reasoning of Dr Jacobsen. As is commonly the case, evaluation of the expert evidence is more nuanced than merely accepting the totality of evidence of one expert.
35. Mr Speck also submitted that Dr Ginis had experience around the priority date of the 430 Patent that was more relevant to its field than Dr Jacobsen. He argued that shortly after the priority date, Dr Ginis was working in a field close to that of the 430 Patent, whereas Dr Jacobsen was working for Texas Instruments making chipsets. I reject this submission. At the priority date, Dr Jacobsen and Dr Ginis were both working for Texas Instruments. Dr Ginis was a systems engineer at Texas Instruments and worked on system design of integrated chipsets for ADSL and DSL. During that period he also represented Texas Instruments in DSL standards meetings of the T1E1.4 committee. Dr Jacobsen was Texas Instruments’ lead DSL standards strategist and developed and presented many technical proposals for the relevant standardisation bodies. She was very knowledgeable about the standards that are relevant to the 430 Patent and well qualified to give evidence concerning the issues raised by that Patent.
JUDGMENT PART A – THE 268 PATENT
36. As the priority dates of the Patents are more than six years apart, and their subject matter is different, I will consider them in separate sections of this judgment.
Technical background to the 268 Patent/common knowledge at the priority date
37. In common with other telecommunications standards, ADSL operates using a protocol stack in which higher protocol layers provide data to lower layers. This is based on the well-known Open Standards Interconnection (‘OSI’) model in which the operations carried out in the various layers are transparent to each other. Each layer adds control information (overhead) to the payload data it carries. A higher level’s overhead becomes a lower level’s payload – a process known as ‘encapsulation’.
38. The 268 Patent is concerned with the lowest layers which set out the various protocols governing data communication. In common with other layers, in the bottom physical layers there are various sub-layers as data is processed sequentially before it is finally converted to an analogue signal and transmitted across the cable using DMT. The pre-priority ADSL standard (T1.413 Issue 2) sets out the processing sequence carried out by a transmitter as follows:
39. The ADSL1 standard (T1.413 Issue 2) contains a diagram (Figure 2) setting out how data is transmitted. Counsel for TQ Delta prepared a summary diagram which further illustrates this process (which I have included at Annex 2 to this judgment) and described the data transmission process as follows:
i) Starting with the transmitter shown on the left hand side of the diagram, at the top level the Mux Data Frame (‘MDF’) is formed by multiplexing data received from the higher layers in the protocol stack. MDFs consist of one byte of overhead data followed by a given (but variable) number of bytes of multiplexed higher level data. Multiplexing is the process where multiple streams of data are combined into a single bit stream. The overhead in the diagram is shown as the first red byte with the remainder payload within the MDF shown as white. At this level the system uses the position of bytes in the frame to identify which amongst them are overhead. The MDFs are constructed by the transmitter at a rate of 4kHz.
ii) The next step is that the bits forming the MDFs are scrambled . Scrambling is a common process in telecommunications. One reason it is beneficial in digital transmission is that transmitters and receivers are not efficient at transmitting long sequences of 1s or 0s. ADSL uses a scrambler in which the input bit stream is scrambled using an algorithm in which the output bits are dependent not only on the value of the input bit but also that of previous inputs. The input bit is thus scrambled across a large number of output bits – there is no simple one to one correlation between input and output bits. Every bit that comes in continues to have an effect in the system as the effect goes round and round within the scrambler. This can be seen from the following diagram in T1.413 Issue 2:

iii) The binary data streams are scrambled using an algorithm in which the output (d’ n ) is dependent on the input (d n ) and the n-18 th and n-23 rd outputs as above. It is a convolutional encoding scheme. Following scrambling there is no single place you can point to and say that is where a particular bit from the MDF has ended up. It is for this reason that the diagram depicts scrambled data spreading out beyond the equivalent of the two MDFs shown at the top level of the diagram with tramlines above and below the scrambled data to depict an equivalent number of bits to that which made up the two MDFs.
iv) The next step is the formation of the Forward Error Correction (“FEC”) codeword. FEC is a way to introduce redundancy such that when errors occur not only are they detected but they can also be corrected as long as there are not too many of them. The error correcting code can completely correct the errors so long as the number of errors contained within the data is not above a threshold. The FEC bytes are additional bytes which are added onto the end of the scrambled data over which the FEC has been calculated (shown in the diagram in blue). The consequence is that the volume of data expands at this point.
v) The next step is the creation of the FEC output data frame – the FEC codeword is segmented into frames.
vi) Interleaving is then carried out on the FEC output data frames. The interleaving assists error correction in the presence of certain types of noise on the line – in particular errors that come in bursts. The basic idea of interleaving is that the bytes are shuffled with the result that an error burst does not overly affect one FEC codeword. A side-effect of interleaving is the introduction of delay (as bits are shuffled back from when the FEC frame would have been fully transmitted). An illustration of interleaving taken from Dr Jacobsen’s first report is shown below:

vii) Typically, interleaving takes place across many FEC codewords rather than just the four shown in the diagram above. The interleaved bits are then ordered into the tones to produce a constellation encoder input data frame. This is the last place in the transmission scheme where the system deals in bits.
viii) The constellation encoder takes the tone ordered bits and translates them into a set of complex numbers which represent points on a constellation diagram. Depending on the scheme used, a particular point in the constellation represented by a complex number can encode multiple bits. The numbers are used to modulate the tones in the frequency domain to enable transmission.
ix) The complex numbers are then subjected to an Inverse Discrete Fourier Transform (“IDFT”). This is used to generate a set of points which are basically a set of samples of the waveform to be transmitted on the wire.
x) The final step before transmission is for the set of points to go through a digital to analogue converter (“DAC”) before it is transmitted on the wire. The signal that is transmitted is formed into a superframe consisting of 68 data symbols followed by a synchronization symbol. These provide windows of time within which a particular waveform is on the line and can be sampled by the receiver. The synchronization symbol helps the receiver to identify the timing boundaries between superframes. The symbols thus transmitted are at a slightly higher rate than 4kHz to allow for the insertion of the synchronization symbol. The rate at this level is 4.058 kHz.
xi) The actual wave that is transmitted across the twisted pair shown at the bottom of the diagram is analogue. Starting at the bottom of the diagram on the right hand side, the received signal is processed using an analogue to digital converter to recover a set of points (or samples) corresponding to the waveform that was transmitted. They are then processed by a discrete Fourier transform to recover the complex numbers corresponding to the constellation points. There is a limited range of messages that could be transmitted and the receiving end knows that only particular modulated signals are valid and assumes that the nearest one to that is the one that was sent and interprets it accordingly.
xii) The constellation decoder then recovers the constellation encoder input data frame from the complex numbers and a bit stream is again formed. This is then de-merged and the bits from the various tones assembled into an interleaved bit stream.
xiii) It is de-interleaved and the FEC output data frames are recovered. The FEC codewords are identified and forward error correction is carried out to attempt to correct any errors in the transmitted bit stream.
xiv) At that point a scrambled stream of data is formed which is then de-scrambled (by applying the inverse of the convolutional scrambling process) before the MDFs shown on the top right hand side are reassembled.
xv) Because the overhead in the reassembled MDFs is to be found in the first byte of the MDF, it can then be identified on the basis of its position within the MDF and used as appropriate.
40. One can talk of a superframe at both the MDF level and at the DMT symbol level. At the MDF level it is a repeating series of 68 MDFs ticking along at 4kHz. At the DMT symbol level it is a repeating series of 69 symbols on the wire ticking along at slightly more than 4kHZ (it is in fact 4.058kHz).
41. At the DMT level the repeating sequence is used for timing and synchronisation. At the MDF level position is used – both in terms of position of the byte within the MDF, but also position of the MDF in the superframe sequence of 68 MDFs.
The 268 Patent
42. Paragraph [0002] of the 268 Patent defines the field of the invention. It specifically relates to a multicarrier communications system and method that are able to “controllably change an overhead channel data transmission rate”.
43. Paragraphs [0003] – [0016] refer to prior art. Paragraphs [0003] to [0008] describe certain basic aspects of DSL systems, which I have considered as a part of the technical background.
44. Paragraph [0009] explains that communication between an ADSL transmitter and an ADSL receiver “is by way of ‘frames’ of data and control information”. It discloses that:
“In a presently-used form of ADSL communications, sixty eight data frames and one synchronization frame form a "superframe" that is repeated throughout the transmission. The data frames carry the data that is to be transmitted; the synchronization or "sync" frame provides a known bit sequence that is used to synchronize the transmitting and receiving modems and that also facilitates determination of transmission subchannel characteristics such as signal-to-noise ratio ("SNR"), among others.”
45. Paragraph [0010] refers to the ANSI T1.413 Issue 2 standard for full rate ADSL. It also refers to the intended G.lite standard and states that the bandwidth used by G.lite will be approximately half that of a full-rate ADSL system.
46. Paragraph [0011] discusses further “frames” and “superframes”. It states that:
“A superframe is 17 milliseconds in duration. A frame is effectively 250 microseconds in duration (or conversely, the frame rate is approximately 4 kHz) and is made up of a collection of bytes (with one byte corresponding to 8 bits).”
47. Paragraph [0012] discloses that during steady state mode, each frame of data is made up of an overhead section and a payload section whereby the overhead section comprises the first byte of each frame and carries information that is used to manage communications between the two connected DSL modems. It explains that the payload section contains the actual user data to be communicated. Paragraph [0012] lists the types of data which the overhead section may comprise; these are the overhead data carried in the fast or sync bytes in reduced overhead mode in T1.413 Issue 2.
48. Paragraph [0013] discloses that the first byte in each frame is an overhead data byte, termed a sync byte when interleaving is employed, and a fast byte when interleaving is not employed. Paragraphs [0014] and [0015] describe the distribution of overhead bytes in reduced overhead mode with "merged" fast and sync bytes in T1.413 Issue 2. This is illustrated by Table 1 of the 268 Patent which is taken from T1.413 Issue 2 and is reproduced below.
|
Frame Number |
(Fast Buffer Only) Fast Byte Format |
(Interleaved Buffer Only) Sync Byte Format |
|
0 |
Fast CRC |
Interleaved CRC |
|
1 |
IB0-7 |
IB0-7 |
|
34 |
IB8-15 |
IB8-15 |
|
35 |
IB16-23 |
IB16-23 |
|
4n+2, 4n+3 with n=0…16 n≠8 |
EOC |
EOC |
|
4n, 4n+1 with n=0…16, n≠0 |
AOC |
AOC |
49. Dr Ginis provided the following explanation of Table 1, which I accept. In T1.413 Issue 2 the type of overhead data carried in the fast bytes and sync bytes was assigned according to the MDF number shown in the left hand column of Table 1. There are 68 MDFs and therefore 68 fast bytes or sync bytes in a superframe. Four of those sync/fast bytes are assigned to a CRC byte and Indicator Bits and the remaining 64 are assigned to ADSL Overhead Channel ("AOC") or Embedded Operations Channel ("EOC") data.
50. Table 1 is discussed at [0015] of the 268 Patent. The first overhead byte in the first frame is used to transport CRC data. The first byte in the second frame is used to transport the first 8 indicator bits. The first byte in the 34th frame is used to transport the eighth to the fifteenth indicator bits. The first byte in the 35th frame is used to transport the sixteenth to the twenty-third indicator bits. The first byte in all the remaining frames alternates between either EOC data or AOC data.
51. The Patent explains that this conventional scheme gives rise to disadvantages. When actual EOC or AOC data are not available for transport, which can often occur, predetermined dummy bytes are used instead. This is wasteful, as explained at [0016]. The Patent identifies the following disadvantages with the conventional scheme:
i) Since one byte out of each frame in each superframe during conventional DSL communications is dedicated to overhead data, the corresponding overhead data rate is invariably fixed at 32 kbps and is not changed when either the payload data transmission rate changes or when no actual EOC or AOC data are available for inclusion in the frame.
ii) Some telephone lines used in DSL communications are of such poor quality that the maximum possible DSL data transmission rate using such lines may not exceed 128 kbps. This means that when DSL communications are carried out over such poor quality lines, an undesirably large proportion (e.g., up to 25%) of the DSL communications system's throughput may be used to transmit overhead data.
iii) At any given time during a given communications session, the total communications bandwidth is constant. This means that communications bandwidth that otherwise would be available to transmit payload data is unnecessarily consumed in transmitting overhead data.
52. The consequence is that communications bandwidth that would otherwise be available to transmit payload data is unnecessarily consumed in transmitting overhead data.
53. Paragraph [0017] sets out the general object of the invention, which is to:
“ provide a multicarrier communications system and method that overcome the aforesaid and/or other disadvantages and drawbacks of the prior art, and more specifically, to provide such a system and method wherein the overhead data transmission rate during a communications session may be changed and/or selected.”
54. Paragraphs [0018] – [0019] provide a summary of the invention, which is said to overcome the drawbacks of the prior art. [0018] states that:
“ In the system and method of the present invention, the overhead data transmission rate may be changed and/or selected. More specifically, this rate may be selected during an initial negotiation process and/or during a steady state mode of operation.”
55. Paragraph [0019] discloses an embodiment of the invention, where the allocation of the bytes to either overhead or payload is said to be “flexible (i.e., changeable and/or selectable)”. The 268 Patent states that:
“ Whereas in the prior art, the first byte in each frame is dedicated to overhead data regardless of whether there is a need to transport overhead data or not, in this embodiment of the present invention, the overhead data transmission rate is determined during start-up and can be modified during steady state mode. ”
56. Under the heading “Flexible Overhead Allocation” the 268 Patent discloses an embodiment of the invention wherein “both the number of bytes and the frame(s) comprising overhead data may be selected”. By selecting the number of frames that comprise overhead data, and the number of bytes allocated to overhead data in those frames, the amount of throughput that is dedicated to overhead data can be modified. This is said to be a marked departure from conventional DSL systems wherein the amount of throughput that is dedicated to overhead data is unchangeably fixed at 32 kbps. Paragraph [0021] discloses a further embodiment where it is possible to select which of the superframes are to carry overhead data-containing frames. This is said to introduce another degree of freedom in allocating the overhead and payload data transmission rates.
57. The overhead data transmission rate may also be selected based on the relative priorities of payload and overhead data to be transmitted ([0022]). The modems may exchange control commands during their initial negotiation or handshake phase to establish which of the frames and/or superframes contain overhead data, and the number of bytes of overhead data in the selected frames. The modems may store sets of parameters designating which bytes, frame(s), and superframe(s) are to be reserved for the transfer of overhead data and then choose one of the sets of parameters based on the control commands ([0023]).
58. Once the overhead data transmission rate has been established, it may be adjusted thereafter during steady-state operation ([0024]). The modems may negotiate a change and coordinate the transition to a different overhead data transmission rate ([0025]-[0029]).
59. Illustrative embodiments are then described at [0033] onwards. In particular, Figure 2 is said to illustrate a conventional data superframe format, which is reproduced below. This shows a superframe which spans 17 milliseconds. During that period 68 frames are processed and transmitted (numbered from 0 to 67) with a synchronisation (“synch”) symbol at the end which is inserted by the modulator prior to transmission. Within the superframe lasting 17ms, each of the 68 frames is depicted as consisting of a fast or sync byte followed by fast or interleaved data bytes (depending on whether interleaving is deployed).
60. Paragraphs [0041] to [0043] describe Figure 3 of the 268 Patent, which is a flowchart of a conventional process which has previously been used “to determine allocation of overhead and payload bytes in each frame structure 105 to be generated for transmission”.
61. The process in Figure 3 begins by initializing a byte counter "K" to -1. The counter is then incremented by one and compared to zero. If the incremented counter equals zero, an overhead byte is generated and inserted into the frame. The type of overhead byte generated is determined in accordance with the scheme set out in Table 1 of the 268 Patent. If the incremented counter differs from zero, a payload byte is inserted into the frame. This continues until the frame is complete with K bytes. The resulting frames each contain one fast or sync byte followed by a portion of payload bytes as shown above in Figure 2.
62. Paragraphs [0044] and [0045] describe the " New Overhead Allocation Table " in Table 2 of the 268 Patent, which is said to be in accordance with the invention. Table 2 is reproduced below.
|
Frame Number |
(Fast Buffer Only) Fast Byte Format |
(Interleave Buffer Only) Sync Byte Format |
|
0 |
Fast CRC |
Interleaved CRC |
|
1 |
IB0-7 |
IB0-7 |
|
34 |
IB8-15 |
IB8-15 |
|
35 |
IB16-23 |
IB16-23 |
|
4n+2, 4n+3
with n=0…n max n≠8 |
EOC or sync |
EOC or sync |
|
4n, 4n+1 with n=0… n max , n≠0 |
AOC |
AOC |
63. The 268 Patent describes, in the context of this embodiment, the introduction of a new parameter n max which is negotiated by the transceivers at initialisation or during steady state mode. Selection of this parameter programs the EOC/AOC transmission rate by determining into which frames EOC/AOC overhead bits are inserted. In Table 2, a sync byte carrying EOC is inserted into every 4n+2, 4n+3 bytes where n goes from 0 to n max . The parameter thus operates to cap the number of frames into which the overhead is inserted.
64. Figure 4 shows the flow diagram for the new process which enables selective insertion of overhead into the frames as they are assembled. The same byte counter used in Figure 3 is used in Figure 4 but there is now also a frame counter, "L", which is incremented each time a frame is completed. An overhead byte is inserted into the first byte of the frame whenever L=L i , where L i is the set of frames in the left hand column of Table 2 as determined by the parameter n max . Figure 4 also allows that the n max parameter can be reset for each superframe.
65. The claims that are said to be independently valid are Claims 1, 5 and 8. Claim 1 is a method claim. Claim 5 is to a transceiver incorporating the method in Claim 1 and Claim 8 is to a device claim including a transceiver according to claim 5. As the same issues are in dispute in relation to Claims 1, 5 and 8, the case turns on validity and infringement of Claim 1.
66. Claim 1 may be separated into the following integers:
“[1] A method of controlling a transmission rate of overhead data bits
[2] in a sequence of frames in a digital subscriber line communication
[3] using multicarrier modulation,
the method being characterized by :
[4] programming the transmission rate between a minimum rate and a maximum rate
[5] and selecting a value for a first parameter (n max ) that specifies which frames in the sequence of frames contain overhead bits and which frames in the sequence of frames do not contain overhead bits.”
67. Although the disclosure of the 268 Patent takes some time to understand, the inventive concept of Claim 1 is relatively straightforward. It claims a method for controlling the transmission rate of an overhead communication channel, where the overhead consists of bytes in a sequence of frames. Control is achieved by providing for overhead (previously present in every frame) to be omitted from some frames to make more room available for additional payload. The 268 Patent provides for the setting of a parameter which ‘specifies’ the frames in which overhead is to be included or not included. This allows the transmitter and the receiver to know which frames to insert overhead into (in the case of the transmitter) and which frames to treat as containing overhead (in the case of the receiver).
The skilled addressee of the 268 Patent
68. In contrast to the 430 Patent, where there was a significant dispute about the identity and attributes of the skilled addressee, the parties were in agreement as to the skilled addressee of the 268 Patent. Dr Ginis set out his view at [42] – [43] of his first report, which was not disputed by Dr Jacobsen. His evidence, which is an adequate description for present purposes, is that
i) the skilled person in relation to the 268 Patent is a DSL communications systems engineer with experience in DSL systems architecture and an interest in the design and implementation of DSL transceivers;
ii) The skilled person may be a DSL systems architect, in which case she or he has a strong understanding of transceiver hardware and software architectures and has the skills to convert DSL product requirements into a DSL system architecture specification. Product requirements may include standards requirements;
iii) Alternatively the skilled person may be a DSL software or hardware architect, depending on whether the framing functionality is predominantly implemented using software or hardware. The skilled person has a strong understanding of DSL transceiver software/hardware architectures, and possesses the knowledge required to map product requirements to a DSL software/hardware architecture specification.
The issues in dispute in relation to the 268 Patent
69. The disputed issues in relation to the 268 Patent are:
i) Interpretation of the following language in Claim 1: “frame”; “specifies”; “Nmax”;
ii) Whether the 268 Patent was obvious at the priority date in the light of the cited prior art (“Alabama”);
iii) If the 268 Patent was obvious, whether a conditional amendment to the 268 Patent is permissible;
iv) Infringement - whether the 268 Patent is essential to (a) ADSL2/2+ and/or (b) VDSL2;
Interpretation of Claim 1
Legal principles
70. The correct approach to claim interpretation, which is purposive, is set out at [18] and [19] of the judgment of Floyd LJ in Saab Seaeye Limited v Atlas Elektronik GmbH [2017] EWCA Civ 2175. The parties were agreed that no issues arise as to equivalents in the present case. Therefore, the further principles explained in Actavis UK Ltd v Eli Lilly & C o [2017] RPC 21 and Icescape Limited v Ice-World International BV & Ors [2018] EWCA Civ 2219 are not relevant.
Interpretation of “frame” – the parties’ contentions in outline
71. ZyXEL contended that at the priority date, “frame” was a term of art. It meant a group of bytes sent in a single DMT symbol period. This interpretation, according to ZyXEL, is supported by the use of the word “frame” in the standards, which was common general knowledge to the person skilled in the art at the priority date. It contended that “frame” is used in the same way in the 268 Patent and in Alabama. TQ Delta contended that the word “frame” as used in Claim 1 of the 268 Patent would be understood by the skilled addressee as a reference to MDFs. Any other interpretation would be technical nonsense, as, in TQ Delta’s submission, both experts well understood.
A term of art?
72. The first question is whether “frame” was a term of art which had a clear meaning at the priority date. “Term of art” refers to a word or phrase which has a special meaning in the relevant field, see e.g. Qualcomm v Nokia (supra). ZyXEL argued that: “frame” was defined in the standards; that gave it a special meaning; and that special meaning represented the understanding of the skilled person at the priority date.
73. I do not accept this submission. I consider that the word “frame” was capable of having a number of different meanings at the priority date, and its meaning was context dependent. In other words, its meaning depended on what was being described, and the technical purpose of the description. If “frame” had a special meaning in the art then, in my view, both experts would be well aware of this. Obviously, they would have set out that meaning in their written expert reports. Neither expert did so. In particular, Dr Jacobsen did not suggest in any of her three reports that “frame” was a term of art which had the special meaning suggested by ZyXEL. Her evidence, which I consider further below, is inconsistent with this suggestion.
74. I also do not accept ZyXEL’s submission that Dr Ginis accepted during cross-examination that “frame” was a term of art in this field, which meant whatever was indicated in the standards at the priority date. I do not consider that Dr Ginis understood the legal meaning of “term of art”, which is far from self-evident.
75. As to the standards, the earliest ADSL1 Standard (T1.413 Issue 1 published in 1995) did not define “frames”, as ZyXEL accepts. ZyXEL’s case is that the standard equated frames with the bytes contained in a single data symbol. In particular, the text at 6.2.1 identified as ‘data symbols’ the elements which are shown in the diagram being described (Figure 2) as ‘data frames’. This figure is shown in this judgment at paragraph 38. However, Dr Ginis considered that this text contained an inaccuracy or ambiguity. I do not consider that it establishes that “frame” was a term of art. A better reference, from ZyXEL’s perspective is [6.2.2] of the standard. In this paragraph, T1.413 Issue 1 equates the frames being assembled at each of the three reference points A-C in Figure 2 with data symbols, stating:
“…because of the addition of FEC redundancy bytes and data interleaving, the data symbols (i.e. bit level data prior to constellation encoding) have different structural appearance at the three reference points through the transmitter.”
76. Figure 2 also differentiates between different types of frames shown at each of the reference points, namely an MDF at reference point A; a FEC output data frame at reference point B; and a constellation encoder input data frame at reference point C. It does not answer the question of which of these frames is being referred to in any given context.
77. The next change to the text of the Standards (after T1.413 issue 2) was after the ITU-T took over the ADSL1 Standard process and published G.992.1 in July 1999. ZyXEL sought to rely upon a link between the concepts of frames and data symbols in G.992.1, and in particular the definition section at p4-5. There, the Standard defined “data frame”, “FEC output data frame” and “Mux data frame”. They are all defined as groupings of bytes over a “single symbol time period” . A symbol time period was also defined in the Standard as the time taken to send a single DMT symbol (at [3.32]).
78. However, G.992.1 was not published until 1999, after the priority date of the 268 Patent. It was not available to the skilled person in 1998. Furthermore, it gives different definitions of different types of frames, and, as with the previous standards, does not answer the question of what type of frame is being referred to in a particular context. Having been asked about the definitions in G.992.1, Dr Ginis strongly disagreed with the suggestion that the 268 Patent was using the word “frame” to refer to a time period and maintained his view that it was plainly referring to MDFs.
“Frame” in the context of the 268 Patent
79. The 268 Patent, and in particular Claim 1, is concerned with “overhead bits”. It seeks to control the transmission rate by specifying frames that contain overhead bits, and frames which do not contain overhead bits. In order to achieve this objective, the receiver must be able to find the overhead bits in an identifiable location. As is apparent from the diagrams at Annex 2, bits do not exist at the lower levels in the process once the complex numbers have been formed. Prior to scrambling and interleaving, such overhead bits are clearly identifiable in an MDF. After scrambling and interleaving, the overhead bits are no longer in that location.
80. Since the claim requires “programming” and “selecting” that “specifies” frames that contain overhead bits, and frames which do not contain overhead bits, it would be understood, in my view, as referring to MDFs. It is only at the MDF level that the receiver can be provided with information via a parameter that can “specify” within the meaning of the claim – it must be able to find the overhead bits in an identifiable location, which is not possible after scrambling and interleaving. This interpretation is supported by the fact that the description of the 268 Patent is directed to specifying which MDFs contain overhead and which MDFs do not . Furthermore, the only overhead described in the specification are fast and sync bytes. Fast and sync bytes are inserted at the MDF level by the transmitter and received and processed at the same level in the receiver
81. This interpretation is supported, in my judgment, by consideration of the evidence of both experts. Expert evidence is admissible as to the technical teaching of a patent. Further, in Qualcomm v Nokia (supra) Floyd J said at [10]:
“10. What is both admissible and helpful expert evidence is something rather different: evidence about the technical inter-relationship between rival claim meanings and the teaching of the specification. The expert is well able to assist the Court about the impact of different assumptions about the correct legal construction of the claim. It may be that it is only on one construction of the claim that general technical statements made in the body of the patent about what the invention achieves will hold good. It is perfectly legitimate for an expert to point that out, and to give a technical explanation of why, if the rival construction is adopted, the claim would extend to embodiments which would not achieve the patent’s technical objective .”
82. In her first expert report, Dr Jacobsen expressed the view that the word “frame” was used inconsistently in the 268 Patent, both in its description and its claims. Having referred to Claim 1, she said at [313]:
“There appears to be an issue with Claim 1 in that the “frames” in the preamble do not appear to be the same "frames" as referred to in the remainder of the claim. The skilled person would appreciate that the general disclosure of the patent uses the term “frame” sometimes to refer to what the skilled person would understand to be a mux data frame in ADSL ( see, e.g. , ¶ [0012]), and other times to refer to what the skilled person would understand to be the frames mapped to DMT symbols ( see, e.g. , ¶ [0009]). What matters is the apportionment between user data and overhead data within the overall transmission system. For my following comments, I shall assume that the references to “frames” must be interpreted with a certain amount of flexibility, as this is the only way that the claim can make any reasonable sense.”
83. There are obvious difficulties with this evidence. First, it does not support ZyXEL’s case that frame was a term of art which would be understood to have a special meaning. On the contrary, it contemplates two different meanings of the word in the same document. Secondly, it purports to give a different meaning to the word “frame” as used in the preamble to Claim 1 from the meaning of the same word in the remainder of the claim. This is not purposive construction and was not a construction adopted by Mr Purvis. Thirdly, it specifically recognises that (at least in parts of its general disclosure and claims) the 268 Patent is referring to MDFs.
84. The evidence of Dr Ginis as to the technical teaching of the 268 Patent concerning “frames” was much clearer. He pointed out at [108] of his first report that, without context, the term “overhead data bits” could refer to any data which are not user payload data; for example fast and sync bytes, FEC redundancy bytes, or other overhead such as the bits added for trellis encoding. Similarly, without context, the term “sequence of frames” could refer to any pre-defined blocks of data produced for processing reasons. However, he considered that the 268 Patent was plainly referring to MDFs, for the following reasons:
i) the specification refers only to the types of overhead included in the fast and sync bytes.
ii) Each of the embodiments in the 268 Patent (ie Figure 3, Figure 4, Table 1 and Table 2) are concerned with the allocation of overhead data carried in the fast and sync bytes in the MDFs.
iii) That overhead typically only has meaning at the layer of the system at which it is inserted (and extracted). Lower processes will result in the contents of the MDFs not being identifiable (or at least not meaningfully).
iv) Given that Claim 1 requires the first parameter to specify which frames in a sequence of frames contain overhead bits and which do not, that implies technically that there cannot be a disconnect between the overhead data and the frames that are specified to contain it. At each layer the input data received from the previous layer comprises ‘payload’ data and additional overhead is added to it.
85. I find that Dr Ginis’ reasons for his conclusion are compelling and they were not altered by his cross-examination. Furthermore, the cross-examination of Dr Jacobsen showed that, in reality, there was substantial agreement between the experts on this issue.
86. In particular, Dr Jacobsen was cross-examined about the disclosure of the 268 Patent, including its general technical teaching. She agreed that paragraphs [0012] – [0020], as well as the preferred embodiments, would be understood as referring to MDFs. Her cross-examination also established that the object of the invention, as set out in [0017] could only be understood and realised if “frame” is referring to the MDF level, where fast and sync bytes are inserted; see in particular T2/316/21 – 317/9:
“Q. If you look at paragraph 17, you see that the patent explains that the object of the invention is summarised, and it says it is to overcome the aforesaid disadvantages.
A. Yes, I see that.
Q. So, that disadvantage as we have just been talking about is the fixed mux data frame level overhead, the sync and fast bytes; yes?
A. Pause: It seems to be focused on the fact that there is one sync or fast byte in each mux data frame.
Q. Yes, that is the disadvantage it identifies that it says the invention overcomes.
A. Correct. So there is too much of the bit rate consumed by the transmission of the fast and sync bytes.”
87. Therefore, in my judgment, the testimony of both experts leads to the conclusion that it is only if “frame” is interpreted as “mux data frame” that general technical statements made in the body of the patent about what the invention achieves will hold good. Otherwise, the claim would extend to embodiments which would not achieve the patent’s technical objectives.
88. A contrary argument, relied upon by ZyXEL, is based upon paragraphs [0009], [0011] and Figure 2 of the Patent. Paragraph [0009] refers to a “superframe” in a “presently used form of ADSL communications” in which 68 frames and one synchronisation frame form a superframe that is repeated throughout the transmission. Paragraph [0011] explains that a superframe is 17 milliseconds in duration and a frame is effectively 250 microseconds in duration. Figure 2 is said at [0031] to illustrate “a conventional data superframe format”. It contains 68 frames and one synch symbol. It is further described at [0039] –[0040]. The “frame structure” illustrated at 105 of Figure 2 is an MDF as the first byte (107) is either a sync or fast byte. This was broadly accepted by Dr Jacobsen at T3/323/21 – 325/3 and it is plainly what is shown in Figure 2.
89. The skilled person would understand that there was a known superframe structure at the priority date at both the MDF level and the DMT symbol level. Paragraphs [0009], [00011] and Figure 2 are concerned with how the symbols are placed on sub-carriers (i.e. the sub-channels of 4312.5 Hz bandwidth). This does not detract from the consistent use of the term “frame” in the 268 Patent, which refers to MDFs.
90. ZyXEL submitted that there was specific terminology available if the skilled person wished to draw a distinction between types of frames. MDF, FEC data output frame and consolation encoder input frame were all known terms at the priority date. The patent does not distinguish between types of frames and does not refer to MDFs at all. This is true, however the argument takes no account of the technical understanding of the skilled person to whom the 268 patent is addressed. For the reasons set out above, it would be clear from the disclosure that the language used by the patentee is intended to refer to MDFs. As Mr Speck pointed out, there may have been good reason not to use the term as a limitation, as terminology may change as standards are revised.
91. ZyXEL submitted that “frame” was used in Alabama to mean a grouping of bytes over a single symbol time period. I shall consider the disclosure of Alabama later in this judgment. There is no dispute that “frame” can be used in the sense contended for by ZyXEL. The issue depends upon the meaning of that word in the context of the 268 Patent. It does not help to refer to a different document when addressing this question of interpretation.
92. Finally, ZyXEL submitted that there was a lack of clarity about the meaning of ‘mux data frame’ on TQ Delta’s interpretation. I disagree. Dr Ginis explained the term by reference to Figure 2 of T1.413 Issue 2 (point A) in a section dealing with common general knowledge at the priority date at paragraph 60(a) of his first report. He explained how MDFs are assembled at paragraphs 64 – 66 and illustrated (amongst other things) an MDF at Figure 13. This was not disputed by Dr Jacobsen, who also illustrated MDFs with fast and sync bytes at [207] and [213] of her first report. As shown by the extracts from her testimony cited above, she had no difficulty in understanding what was meant by ‘mux data frame’, and indeed differentiated between different types of frames in her evidence.
93. I conclude that TQ Delta is correct in respect of this issue. “Frame” in the context of the 268 Patent would be understood by the skilled addressee as ‘mux data frame’.
“specifies”
94. ZyXEL contended that this word, as used in Claim 1, means “governs”. It pointed out that the word does not appear in the description, nor in the application as filed. It noted that paragraph [0023] of the description refers to a “set of parameters that will govern how many and which frames and/or superframes will contain overhead data”. This, it suggested, is the nearest that the description gets to this element of the claim.
95. No objection of added subject matter has been pleaded in respect of the introduction of the term, and therefore reference to the application as filed is not relevant. In my view the term is clear on its face and does not require paraphrasing. The method of Claim 1 of controlling a transmission rate of overhead data bits requires programming the transmission rate between a minimum and a maximum rate, and selecting a value for a first parameter that specifies which frames in the sequence contain overhead bits and which do not. The claim, read as a whole, uses the steps of programming and selection of a value for the first parameter to specify which frames contain overhead bits and which do not. In order to do this the receiver must know where to find the overhead data in the frame when it identifies it as overhead. This makes sense if frame means ‘mux data frame’, as I have concluded.
“n max ”
96. Both sides contended that the term n max as used in Claim 1 was non-limiting, although they offered different routes to arrive at this conclusion. Whilst the term n max could be interpreted as meaning the final numbered frame in which an overhead byte is located, Mr Speck submitted, and Mr Purvis agreed, that this is not consistent with the specific embodiment, for the following reasons. First, in many cases, the last frame in which an overhead byte appears is not given by n max at all. Rather the last frame is the middle frame 35 in which the last Indicator Bit (not affected by n max ) appears. Only if n max results in the AOC and EOC bytes being inserted in more than half of the available frames does it determine the last frame with an overhead byte. Secondly, n max does not in fact indicate the actual number of the last frame, even where the AOC and EOC bytes are inserted in more than half the available frames. This is provided by the Table L i , generated by an algorithm of which n max is one element. Further, the last number in Table L i is not actually the number n max itself.
97.  So either n max needs to be written out of the claim or it needs to be interpreted extremely widely. Mr Purvis submitted, and I agree, that it would have to mean something like “a number which (including in conjunction with other elements such as a table) determines not only which frames contain and which do not contain overhead bits, but also which is the last frame in the sequence which contains overhead bits”. At that point the integer becomes essentially non-limiting because any parameter which manages to determine which frames contain and which do not contain overhead bits will also by definition determine the last frame which contains overhead bits.
So either n max needs to be written out of the claim or it needs to be interpreted extremely widely. Mr Purvis submitted, and I agree, that it would have to mean something like “a number which (including in conjunction with other elements such as a table) determines not only which frames contain and which do not contain overhead bits, but also which is the last frame in the sequence which contains overhead bits”. At that point the integer becomes essentially non-limiting because any parameter which manages to determine which frames contain and which do not contain overhead bits will also by definition determine the last frame which contains overhead bits.
98. Mr Speck contended that the use of n max in the claims was no different to the use of bracketed reference signs which are intended to refer to parts of the specific embodiment shown in the drawings. Rule 29(7) of Implementing Regulations the European Patent Convention provides that:
“Where the European patent application contains drawings including reference signs, the technical features specified in the claims shall preferably be followed by such reference signs relating to these features, placed in parentheses, if the intelligibility of the claim can thereby be increased. These reference signs shall not be construed as limiting the claim.”
99. Rule 29(7) was considered by the Court of Appeal in Virgin Atlantic Airways Ltd v Premium Aircraft Interiors UK Ltd [2009] EWCA Civ 1062; [2010] RPC 8. Jacob LJ concluded at [15] – [16] that the skilled reader would know and take into account specific drafting conventions by which a patent and its claims are framed, including r.29(7). With his usual clarity, Jacob LJ explained the purpose of inserting reference numerals into a claim at [17]:
“They help a real reader to orientate himself at the stage when he is trying to get the general notion of what the patent is about. He can see where in the specific embodiment a particular claim element is, but no more. Once one comes to construe the claim, it must be construed as if the numbers were not part of it. To give an analogy, the numbers help you get the map the right way up, they do not help you to read it to find out exactly where you are.”
100. Mr Purvis submitted that n max is a term used in the text of the patent itself and it is not merely a reference sign (i.e. a number) used in the drawings. Therefore, r.29(7) does not apply. Whilst I was initially attracted to that argument, on reflection, I do not accept it. n max is placed in parentheses in Claim 1, just as, for example, reference signs to a transceiver (26, 34) are placed in parentheses in claim 3. Typically, reference signs within the meaning of r.29(7) will be numbers. However the rule is not limited to numbers. In my judgment, n max is a reference sign, used in Figures 4 and 5 of the 268 Patent. It is not to be construed as limiting the claims.
101. Even if this conclusion is wrong, it makes no difference to the result of this case. I agree with the parties that the reference to n max in Claim 1 does not provide any meaningful limitation on the scope of the claim. It follows that I do not accept an alternative interpretation of n max advanced by Mr Purvis for the purposes of non-infringement. That interpretation sought to give a narrow meaning to n max i.e that it limited the claims to the precise ‘truncation’ mechanism of the specific embodiment of the 268 Patent, which I shall now describe.
102. The preferred embodiment of the Patent is described between paragraphs [0044] and [0048]. It does not change the allocation of overhead bytes in frames 0 (CRC byte), 1, 34 and 35 (indicator bits). It is only concerned with the 64 remaining frames allocated in T1.413 Issue 2 to AOC and EOC bytes. It provides a number - n max - to be set by the network and ‘agreed’ on initialisation, which ultimately determines the frames in the superframe which are used for AOC/EOC overhead bytes. In the embodiment described, n max can only be fixed between 0 and 16, limiting the granularity to groups of 4 frames. Setting it as 2 has the effect that only the first 10 frames in the superframe after frames 0 and 1 will be provided with AOC/EOC overhead bytes. The usual sequence of AOC and EOC overhead bytes within a superframe is thereby “truncated”. This will change the overhead transmission rate. This scheme enables the rate to be varied in approximately 2kbps steps up to the 32kbits used in T1.413 Issue 2.
103. However, Claim 1 is not limited to the preferred embodiment, which is intended to illustrate the invention. Specifically, the claim is not limited to the truncation method of the preferred embodiment.
The prior art citied against the 268 Patent (“Alabama”)
104. Alabama is a joint contribution by Centillium Technology and Nortel to the T1E1.4 Working Group. It was presented at the Huntsville Alabama meeting of the Working Group. TQ Delta admitted shortly before the trial that Alabama had been published before the priority date of the 268 Patent.
105. The T1E1.4 Working Group was responsible for developing the T1.413 series of DSL standards. The abstract of Alabama states that it is a contribution which “ reviews an efficient framing structure for G.lite and proposes the addition of a new item for the Living List of open issues for issue 3 of T1.413 ” . Dr Ginis pointed out a standard T1.413 Issue 3 was never published, but that is not relevant to the issues that I have to decide.
106. G.lite used a smaller range of transmission frequencies, and consequently required a smaller amount of computation (hence the name “lite ” ). Dr Ginis explained that, g iven the integrated circuit technology when G.lite was being developed, G.lite systems were expected to have a lower production cost than T1.413 Issue 2-compliant systems. The goal of G.lite was to make DSL technology ubiquitous, with DSL modems included in a large range of computing devices, and usable over almost any twisted pair (or loop). This latter goal also meant that G.lite was expected to operate over very long or very noisy loops. The Signal-to-Noise-Ratio ( “ SNR ” ) on such loops can be very low, such that line transmission speeds are then necessarily also limited to maintain a satisfactory bit error rate. For this reason, it was considered beneficial at the time of developing G.lite to have low overhead transmission when operating G.lite lines.
107. Alabama was intended to address the “low efficiency” that is found when DSL lines are operating at low data rates, which is a consequence of using long (or noisy) DSL loops, where SNR is weak, and higher data rates cannot be achieved.
108. The Introduction to Alabama states that the G.DMT (i.e. T1.413 Issue 2) framing structure exhibits poor bandwidth efficiency when applied to the low bit rates required to provide service on the longest loops envisioned for G.lite. The introduction states that the factors causing low efficiency are “one sync byte per frame ” and “at least one FEC overhead byte per frame”.
109. If there is only a small amount of  data in the FEC frame as a result of noise then there will only be a small fraction of it available to carry payload data once overhead has been included. This is shown in Example 2.1 in Alabama.
data in the FEC frame as a result of noise then there will only be a small fraction of it available to carry payload data once overhead has been included. This is shown in Example 2.1 in Alabama.
110. The top row shows the MDFs as FRM0, FRM1, FRM2 and FRM3. The FEC frames that are formed are shown in the second row. As explained above, by this stage, the contents of the MDFs have been scrambled.
111. In G.DMT Mode in Alabama, the MDFs and the FEC Frames are both generated at a fixed rate of 4 kHz. Since they are specified to contain an integer number of bytes and because the line rate in the example given is only 96kbps, Dr Ginis calculated at [87] of his first report that the size of the FEC frame is 3 bytes.
112. Alabama proposes a new mode of operation, referred to as "G.lite Mode", which can be used as an alternative to the existing “G.DMT Compatible Mode” (referred to in Alabama as "G.DMT Mode"). Alabama makes two proposals: (a) to reduce the rate at which MDFs are generated from 4kHz to 1kHz; and (b) optionally to increase the number of sync bytes contained in an MDF.
113. Each of these proposals has the effect of varying the amount of overhead in aggregate. In the first proposal, MDFs are assembled less frequently, effectively meaning that the size of the MDF is enlarged so that the relative proportion of overhead within it varies. In the latter, additional sync overhead is included in the MDF such that the overhead bandwidth for that category can be maintained at the original rate despite operating in G.lite mode and the benefit of the reduced rate of FEC overhead is still obtained.
114. In the first proposal, in G.lite Mode, the MDF rate is adjusted to 1 kHz using a “G.lite efficiency multiplier”, M=4, and the FEC Frame rate remains as 4 kHz. The result is that 4 frames which are modulated onto the DMT symbols are produced for every MDF. This is shown in the second diagram in the example in Alabama:
Here the MDF is shown as having one sync byte (S) per MDF followed by 10 payload bytes (P).
115. In the diagram, the frames formed once the FEC bytes have been added are depicted as chunks of MDF frames – for example FRM0 is shown as consisting of the sync byte and 2 payload bytes. In fact, because of scrambling, the bits in the MDF are spread across several bits in the FEC frames and there is no direct 1:1 correlation between the bits at the MDF and FEC frame levels. The purpose of the diagram is to show what quantity of data being transmitted is payload; what quantity is sync overhead; and what quantity is FEC overhead.
116. The second proposal in Alabama is a mechanism to maintain the sync overhead bandwidth, S B , despite a change in the MDF rate. A reduction in the MDF rate results in a proportionate reduction in the sync overhead bandwidth as illustrated above. Increasing the number of sync octets per MDF would therefore compensate for this reduction in overhead bandwidth. In G.lite Mode, Alabama states that a sync overhead rate (S B ) of 8, 16 or 32 kbps can be selected. Dr Ginis explained that the skilled person could work out that the parameter N S can be fixed as N S = 1, 2 or 4, which results in 1 sync byte every MDF, 2 sync bytes every MDF, or 4 sync bytes every MDF respectively. N S is constant for all MDFs transmitted in a communications session.
117. In each case the MDFs all contain overhead at the beginning of the frame. Alabama does not teach that some MDFs will and some will not contain that overhead. Rather, it “stretches” the MDFs so that there is a higher ratio of payload to overhead in a given MDF, and optionally increases the number of overhead bytes in the MDF.
Anticipation by Alabama
118. At paragraphs [104] – [123] of its written closing submissions ZyXEL advanced four alternative cases of anticipation of the 268 Patent by Alabama. Alabama was added by amendment in the Re-Re-Amended Grounds of Invalidity. However, anticipation by Alabama was not pleaded. Paragraph 1 of the pleading only asserts that the claims of the 268 Patent were obvious at the priority date in the light of Alabama.
119. Mr Speck objected to the introduction of un-pleaded allegations of anticipation at the close of the trial. I asked Mr Purvis whether he wished to apply to amend the pleading, but he did not do so. Resourceful as ever, Mr Purvis contended that the four alternatives were in fact, allegations of obviousness (contrary to his written closing). Alabama was a paper proposal that required implementation and only disclosed that M=4. Mr Speck maintained his objection on the basis that the allegations were in substance un-pleaded anticipation attacks, and that in any event they had not been set out in Dr Jacobsen’s evidence and therefore there had been no opportunity to answer them.
120. I propose to consider the obviousness attack in the light of Alabama which is set out in Dr Jacobsen’s evidence and has been answered by Dr Ginis. I will then deal with the four alternative attacks set out in ZyXEL’s written closing.
Obviousness in the light of Alabama
ZyXEL’s case in outline
121. ZyXEL pointed out that Alabama addresses the same problem as that identified in the 268 Patent. Alabama starts by addressing the fact that the G.DMT framing structure would cause inefficiencies in the proposed G.Lite system. In particular it states at page 2 that:
“The G.DMT framing structure exhibits poor bandwidth efficiency when applied to the low bit rates required to provide service on the longest loops envisioned for G.Lite.”
…
Factors causing low efficiency:
· One sync byte per frame
· At least one FEC overhead byte per frame…”
122. This is the same problem addressed by the 268 Patent, although the 268 Patent is not concerned with the FEC overhead byte issue. The 268 Patent also refers to the impending arrival of G.Lite, and the fact that it operates at lower bandwidth ([0010]), and identifies the same problem that having a compulsory 1 sync byte per frame means that an undesirably high proportion of data is taken up by overhead ([0016]). I accept this submission. The issue, however, is whether Alabama’s proposed solution to this problem renders obvious Claim 1 of the 268 Patent.
123. Dr Jacobsen explained the reasons why she considered that the solution of Claim 1 of the 268 Patent was obvious at [329] – [333] of her first report, and added to these reasons in her second and third reports. Her position was that there was no real distinction between the teaching of Alabama and Claim 1. Both documents set out to provide the same functionality, namely to reduce the number of sync/fast bytes within a superframe, and did so in a remarkably similar way.
124. Dr Jacobsen referred to two new parameters introduced by Alabama, S B and M. The G.lite efficiency multiplier M is set to 4 for the G.lite efficient framing mode (Alabama at pages 3-5). When FEC is disabled (i.e., R i = 0), which Alabama specifically contemplates (Alabama at page 3), the equations in Alabama reduce to the equations shown in Table H of her report.
|
Total number of bytes per mux data frame: |
K i = 4 x N i |
|
Number of sync bytes per mux data frame: |
N s = S B /8 |
|
Number of payload bytes per mux data frame: |
N p = K i – N s |
125. She considered that the skilled person would understand that the number of bytes per DMT symbol, N i , is known and does not depend on the value of S B . Thus, the only variable in the simplified equations in Table H is S B , which establishes how many sync bytes the transmitter will insert at the beginning of each MDF. Consequently, selecting the value of S B determines the number of sync bytes (S B /8), and, indirectly, the number of payload bytes in each MDF. She considered that the skilled person would also understand from the disclosure of Alabama, that once the total number of bytes, the number of sync bytes, and the number of payload bytes per MDF are known, the exact positions of the sync bytes within the frames of a superframe are also known.
126. Consequently, she reasoned that selecting the value of S B specifies which frames in a superframe contain overhead bits and which frames in the superframe do not contain overhead bits. Evaluating the equations in Alabama programs the transmission rate of overhead data bits between a minimum of 8 kbit/s and a maximum of 32 kbit/s.
127. Insofar as there is any difference between Alabama and the Patent, Dr Jacobsen considered that it lay only in the specific mechanism by which the permitted overhead bytes are allocated within the data frames. Alabama proposed to reduce the number of overhead bytes within a superframe. Dr Jacobsen noted that Alabama makes suggestions as to how to disperse fewer than 68 fast/sync bytes among the 68 frames of a superframe but she thought that it clearly indicated that other approaches are possible (Alabama at page 4, indicating it provides “[o]ne possible allocation”).
128. She reasoned that, faced with a question of how to distribute fewer than 68 overhead bytes among the 68 frames of a superframe, the skilled person would readily come up with any number of different allocation patterns as a matter of mere routine, including the n max approach disclosed by the Patentee, which simply limits the EOC and AOC bytes to the first X frames of a superframe by changing a single value in a pre-existing table. She considered that the skilled person would also readily appreciate that because the indicator bits convey time-sensitive information, allowing their positions within the superframe to shift, as in Alabama, might be undesirable.
129. Dr Jacobsen also produced certain tables (Tables A and B) which appeared to show that the position of the sync bytes in Alabama could be traced down to particular frames. Table B, according to ZyXEL’s opening skeleton, gave “a complete account of the structure of an FEC frame following the teaching of Alabama (with Ri = 0)”. Tables A and B are reproduced in Annex 3 to this judgment.
130. ZyXEL relied on the evidence of Dr Jacobsen to submit that the way in which Alabama chose to effect its first proposal was by changing the definition of ‘mux data frame’ at the initial point of assembly (Reference point A) by allowing it to extend over M data symbol time periods, and keeping the rule that the sync byte is inserted at the beginning of every frame. As discussed above, the MDFs still all contain overhead at the beginning of the frame and Alabama “stretches” the MDFs so that there is a higher ratio of payload to overhead in a given MDF.
131. However, ZyXEL submitted that the technical effect of this description is precisely the same as keeping the definition of ‘mux data frame’ tied to a single data symbol time period and saying ‘insert a sync byte every M frames’. This, it submitted, was simply a matter of nomenclature, a point made by Dr Jacobsen in [50] –[51] of her second report.
132. ZyXEL relied upon a description of this technique in a parallel patent application, where one of the authors of Alabama characterised their idea as follows:
“The inventors have further realised that the requirement for one sync byte per frame is wasteful in many situations. The inventors provide an option to include a sync byte just once for several frames, rather than once per frame.”
This, it suggested, was exactly the point Dr Jacobsen was making.
TQ Delta’s case in outline
133. Mr Speck submitted that the critical point about the MDFs in Alabama, which could not be disputed, was that they still all contain an overhead byte at their start. The frames are made bigger in terms of data content so that the ratio of overhead to payload changes, but overhead is not eliminated from any of the MDFs. Since, as a matter of construction, the claims are concerned with MDFs this was a crucial difference between the 268 Patent and Alabama.
134. TQ Delta’s case was that Alabama taught away from the solution of Claim 1 of the 268 Patent. Dr Ginis’ evidence at paragraphs [112] – [114] of his first report was that the Alabama approach was consistent with the skilled person’s understanding as at June 1998 that MDFs always comprise a sync byte (or fast byte) followed by payload data. There was no reason to suppose that, when presented with the fixed MDF structure in Alabama, the skilled person would consider the solution of the 268 Patent, wherein some MDFs will and some will not contain overhead, specified on the basis of a parameter.
135. Dr Ginis’ response to Dr Jacobsen’s evidence was as follows. He considered that Dr Jacobsen’s approach was inconsistent about which overhead and frames she was comparing. She was really talking about lack of overhead which might arise fortuitously in some frames which are modulated onto DMT symbols but not at the MDF sub-layer. Further, she had to ignore interleaving and scrambling (despite the fact that scrambling is always present whichever data path is under consideration).
136. Dr Ginis explained at [34] of his second report that a superframe can refer to: a superframe of MDFs; alternatively FEC output data frames; or alternatively constellation encoder input data frames (i.e. superframes assembled from the frames assembled at points A, B and C respectively). He considered that Dr Jacobsen’s Table A, which considers sync byte positions within a superframe in the context of the teaching of Alabama jumbled up frames from different levels of abstraction which should properly be kept separate, and was internally inconsistent.
137. TQ Delta’s case was that Alabama does not render any of the claims of the 268 Patent obvious. Taken at a high level, Alabama was about reducing the sync overhead bandwidth overall. It was not about specifying which frames carry sync overhead.
138. TQ Delta also contended that the method of the 268 Patent could be used during Showtime, as expressly disclosed in the description. The method in Alabama is only suitable for use during initialisation and would not work during Showtime. Trying to make the approach in Alabama work during Showtime would introduce considerable complexities, as Dr Ginis explained at [124] onwards of his first report.
Discussion
139. ZyXEL’s case may be considered on two different bases; first, whether the 268 Patent lacks inventive step in the light of Alabama (“conventional obviousness”); and secondly whether the 268 Patent has made no technical contribution to the art.
Conventional obviousness
140. Attractively as this case was put by Mr Purvis, I do not accept it. The argument, and the cross-examination based upon it, was, in my judgment, hindsight reasoning. I did not find the reference to a patent application filed by one of the authors of Alabama of assistance. This was not part of the prior art, and contains a statement which does not appear in Alabama.
141. I have concluded that “frames” in Claim 1 of the 268 Patent would be understood by the skilled addressee as meaning MDFs. I accept the evidence of Dr Ginis that the Alabama approach was consistent with the skilled person’s understanding as at June 1998 that MDFs always comprised a sync byte (or fast byte) followed by payload data. I also accept his evidence that there was no reason to suppose that, when presented with the fixed MDF structure in Alabama, the skilled person would consider the solution of the 268 Patent, wherein some MDFs will and some will not contain overhead, and wherein MDFs which do and do not contain overhead are specified on the basis of a parameter.
142. Having heard the cross-examination of both experts, I was not convinced by Dr Jacobsen’s reasons in support of her conclusion that the 268 Patent was obvious. Although Alabama and the 268 Patent both provide methods of reducing sync and fast byte overhead, that was, in substance, the only similarity identified by Dr Jacobsen. I do not accept that the method of Alabama would be altered, without hindsight, to the method of Claim 1 of the Patent.
143. I also accept Dr Ginis’ evidence that Dr Jacobsen’s approach was inconsistent about which overhead and frames she was comparing. She was relying on lack of overhead which might arise fortuitously in some frames which are modulated onto the DMT symbols but not at the MDF sub-layer.
144. I do not consider that either Tables A or B in Dr Jacobsen’s first report can be relied upon. They do not show that sync bytes in Alabama can be found in specified frames. Dr Jacobsen made clear during her cross-examination that she was not intending to suggest that, but merely that they were intended to show how “things roughly line up”. Her cross-examination also illustrated that she was mixing up frames from different levels, had included a frame number column which could not be applied to Alabama (although it appeared to do so) and that the tables were internally inconsistent. There are many passages in her cross-examination which illustrate these points. It is sufficient to refer to two short extracts:
“18 Q. Now, doctor, not only are you muddling up overhead by trying
19 to look at a different level to identify a frame, this table
20 does not even treat frames consistently as between the left
21 hand pair of columns and the right; does it?
22 A. Well, no, and, as I explained, the objective was to show how
23 would these things roughly line up, if I were to carry the
24 Alabama example out to an entire Superframe's length.”
(T3/399/18-24)
“3 Q. You see, doctor, what I have to suggest to you is that you are
4 not being consistent in this table, and you are jumping
5 between looking at mux data frames when you are giving a
6 number to the G.DMT, and then flipping down to a different
7 level in the processing to the DMT symbol or whatever you want
8 to call it, but you are not looking at the same thing when you
9 try and line up where the sync byte is and give it a frame
10 number in the two right-hand columns?
11 A. Well, I do not disagree with you and I am wondering if you
12 have interpreted the frame number column as applying to the
13 Alabama columns, that was not my intention. I was giving that
14 frame number to show that the G.DMT sync byte index lines up
15 with that, so that the demarcation between the two is that
16 line between the G.DMT framing and the Alabama framing. I was
17 trying to show where they are in time.”
(T3/4034/3-17)
145. Dr Ginis was also correct, I believe, in his criticism that Dr Jacobsen’s tables had ignored the effect of interleaving and scrambling. Dr Jacobsen accepted during cross-examination that scrambling means that there is no single place that you can point to in order to identify a bit after it has been scrambled. The tables took no account of this fact.
146. Finally, Dr Jacobsen accepted during cross-examination that the parameter S B (which she had identified in her first report as the relevant parameter) did not specify which of the MDFs did and did not contain overhead, which is, of course a requirement of Claim 1 of the 268 Patent; see T3/387:25-388:15),
25 Q. So, this is right, is it not, Alabama does address the issue
2 of the overly high proportion of overhead at low line rates;
3 yes?
4 A. It does, yes.
5 Q. But it does not do so by providing for the space allocated to
6 the sync and fast bytes in some of the frames to be allocated
7 to payload? That is right, is it not?
8 A. Well, it defines this longer mux data frame which -- Yes,
9 that is right.
10 Q. And the parameter SB does not specify which of the mux data
11 frames the sync and/or fast bytes are and are not; agreed?
12 A. It does not specify their contents, is that what you asked?
13 Q. It does not specify which of the mux data frames has a sync
14 and a fast byte and which do not?
15 A. Not of the mux data frames, no.
147. For these reasons, I reject the conventional obviousness case, as advanced on the basis of Dr Jacobsen’s evidence. In so doing, I have not relied on the fact that the method of the 268 Patent could be used during Showtime, whereas the method of Alabama is only suitable for use during initialisation and would not work during Showtime. Use during Showtime is not a feature of Claim 1 of the 268 Patent, nor of any claim alleged to be independently valid. Therefore, methods which could not be used during Showtime would fall within the scope of Claim 1. As Floyd LJ stated in Generics UK Ltd v Mylan [2013] EWCA Civ 925 at [39]:
“39. As with any consideration of obviousness, the technical results or effects must be shared by everything falling within the claim under attack. This follows from the fundamental principle of patent law, which underpins many of the grounds of objection to validity, that the extent of the monopoly conferred by a patent must be justified by the technical contribution to the art. If some of the products covered by a claim demonstrate a particular property, but others do not, then the technical problem cannot be formulated by reference to that property. Either the products which do not exhibit the property must be excised from the claim by amendment, or the problem must be formulated by reference to some other, perhaps more mundane, technical contribution common to the whole claim.”
Lack of technical contribution
Legal principles
148. In Generics v Yeda (supra) Floyd LJ observed at [37] that neither the European Patent Convention nor the Patents Act 1977 includes amongst the available grounds of invalidity of a granted patent an objection that the patent does not make a technical contribution to the art. However, the “problem and solution” approach adopted by the EPO to assessment of lack of inventive step necessarily involves isolating from the patent (in comparison with the prior art) some technical contribution or effect. At [40] – [42] Floyd LJ considered the well-known decision of the Technical Board of Appeal of the EPO in
AgrEvo
T 939/92; [1996] EPOR 171. In that case the claim was to a very large class of chemical compounds said to possess herbicidal activity . There was an issue as to whether it was credible that all compounds within the claim possessed the relevant activity. The applicant/appellant argued that, even if the claims included compounds with no technically useful properties, the objection of lack of inventive step did not provide a basis for invalidating the claims. The Board of Appeal rejected this argument. It stated at [2.4.2] that:
… it has for long been a generally accepted legal principle that the extent of the patent monopoly should correspond to and be justified by the technical contribution to the art (see T 409/91, OJ EPO , No. 3.3. and 3.4 of the reasons, and T 435/91, OJ EPO 1995, 188, reasons No. 2.2.1 and 2.2.2). Now, whereas in both the above decisions this general legal principle was applied in relation to the extent of the patent protection that was justified by reference to the requirements of Articles 83 and 84 EPC, the same legal principle also governs the decision that is required to be made under Article 56 EPC, for everything falling within a valid claim has to be inventive. If this is not the case, the claim must be amended so as to exclude obvious subject-matter in order to justify the monopoly. Moreover, in the Board's judgment, it follows from this same legal principle that the answer to the question what a skilled person would have done in the light of the state of the art depends in large measure on the technical result he had set out to achieve. In other words, the notional "person skilled in the art" is not to be assumed to seek to perform a particular act without some concrete technical reason: he must, rather, be assumed to act not out of idle curiosity but with some specific technical purpose in mind.
149. The Board of Appeal concluded at [2.5.3] that:
“It follows from these considerations that a mere arbitrary choice from this host of possible solutions of such a "technical problem" cannot involve an inventive step (see also e.g. T 220/84 of 18 March 1986, No. 7 of the reasons). In other words, the Board holds that, in view of the underlying general legal principle set out in point 2.4.2 above, the selection of such compounds, in order to be patentable, must not be arbitrary but must be justified by a hitherto unknown technical effect which is caused by those structural features which distinguish the claimed compounds from the numerous other compounds.”
150. In Dr Reddy's Laboratories (UK) Ltd v Eli Lilly and Co Ltd
[2010] RPC 9
, the Court of Appeal was concerned with a selection invention – where a patent is sought for a compound or class of compounds which are a selection from a broader class disclosed by a prior document. Jacob LJ summarised the approach of the EPO to that question at [50]:
"Has the patentee made a novel non-obvious technical advance and provided sufficient justification for it to be credible? This is the basis of all the reasoning - see e.g. [2.4.2] of
AgrEvo . A selection which makes a real technical advance in the art is patentable."
Jacob LJ explained that the rule against “arbitrary” selection was to be found in the guiding principle “is there a real technical advance?”
151. In Generics v Yeda , Floyd LJ summarised the principles to be derived from these authorities at [49]. Certain of those principles relate to plausibility, which was an important consideration in Generics v Yeda but which is not in issue in the present case. The following are relevant:
“i) Article 56 of the EPC is in part based on the underlying principle that the scope of the patent monopoly must be justified by the patentee's contribution to the art;
ii) If the alleged contribution is a technical effect which is not common to substantially everything covered by a claim, it cannot be used to formulate the question for the purposes of judging obviousness;
iii) In such circumstances the claim must either be restricted to the subject matter which makes good the technical contribution, or a different technical solution common to the whole claim must be found;
iv) A selection from the prior art which is purely arbitrary and cannot be justified by some useful technical property is likely to be held to be obvious because it does not make a real technical advance;”
Application to the facts
152. Mr Purvis summarised ZyXEL’s case in respect of lack of technical contribution as follows:
i) The concept of the 268 Patent is “fixed overhead transmission is wasteful, so control it by not including an overhead byte in every frame”. The only other feature of the claim, specifying which bytes are where, is necessary in any deterministic system.
ii) The skilled person finds the same inventive concept in Alabama – as described in one of the author’s patent applications “the requirement for one sync byte per frame is wasteful in many situations. The inventors provide an option to include a sync byte just once for several frames, rather than once per frame.”
iii) The precise mechanisms of implementing the inventive concept - using an MDF rate of 1 kHz then rebuilding the frames at 4 KHz for transmission, or keeping the MDF rate at 4 KHz and inserting sync bytes every 4 frames - are irrelevant. For all material purposes they come to the same thing.
153. He submitted that once the problem of wasted overhead bytes was known, the idea of not including overhead in every 4 kHz MDF was inherently obvious, subject only to the “tradition” of having a given fixed overhead. Alabama disclosed both the problem and the idea of getting rid of the “tradition”, removing any barrier to the inherently obvious approach. The mechanism of the patent was simply one of a number of obvious and routine alternatives to implement Alabama’s basic concept of removing and reallocating sync bytes.
154. I have already rejected certain key aspects of this argument when considering conventional obviousness. I have accepted the evidence of Dr Ginis that the Alabama approach was consistent with the skilled person’s understanding as at June 1998 that MDFs always comprised a sync byte (or fast byte) followed by payload data. I have also accepted his evidence that there was no reason to suppose that, when presented with the fixed MDF structure in Alabama, the skilled person would consider the solution of the 268 Patent, wherein some MDFs will and some will not contain overhead, and wherein MDFs which do and do not contain overhead are specified on the basis of a parameter. I reject the contention that the method of Claim 1 of the 268 Patent was simply one of a number of obvious and routine alternatives to implement Alabama’s basic concept of removing and reallocating sync bytes. Rather, it is a different technical solution to that proposed by Alabama. Claim 1 of the 268 Patent, unlike Alabama, is limited to a method wherein some MDFs contain overhead bits and others do not, to be specified by a parameter.
155. In the present case, and in contrast to Agrevo and the other authorities considered above, I am not considering a claim of wide scope, where there is an issue as to whether it is credible that a technical effect is common to everything covered by the claim. Nor am I considering a selection from the prior art which is purely arbitrary and cannot be justified by some useful technical property. The method of Claim 1 is a technical solution, which is different from, and not rendered obvious by, Alabama.
156. There was some debate between the parties as to whether the patented solution has benefits over the Alabama solution. Mr Speck submitted, and I agree, that Agrevo obviousness is not established by suggesting that the prior art provides a solution that might be considered to be as good as that claimed in a patent, by different technical means. Therefore, this debate is, in my view, irrelevant.
ZyXEL’s four alternative cases
Can ZyXEL rely on these alternative cases?
157. As explained above, ZyXEL relied upon four alternative cases of anticipation in its written closing. As anticipation was not pleaded, and no application to amend the pleading was advanced, it submitted that it was entitled to rely upon such cases as obviousness attacks. However, obviousness is a matter of evidence. Where the issues were not raised in ZyXEL’s evidence, it is necessary to ensure that allowing these matters to be raised during closings is not unfair to TQ Delta. Such unfairness would arise if the new attacks give rise to technical issues in respect of which TQ Delta have been taken by surprise and have not had the opportunity to put in evidence to deal with them.
158. Mr Speck submitted that this was so in respect of each of the alternative cases now advanced by ZyXEL, for the following reasons.
i) They were not foreshadowed in any of the three reports of Dr Jacobsen. They were first advanced during cross-examination, or in certain instances during re-examination.
ii) They each raised technical issues. Had they been set out earlier, they would have been dealt with from a technical perspective in the reports of Dr Ginis, or at the very least, they would have been discussed in detail before the trial and are likely to have been the subject of evidence from Dr Ginis.
iii) They were in substance unpleaded anticipation attacks (and had been expressly advanced on that basis).
iv) The arguments based upon FEC frame level were not part of Alabama’s proposal at all. Rather, they relied upon aspects of the pre-existing system, contained in the ADSL1 standard as Dr Ginis pointed out during his cross-examination. This was common general knowledge at the priority date. However ZyXEL had disclaimed reliance on any case based on common general knowledge alone.
159. I agree with Mr Speck that it would not be fair to allow these alternative cases to be advanced during closing speeches for the reasons that he gave. There is no suggestion that these alternative cases were deliberately held back by ZyXEL. Rather, Mr Speck draws the reasonable inference that counsel for ZyXEL appreciated the difficulties with the case set out in Dr Jacobsen’s evidence, and therefore came up with alternatives.
160. Whilst I recognise the importance of not being too formalistic, and that there are some cases where cross-examination reveals facts that could not have been anticipated in advance of the trial, this is not such a case. It is also important that, in commercially significant cases such as the present, where experts have served a number of reports, each party is at least broadly aware of the case that it has to meet in advance of the trial. There is also a practical difficulty with the new obviousness cases. Dr Jacobsen’s evidence does not address them and insofar as they were put to him in cross-examination, Dr Ginis did not accept them. However, in case it is subsequently decided that I am wrong about this, I shall deal briefly with each of the alternative cases.
FEC frame level (Reference point B) part 1
161. This case was based on the premise that “frames” in Claim 1 of the 268 Patent should be interpreted as including FEC frames. ZyXEL contended that:
i) In Alabama, FEC overhead can be turned off, in which case its FEC frames will not contain FEC bytes. Similarly, interleaving is optional and can also be disregarded.
ii) In the case where MDFs are created at 1 kHz and FEC frames at the ordinary rate of 4 kHz, the contents of 1 MDF will be split into 4 FEC frames. The only difference between the appearance of the bits is that scrambling has taken place, but according to ZyXEL, this does not affect the position of the bits and can be disregarded for purposes of the patent.
iii) In such a case, ZyXEL contended that only every fourth FEC frame will contain a fast byte.
162. As I understood this argument, in contrast to Dr Jacobsen’s evidence, it pins its colours firmly to FEC frames. As to the identification of a parameter within the meaning of Claim 1, insofar as this is identified at all, it relies upon M rather than S B.
163. For the reasons set out in detail above, I reject this case. I have interpreted the word “frames” in Claim 1 as meaning “mux data frames”. It does not include FEC frames. Furthermore, I do not accept that it is possible to ignore the effect of scrambling, even if interleaving is not used. Prior to scrambling overhead bits are clearly identifiable in an MDF. After scrambling, the overhead bits are no longer in that location. Finally, I do not accept that M is a parameter which specifies which frames contain overhead bits and which do not.
FEC frame level (Reference point B) part 2
164. This alternative case relies upon the FEC bytes (when used) in Alabama. ZyXEL submitted that they must count as overhead in the FEC frames, because they are not scrambled, and they are inserted at what TQ Delta regards as the ‘right sub-layer’.
165. ZyXEL submitted that since Alabama provides a parameter for selecting whether or not the FEC bytes are inserted into the FEC frames (R i ), the selection of that parameter specifies which FEC frames contain FEC overhead and which do not. The parameter affects (i) whether there are FEC bytes at all – is R i =0 or R i > 0?; (ii) which frames they fall in – if R i is 4, they straddle frames 14-15 etc., if 16 they straddle more frames, etc. – see the bottom diagram on p4 of Alabama.
166. I do not accept an obviousness attack on this basis, for the following reasons. First, it depends upon an interpretation of “frames” in Claim 1 which I have rejected. Secondly it ignores scrambling. Thirdly, it does not identify a “parameter” within the meaning of Claim 1. The argument merely asserts that R i “affects” whether there are FEC bytes and which frames they fall into.
MDF level (reference point A) part 1
167. For the purposes of this case, ZyXEL repeated the contention that a ‘frame’ at the priority date was a term of art meaning a group of bytes extending over the time of a single data symbol, i.e. 250 microseconds, or repeating at a rate of 4kHz. This applied to data frames assembled at reference point A (referred to in T1.413 and G.992.1 as ‘mux data frames’) as much as to any other frames. In Alabama the number of bytes in a data symbol time period is stated as N i and therefore a frame within the meaning of the Patent is a sequence of N i bytes, whether at reference point A or reference point B. In the Alabama example shown in the diagrams above, therefore, a ‘frame’ is 3 bytes long. The sync bytes are not inserted in every ‘frame’ but rather in some of the frames, as determined by parameter M in conjunction with the table (as shown by Dr Jacobsen in Table B).
168. ZyXEL contended that the 12 byte long groups referred to by Alabama as ‘mux data frames’ are actually just collocations of M (=4) frames within the meaning of the Patent because they extend over M (=4) data symbol time periods. Only the first begins with a sync byte.
169. ZyXEL submitted that the issue is merely one of nomenclature. If the authors of Alabama had been told that they could not change the definition of a ‘mux data frame’ in terms of time, but that they could change the definition in terms of including a sync byte, they would have described their invention as keeping the MDF rate at 4kHz and inserting sync bytes only every M frames. The same system could be constructed from instructions phrased in either of these equivalent ways.
170. I do not accept this case for the following reasons. First, I have rejected the case that “frame” was a term of art with a special meaning at the priority date. Secondly, I have decided that Alabama’s proposal is that the MDFs all contain overhead at the beginning of the frame. Alabama does not teach that some MDFs will and some will not contain that overhead. Rather, it “stretches” the MDFs so that there is a higher ratio of payload to overhead in a given MDF, and optionally increases the number of overhead bytes in the MDF. This is not merely a matter of nomenclature. Thirdly, insofar as the argument relies upon Dr Jacobsen’s Table B, I have concluded that I should not rely upon that table.
MDF level (reference point A) part 2
171. ZyXEL submitted that, even if TQ Delta was correct in its interpretation of “frames” (which I have accepted) then it was not disputed that Alabama disclosed 1kHz MDFs. It then submitted that the table on page 5 of Alabama indicated that only 16 out of the 17 MDFs comprising the superframe included a sync byte. Sync byte 16 was “not used”.
172. In particular, Mr Purvis pointed out that the allocation of overhead bytes in Alabama is determined by parameter M together with a table, such as the one at the top of p5 which is used for M=4.

173. The overhead bytes comprise (as usual) 1 CRC byte, 3 indicator bytes, and a number of EOC and AOC message bytes. In this case, there are 12 of them, giving a total of 16. Where M=4, as can be seen from the table, and S B =8 (thus limiting the number of sync bytes to 1 per ‘mux data frame’), sync bytes are being inserted in pairs, one per 1kHz MDFs. There are 17 1kHz MDFs. Under this combination of M and S B , Alabama inserts 16 sync bytes in the first 16 MDFs (frames 0-15), but none in the 17 th MDF (frame 16).
174. Mr Purvis submitted that the combination of M and the table does in fact satisfy the requirements of the claim even if the only qualifying frames in Alabama are the 1kHz ‘mux data frames’. They determine which frames in the sequence of frames contain overhead bits (in the example frames 0-15) and which do not (in the example frame 16).
175. A real difficulty with this case is that, not only was it not foreshadowed in Dr Jacobsen’s evidence, but also, it was not put to Dr Ginis during his cross-examination. Therefore, he was given no opportunity to comment on it. Mr Speck suggested to Dr Jacobsen during cross-examination (T3/383/25 – 384/4), that the explanation for frame 16 was that Alabama was inserting the EOC and AOC bytes in pairs, and this configuration gives an odd number of 1kHz MDFs in which to put them. The first time that an invalidity case based on frame 16 was advanced was during the re-examination of Dr Jacobsen at T4/516-519. At that stage, Dr Ginis had finished his evidence.
176. The purpose of re-examination is generally to correct or clarify answers. It is not to advance for the first time a wholly new case. Even if I had concluded that ZyXEL were entitled to rely upon certain of their alternative cases, I would not have allowed this fourth case to be advanced.
177. Turning to the substance of the allegation, I do not accept it. The difficulty arises from the absence of technical evidence on this issue. The statement that sync byte 16 is “not used” is unclear. It may be that sync byte 16 contains dummy bits, as was the case with the prior art, and therefore suffers from the problem that the patent seeks to address. Furthermore, it is unclear what is relied upon by ZyXEL as the relevant parameter. The table provides an example using two parameters which are not, or may not be, used to specify which frames contain overhead bits and which do not.
Conclusion
178. For the reasons set out above, I reject ZyXEL’s case that the claims of the 268 Patent were obvious at the priority date in the light of Alabama. The 268 Patent is valid.
Conditional amendment
179. The application to amend was only advanced in the event that I concluded that the claims of the 286 Patent as granted were invalid. In the light of my conclusion, this issue does not arise. Since I was addressed on it (albeit briefly) I record that the conditional amendment would have replaced the words “overhead bits” in the claims with the words “fast or sync bytes”. This could have been relevant if I had concluded that “frames” in the claims were not limited to MDFs.
180. During closings, ZyXEL relied upon three objections to the amendment, namely lack of clarity, adding subject matter by intermediate generalisation and broadening the scope of protection. Mr Speck responded to these objections orally and summarised his points in a written note submitted after the hearing. For the reasons set out by Mr Speck, I was not convinced by any of ZyXEL’s arguments. Had it been necessary to determine the issue, I would have allowed the amendment, the effect of which would, in my view, have removed any argument that “frames” meant anything other than mux data frames.
Infringement
181. The parties agreed that infringement of the 268 Patent depends on whether the patent is essential to the operation of the relevant standards. By the conclusion of the trial, two points remained in issue.
182. First, in relation to ADSL2/2+ ZyXEL argued that if n max was a limiting feature of the claims, then it required “truncation” as disclosed in the specific embodiment. In that case, it was said that the 268 Patent was not essential, in that ADSL 2/2+ does not truncate. Since I have decided that n max is not a limiting feature and is not limited to truncation, I reject this argument.
183. Secondly, in relation to the VDSL2 standard, ZyXEL pointed out that two parameters are used, G p and T p . T p sets the number of MDFs in a sequence (called the OH subframe), which can be 1 to 64. G p sets the number of OH octets in the sequence (i.e. the OH subframe), between 1 and 32. The system then allocates G p OH octets to the sequence of T p MDFs according to certain equations set out at [214] of Dr Ginis’ First Report.
184. If G p is set to be less than T p an overhead byte will be placed in each of the initial G p MDFs but not in the remaining MDFs. Dr Ginis depicts this at [216] of his first report as follows in the example where T p is 8 and G p is 4:
185. ZyXEL accepts that where G p < T p (i.e. there are more MDFs than OH octets to be inserted) they ‘fill up’, one per MDF, from the start of the MDF sequence. As can be seen from the diagram, where G p < T p , G p specifies which frames contain OH octets (overhead bits) and which do not. However, they point out that Dr Ginis acknowledged at [217], “ if G p is larger than or equal to T p , all MDFs in the OH subframe will contain at least one OH octet ” . They submit that this shows that the real allocation scheme is nothing like the n max system taught in the specific embodiment of the 268 Patent.
186. ZyXEL denied that this was a case of ‘infringement some of the time’; the claim is to the operation of a system based on n max , and the alleged infringement is a system operating quite differently. Finding a ‘snapshot’ of the system operation that allows a diagram to be drawn that ‘looks a bit like’ some of the diagrams that can be drawn based on the disclosure of the 268 Patent does not lead to infringement.
187. I do not accept this argument. I am not concerned with whether VDSL2 operates in accordance with the specific embodiment of the 268 Patent. The claim simply requires a parameter that specifies which frames do and which do not contain overhead bits. In VDSL2 Gp fulfills that function where Gp < Tp. That is sufficient to establish i nfringement.
188. In conclusion, the 268 Patent is essential to the operation of the relevant standards. Therefore, ZyXEL have infringed, and are continuing to infringe, the 268 Patent.
JUDGMENT PART B – THE 430 PATENT
189. The 430 Patent concerns cyclic redundancy checksums (“CRCs”), which are used to detect errors in a received bitstream. It has a priority date of 25 September 2004.
Technical background relevant to Patent 430 / common general knowledge at the priority date
CRCs
190. As well as providing technical background, the following information was, in my judgment, common general knowledge at the priority date. CRCs are counted in DSL to identify problems with a DSL line. Such problems, e.g. ‘noise’ on the line, can alter the signal carried over the twisted copper pair such that the received signal is altered in some way. The accuracy of some types of data is more critical than others. A degree of error can be tolerated when streaming video or during voice phone calls, for example. In those circumstances time is of the essence rather than ensuring perfect quality and the video displayed may be of lower resolution or appear ‘blocky’. On the other hand, when downloading a file or some other software it is essential that all of the data downloaded is 100% accurate – delays can be tolerated in order to ensure that all of the data has been accurately received.
191. CRCs are widely used calculations added to data which operate as a check on the accuracy of (or number of errors in) the data that has been transmitted. A CRC is a check value which is a numerical value of a fixed length. It is determined by the transmitter performing a polynomial division in which the block of bits to be transmitted is the numerator and a separate shared polynomial known to both transmitter and receiver is the denominator. The check value transmitted as the CRC is the remainder from the division that has been carried out.
192. A CRC value is calculated by the transmitting party by applying the polynomial division described above to the data bits of an MDF. The CRC value (8 bits long) is then sent in the first octet of the next frame on the overhead channel. Having received the data bits, the recipient does its own calculation of what the CRC value should be and compares this to the actual CRC value received from the transmitting party on the overhead channel. Any discrepancy indicates an error in the bitstream (due to external interference, noise etc.) and this is logged as an ‘anomaly’.
193. CRCs were and are commonly used for detecting bursts of errors in a transmitted bit stream. The CRC failure rate is one of a number of different pieces of line diagnostic information that can be used by operators of DSL networks to identify problems with their networks. The network provider will use the CRC anomalies to diagnose and detect problems in line performance. A certain proportion of errors is acceptable, but the network needs to know when too many are being generated for comfort. It is against this background that certain Recommendations, approved in 1999, required the recording of each Severely Errored Second (“SES”) on a counter.
194. When SES was introduced for use with ADSL1, the number of measurements was fixed – the CRC had to be computed every 17ms, that is to say there would be around 59 computations per second. G.997.1 defines a SES as, among other things, “a count of 1-second intervals with 18 or more CRC-8 anomalies”.
195. As technology developed, however, the period of CRC computation became variable. An account of the changes introduced by various Recommendations is provided in the 430 Patent, and in particular changes between ADSL1 and ADSL2. The extent to which the problem that this created would have been known to the skilled addressee requires an assessment of disputed areas of common general knowledge, and consideration of the identity and attributes of the skilled addressee. I shall consider the disclosure of the 430 Patent before resolving these disputed issues.
The 430 Patent
196. Paragraph [0001] of the 430 Patent states that the invention relates generally to communication systems. More particularly it is said that “an exemplary embodiment of this invention relates to anomaly detection and communication systems”. Although described as an exemplary embodiment, this defines the field of the invention. Paragraph [0002] introduces CRC error detection which I have considered as part of the technical background.
197. Paragraph [0004] explains the concept of SES and that in the ADSL2 Recommendation an SES is defined as 18 or more CRC anomalies in a 1-second interval. The 430 Patent states that:
“This corresponds to approximately 30 per cent of computed CRCs being in error if the CRC is computed every 17 ms. The G.992.3 ADSL standard requires that the CRC is computed every 15 to 20 msecs. In ADSL 2 and ADSL 2 systems, the period of the CRC computation is called the period of the overhead channel (PERp). The G.992.3 standard requires that
15 ms <= PERp <= 20 ms.”
198. Paragraph [0005] explains that DSL service providers use CRC anomaly reporting as a way to diagnose and detect problematic service conditions. It states that an ADSL service provider may use SESs as a way to detect an ADSL connection that is experiencing problems. For example, an ADSL service provider may specify that if an ADSL subscriber is experiencing more than 30 SESs in a 1-minute period, the ADSL connection needs to be repaired. For this reason, it is important that an SES is reported in a consistent manner across all connections in the service provider network.
199. Paragraph [0006] explains that if CRCs are computed every 2ms, rather than every 17ms (the CRC calculation period in ADSL1), then 18 CRC anomalies in a 1-second period would represent 3.6% of CRCs in that second being in error rather than approximately 30%, being the PERp required by the G.992.3 standard. In those circumstances, the service provider might dispatch a network technician to fix a connection that is only experiencing a small number of errors.
200. Paragraph [0007] explains that most communications systems restrict CRC computation to within a “specified and bounded repetition period or rate” in order to provide consistent detection and diagnostic capabilities. Paragraph [0008] explains that new designs and innovations were making it more difficult to ensure CRC computations were bounded. It gives the examples in ADSL2 of Seamless Rate Adaptation (“SRA”) and Dynamic Rate Repartition (“DRR”) that allow ADSL2 to make seamless changes in data rates on-line. SRA and DRR modify the data rate without changing the framing parameters, in a way that changes the PERp in proportion to the data rate change.
201. Paragraph [0009] reiterates that in ADSL2 PERp must be 15–20ms and says that this range is a problem because SRA and DRR are limited to “small data rate changes, usually within 10 to 15 percent”. Paragraph [0010] states that it would often be desirable to have large data rate changes resulting in PERp values outside the range of 10–20ms but that ADSL service providers will encounter problems with diagnostic procedures which are based on CRC anomalies to detect problematic connections.
202. Paragraph [0011] discloses that new communication systems such as VDSL, VDSL2 and other high-speed wired and wireless communication systems specify very wide ranges of data rates, such as 500 Kbps to 100 Mbps or more. It states that it is difficult to design a framing method for all possible data rates that include a CRC procedure that restricts the CRC computation period to be within a specified and bounded repetition period.
203. Paragraphs [0012] and [0013] explain that the accuracy of CRC error detection decreases with the number of bits in the CRC computation period. For example, a 20ms computation period would cover 20,000 bits at 1 Mbps and 20 million bits at 100 Mbps; error detection is generally considered adequate if the computation period includes less than 100,000 bits.
204. Paragraph [0014] of the 430 Patent states that the:
“Object (sic) of this invention relates to calculating and reporting communication errors and, more particularly, to a method or a module for calculating or reporting CRC anomalies in a consistent manner for all communication connections in a network independent of data rate or the CRC computation period (e.g. the PERp value) of each individual connection.”
205. The 430 Patent proposes to normalise the number of CRC anomalies to take account of the CRC computation period being used on that line i.e. to increase the CRC anomaly count in proportion to the periodicity of the computation. Normalising is also referred to as in the 430 Patent as scaling – see [0053] and [0054]. Whilst the preferred embodiments are quite complex, the basic idea is straightforward and is illustrated in Figure 2, which is described at [0022] as “a flowchart outlining an exemplary method for normalizing a CRC counter according to this invention”.

206. The patent describes an exemplary embodiment at paragraphs [0032] – [0040]. Paragraph [0035] explains that each CRC anomaly is counted as PERp /K normalised anomalies and that K is any positive integer. It explains that generally K will correspond to a value equal to an expected period of CRC computations based on which the system diagnostic information is reported. For example, for ADSL and VDSL systems, K can be equal to 15ms (i.e. the bottom of the range in ADSL2), corresponding to approximately 66 CRC computations per second. It reiterates that a Severely Errored Second is reported when there are more than 18 CRC anomalies in a second, which corresponds to 30% of the CRC computations being in error.
207. Paragraph [0036] illustrates the operation of the invention. Since CRC anomalies are typically reported as integer numbers, the accumulated CRC anomaly count can be rounded up to the next higher integer. For example, if PERp=28, then each CRC anomaly is counted as 28/20=1.4 normalised CRC anomalies. If there are 23 CRC anomalies detected over a period of time, the accumulated CRC anomaly counter could contain ceiling (23 x 1.4) = ceiling (32.2) = 33 normalised CRC anomalies, where “ceiling” indicates a rounding in the upward direction. [0039] explains that the CRC error counter is incremented by this value, referred to as "M", equal to PERp /K.
208. Paragraph [0040] teaches how communication parameters (such as data rate) can be monitored to determine changes in PERp. Paragraphs [0041] – [0053] describe a second exemplary embodiment in which CRC computations are combined into groups of “ceiling(K/ PERp)”. Paragraphs [0049] – [0054] teach the use of different normalization methods depending on PERp and involving different grouping and scaling calculations for each instance. These paragraphs also teach the use of K being an integer such as 15, 17 or 20 in relation to each method. Paragraph [0045] discloses that the CRC computations could also be combined in groups based on some metric other than ceiling (K/ PERp). For example, floor (K/PERp) could be used i.e. rounding down rather than rounding up.
209. As illustrated by the Figures, the receiver computes a local CRC value and compares it to the CRC value received from the transmitter. If the two CRC values do not match, the receiver identifies a CRC anomaly. The receiver then increments the CRC error counter by a value of M equals PERp/K where K is a positive integer. At the end of a one second period, the accumulated CRC anomaly count can be rounded up to the next highest integer. Therefore, the patent contemplates a normalising step which requires incrementing the counter by the value of PERp/K.
Claims in issue
210. Claim 1 concerns a method for normalising a CRC anomaly counter. A CRC anomaly is identified where the CRC byte does not match that generated by the receiver (integer 2 below). Claim 1 may be divided into the following integers:
“[1] Method for Cyclic Redundancy Checksum, hereinafter referred to as CRC, anomaly counter normalization comprising:”
[2] identifying a CRC anomaly when a local CRC octet, which is computed based on a received bit stream, is not identical to a received CRC octet.
[3] normalising the CRC anomaly counter based on a value for a CRC computation period, hereinafter referred to as PERp
[4] wherein the normalising of the CRC anomaly counter comprises incrementing the CRC anomaly counter by a value of M wherein the value of M is equal to PERp/K, where K is a positive integer.
211. Claim 10 is to a module using the method of Claim 1. It is said to be independently valid but adds nothing to Claim 1.
Issues in dispute in relation to the 430 Patent
212. The disputed issues in relation to the 430 Patent are:
i) Interpretation of “normalising” in Claim 1;
ii) Infringement, which depends on the interpretation of normalising.
iii) The identity and attributes of the skilled person;
iv) Common general knowledge of the changes in respect of the CRC computation period introduced by changes in the standards
v) Obviousness in the light of the cited prior art (ADSL2/02)
Interpretation of “normalising” in Claim 1
213. ZyXEL submitted that “normalising” is required by the claims of the 430 Patent to be performed consistently across all computation periods/PERp. They argued that the claims must be read in the light of the object of the invention stated in paragraph [0014]. Paragraph [0015] specifically states that the object is achieved by a method according to Claim 1 or a module according to Claim 10. Hence, methods which do not achieve the object cannot be considered to be intended to be within the scope of the claims.
214. The object in [0014] is a method or module for calculating and reporting CRC anomalies “in a consistent manner for all communications connections in a network independent of data rate or the CRC computation period (e.g. the PERp value) of each individual connection”. Mr Purvis submitted that this is achieved in all the relevant exemplary embodiments of the invention by ensuring that every time it identifies an anomaly the anomaly counter is incremented by PERp/K. Therefore, the object of the invention is only achieved if one reads the term ‘normalisation’ in the claim as requiring the counter to respond consistently to all identified anomalies so that they are indeed reported in a consistent manner independent of the CRC computation period (PERp).
215. I do not accept this argument. In my judgment, “normalising” does not require calculation and reporting of CRC anomalies in a consistent manner for all connections. There is no such limitation in the language of Claim 1, and consideration of the description and drawings does not support this interpretation.
216. In particular, paragraph [0042] of the 430 Patent gives the following example of the invention:
“[0042] K=15 ms and PERp=10 ms: CRC computations are combined in groups of ceiling(15/10)=2 CRC computations. The first 2 CRC computations are the first group, the second 2 CRC computations are the second group, and so on. One or more CRC anomalies in a group are counted as 1 normalised CRC anomaly.”
217. Dr Jacobsen agreed in cross examination that this was normalizing to the top of the 15 -20ms window; T4/507/18 -21. She also accepted that the benefit of normalisation was obtained even outside that window; T4/510/15-19:
“Q. So one can see that outside that window, one is getting the
benefit of the normalisation because you have had the effect
of scaling it so as to constrain any variation to be within in this case, 36 to 27, yes?
A. That is right.”
Infringement
218. ZyXEL’s non-infringement case depended on its construction of “normalising”, which I have rejected. If the 430 Patent is valid, then it is infringed, as it is essential to the relevant standards.
The skilled addressee of the 430 Patent
219. Whilst as a matter of generality the skilled addressee of the 430 Patent may be described in the same way as the skilled addressee of the 268 Patent, there was a significant dispute between the parties in relation to his/her capacity to assimilate the prior art, whether she or he would be interested in any particular aspect of the prior art, and whether it is appropriate to consider a skilled person working for an ISP, who is interested in SES reporting and management.
Legal principles
220. Certain legal principles are settled law. They may be summarised as follows:
i) A patent specification is addressed to those likely to have a real and practical interest in the subject matter of the invention (which includes making it as well as putting it into practice) ( per Lord Diplock in Catnic Components v Hill & Smith Ltd [1982] RPC 183 at 242 )
ii) The relevant person or persons must have skill in the art with which the invention described in the patent is concerned. As Aldous LJ stated in Richardson Vicks Inc’s Patent [1997] RPC 888 at 895:
“Each case will depend upon the description in the patent, but there is no basis in law or logic for including within the concept of “a person skilled in the art”, somebody who is not a person directly involved in producing the product described in the patent or in carrying out the process of production.”
iii) The skilled addressee has practical knowledge and experience of the field in which the invention is intended to be applied. She or he reads the specification with the common general knowledge of persons skilled in the relevant art, and reads it knowing that its purpose is to disclose and claim an invention.
iv) A patent may be addressed to a team of people with different skills. Each such addressee is unimaginative and has no inventive capacity.
v) Although the skilled person/team is a hypothetical construct, its composition and mind-set is founded in reality. As Jacob LJ said in Schlumberger [2010] EWCA Civ 819; [2010] RPC 33 at [42]:
“… The combined skills (and mindsets) of real research teams in the art is what matters when one is constructing the notional research team to whom the invention must be obvious if the patent is to be found invalid on this ground.”
Assimilation of complex documents
221. In the present case, the cited prior art is the ADSL2/02 standard. It is a comprehensive document, which is far too long to summarise in this judgment. ADSL2/02 is a complete specification for every standardised aspect of an ADSL2 transceiver. It runs to 312 pages and incorporates thirteen pre-existing Recommendations.
222. TQ Delta submitted that the law requires that the real-life attributes of the skilled addressee are to be taken into account. I agree. It suggested that the approach to the prior art adopted by ZyXEL was to treat the skilled addressee as having exceptional powers of assimilation. It submitted that ZyXEL wrongly assumed that the skilled person can read through massively long and complex documents, retain all of the detail and link the disclosure from one part to all other parts (and the contents of multiple cited documents) to which it may in any way be related, whilst identifying the nature of the links.
223. This, according to TQ Delta, is wrong in principle. It would lead to contributions which are not within the capability of the ordinary skilled person being excluded from patentability. Mr Speck postulated an invention which results from an unusually perceptive reading of a long and complex document requiring a special ability to hold detail in mind throughout the reading, and to correlate or connect detail from disparate parts of it. He suggested that this may be valuable and non-obvious in the sense that ordinary people skilled in the art could not do it.
224. Insofar as this submission suggests that hindsight “cherry-picking” from the prior art is impermissible, then I agree. Insofar as it suggests that the skilled person will not assimilate the contents of long and complex documents which are cited as prior art, and relevant documents which are incorporated by reference in the prior art, then I disagree.
225. The skilled person is deemed to read and assimilate a prior art document properly and with interest. Having done so, she or he may conclude that it is in fact of no interest, or of no relevance to the problem with which she or he is concerned, but that is a different question. This was explained by Laddie J in Inhale v Quadrant 2002 RPC 21 at [47]:
… A fiction in patent law is that the notional uninventive skilled man in the art is deemed to have read and assimilated any piece of prior art pleaded by the party attacking the patent claim . If the invention is obvious to that person in the light of a particular piece of prior art, the claim is invalid. It is no answer to say that in real life the prior art would never have come to the attention of a worker in the field, for example because it was tucked away on the top shelf of a public library or because it was in a language which nobody in the art knew. The notional skilled person is assumed to have read and understood the contents of the prior art. However that does not mean that all prior art will be considered equally interesting. The notional skilled person is assumed to be interested in the field of technology covered by the patent in suit, but he is not assumed to know or suspect in advance of reading it that any particular piece of prior art has the answer to a problem he faces or is relevant to it. He comes to the prior art without any preconceptions and, in particular, without any expectation that it offers him a solution to any problem he has in mind…. (emphasis added).
226. This approach has been applied by the Court of Appeal in a number of cases. For example, in
Asahi Medical Co Ltd v Macopharma (UK) Ltd [2002] EWCA Civ 466 Aldous LJ said at [21]:
“ Of course any prior art document relied on must be deemed to be read properly and in that sense with interest. To conclude otherwise would deprive the public of their right to make anything which is an obvious modification of a published document. By ‘obvious’ it is meant that which would be obvious to the skilled person. The correct approach was set out by Oliver LJ in the Windsurfing case. He said at page 74 line 20:
“We agree, of course, that one must not assume that the skilled man, casting his experienced eye over Darby [the prior art], would at once be fired with the knowledge that here was something which had a great commercial future which he must bend every effort to develop and improve, but he must at least be assumed to appreciate and understand the free-save concept taught by Darby and to consider, in the light of his knowledge and experience, whether it would work and how it will work”.”
227. As stated above, ADSL2/02 is a very long document, which is concerned with the entire implementation of ADSL2. However, the 430 Patent is not concerned with the entire implementation of ADSL2. It is concerned with the limited issue of error reporting and management. This was a known field at the priority date. A patent specification is addressed to those likely to have a real and practical interest in the subject matter of the invention, and the relevant person or persons must have skill in the art with which the invention described in the patent is concerned.
228. I accept ZyXEL’s submission that the skilled person to whom the Patent is addressed is interested in error reporting and management. That skilled person would be specifically interested in the impact of ADSL2 on error reporting and management, as that is the field in which the 430 Patent claims to have made an improvement.
Internet service providers
229. I have considered the evidence of Dr Ginis at [232] of his first report, where he said that in 2004, there was no specialisation within communication systems engineering for DSL line diagnostics. However, I accept ZyXEL’s submission that it is appropriate to consider a person working for an ISP as a part of the skilled team. I reach this conclusion for the following reasons.
230. “Digital subscriber line service providers” (ISPs) are expressly referred to in the 430 Patent at [0005] – [0006]. ISPs had to report SESs, and were using the equipment that identified them. ISPs experienced the consequences when a network technician was sent to fix a connection that was only experiencing a small number of errors :
“[0005] Digital subscriber line service providers use CRC anomaly reporting as a way to diagnose and detect problematic service conditions. For example, an ADSL service provider may use SESs as a way to detect an ADSL connection that is experiencing problems. For example, an ADSL service provider may specify that if an ADSL subscriber is experiencing more than 30 SESs in a 1 -minute period, the ADSL connection needs to be repaired. For this reason, it is important that an SES is reported in a consistent manner across all connections in the service provider network.
[0006] As discussed above, if an ADSL system is determining CRCs every 17 ms (the PERp as required by the standard), Severely Errored Seconds (SESs) are defined as 18 or more CRC anomalies in a 1-second interval, then an SES will occur whenever approximately 30 percent of the computed CRCs are in error in a 1-second interval. But if, for example, CRCs are computed every 2 ms, and a SES is still defined as 18 or more CRC anomalies in a 1-second 40 interval, then 18 CRC anomalies will correspond to only 3.6 percent of a computed CRC being in error. In this case, the service provider may receive a repair alarm and dispatch a network technician to fix a connection that is only experiencing a small number of errors”.
231. The expert evidence explained and supported this disclosure. ISPs were concerned with the reporting of SES’s on lines which was compulsory under ADSL2/02. This was an important aspect of error reporting and management. and when cross-examined about the standard, Dr Ginis accepted that any skilled person involved in error management, such as an ISP, would pay particular attention to those parts of the standard that were mandatory (T1/109/6-12):
“Q. Anything that is required, so it is given a capital letter "R", for example, and is thus mandatory, is something that any skilled person who was involved in error management, for example, in operating an ISP at the priority date, would need to be very familiar with?
A. It would be a reasonable assumption for the kind of person you describe to pay particular attention to those parts.”
232. The point of requiring this information to be compulsorily reported on individual lines was to enable network operators to monitor their lines and take steps based on it (see Ginis T1/121 lines 2 – 6). By the priority date this was being done using SES data by ISPs. Individual SESs would not be relied upon, but the software would monitor over a particular period of time and flag up an issue on the line if an unacceptable pattern of SESs was experienced.
Common general knowledge –CRCs and SESs
233. The measurement of SES was common general knowledge at the priority date. SES reports had been an important part of the error reporting requirements under the ADSL Standards since the publication of the first ITU-T ADSL1 Standard (G.992.1) in June 1999. This Standard was published simultaneously with G.997.1 which set out the management functions to be carried out by transceivers, including the error monitoring requirements. G.992.1 incorporated by reference G.997.1 for ‘Failures, performance parameters, storage and reporting thereof’ . As a result, Dr Jacobsen considered G.997.1 represented the common general knowledge (indeed the basic required information) for any skilled person concerned with the management functions of transceivers in networks. Jacobsen 1 [244]; Dr Ginis agreed at T1/98/10-14:
“for someone that intends to study and understand, implement, G.992.1 transceivers and, more precisely, wanting to understand the management functions of such transceivers, the G.997.1 document would indeed provide the detailed specification.”
234. Furthermore, Dr Ginis explained at [246] of his first report, in a section which set out common general knowledge at the priority date of the 430 Patent, that CRC was commonly used to derive line performance measurements, including "code violations", "errored seconds" and "severely errored seconds". He said that these were well known to the skilled person from decades of use in various communications systems.
235. The experts agreed that it was well known to the skilled person that CRCs were not error-proof: there is a small probability that the CRC computed by the receiver is identical to the CRC byte received despite errors in data reception. It was also well known that the CRC method detects that there is at least a one byte error over a block of bytes and cannot indicate the number or the location of the byte error(s) within this block.
236. G.997.1 defined a threshold of 18 CRC anomalies within a one-second period for declaring an SES. The experts agreed that this threshold was somewhat arbitrary and did not derive from some type of strict quality of service requirement. It was well known that SES counters (like CRCs themselves) were only approximate indicators of line issues. With a threshold of 18, an SES may correspond to as few as 18 bytes in error or as many as 1,000,000 bytes in error. In addition, because SES were counted second-by-second, the same number of CRC anomalies might or might not produce an SES depending on how many fell within the same second. For example, a burst of 20 CRC anomalies would trigger the occurrence of an SES only if 18 or more happened to fall within the same one-second period:
| |
| |  |
237. The impact on user experience from an SES was also uncertain. If the bytes in error were simply dummy bytes conveying no information (e.g. if the DSL was idle), then there would be no impact on user experience. If the bytes in error corresponded to a voice application with a high tolerance for lost packets, then the impact on user experience would be minor. If the bytes in error corresponded to a critical video frame of a live-streamed sports event, then the impact on user experience could be significant.
238. SES anomalies were therefore well known as an approximate measurement that could be used for line diagnostics. They were part of the toolkit of measurements the skilled person could use (or not – for example, not all DSLAM equipment at this time supported the collection of SESs).
239. Despite the inaccuracies inherent in the definitions of CV and SES counters, these counters were informative. For example, an SES counter value corresponding to a single 15-minute period showing 30 SESs may have been an unreliable indicator of a line issue. However, an observation that all 15-minute SES counters corresponding to times between 6pm and 10pm exceeded a count of 30 for each of the last 3 days might have been a reasonably reliable indicator that the user had been having a poor internet experience.
CRC anomalies expressed as a percentage
240. There was a dispute about whether the skilled person at the priority date would have worked out the CRC anomalies as a percentage. Whilst ZyXEL submitted that it was not essential to their case to establish this, the issue requires determination. During her cross-examination, Dr Jacobsen explained her view as follows at T4/454 lines 4-12:
“The logic that I applied, that I believe the skilled person applied would be first to see that number 18 and think, “Why 18” (because any time you see a constant, I think the skilled person wonders where the constant came from) and then, would look at ADSL and realise, based on the structure of the overhead channel and the fact that the CRC has transmitted once every 17 ms, then would work out “okay that is about 30%. I understand that is the traditional level to declare a severely errored second.”
241. I accept Dr Jacobsen’s evidence on this issue. Alternatively, even if the percentage (in fact 30.5%) was not common general knowledge, I believe that it was an obvious value to work out, for the reasons given by Dr Jacobsen.
Perception of the problem – legal principles
242. In Actavis v Novartis [2010] FSR 18, Jacob LJ made some criticisms of the problem/solution approach (“the PSA”) used by the EPO. At [35] he considered that an invention could lie in the perception of a problem:
“35. Moreover the PSA does not really cope well with cases where the invention involves perceiving that there is a problem, or in appreciating that a known problem, perhaps “put up with” for years, can be solved. Take for instance the “Anywayup Cup” case, Haberman v Jackel International [1999] FSR 683 . The invention was a baby's drinker cup fitted with a known kind of valve to prevent it leaking. Babies drinker cups had been known for years. Parents all over the world had put up with the fact that if they were dropped they leaked. No-one had thought to solve the problem. So when the patentee had the technically trivial idea of putting in a valve, there was an immediate success. The invention was held non-obvious, a conclusion with which most parents would agree. Yet fitting reasoning to uphold the patent into a PSA approach would not really work. For by identifying the problem as leakage and suggesting it can be solved, one is halfway to the answer – put in a valve.”
243. Haberman v Jackel was not a case where inventiveness lay in perceiving the existence of a problem. Rather it was a case in the second category discussed by Jacob LJ, where a problem had been known for a long time before the priority date, but had not been solved. As is evident from the judgment of Laddie J at [33] onwards, it was a case of long felt want and commercial success. Counsel were unable to point to any case where a patent whose solution was obvious was nonetheless held to be inventive on the basis of perception of the problem.
244. Nonetheless, I recognise that such a case is possible. The EPO has recognised that the identification of a technical problem could give rise to an invention, although it has emphasised that such identification will rarely amount to an inventive step. The principles are summarised in the following passages from Case Law of the Boards of Appeal , at I.D.9.10.
The posing of a new problem did not represent a contribution to the inventive merits of the solution if it could have been posed by the average person skilled in the art (T 109/82, OJ 1984, 473). It also had to be taken into consideration that it was the normal task of the skilled person to be constantly occupied with the elimination of deficiencies, the overcoming of drawbacks and the achievement of improvements of known devices and/or products (see T 15/81, OJ 1982, 2; T 195/84, OJ 1986, 121). In T 532/88 the board confirmed the established principle that to address a problem simply by looking for ways of overcoming difficulties arising in the course of routine work did not constitute inventiveness.
[…]
In T 971/92 the board emphasised that the appreciation of conventional technical problems which formed the basis of the normal activities of the notional person skilled in the art, such as the removal of shortcomings, the optimisation of parameters or the saving of energy or time, could not involve an inventive step. The appreciation of a technical problem could thus only contribute to the inventive step in very exceptional circumstances.
245. I would not use the expression “very exceptional circumstances”. Each case depends on its own facts. However, I agree with the logic of the Board of Appeal in the case law referred to above. In a field where the person skilled in the art regularly confronts technical problems and is used to solving them, if a real problem exists, she or he is likely to be aware of it.
Obviousness in the light of ADSL2/02
246. As indicated in the introduction to this judgment, this is an unusual case, in that TQ Delta accepts that once the problem addressed by the patent is known, the claimed solution was one of a number of obvious solutions. However, it contended that invention lay in perceiving the problem at the priority date.
247. The 430 Patent claims a method or a module for normalising the anomaly counter to take account of variations in PERp between lines, namely:
Normalising the CRC anomaly counter based on a value for a CRC computation period, hereinafter referred to as PERp, wherein the normalising of the CRC anomaly counter comprises incrementing the CRC anomaly counter by a value of M wherein the value M is equal to PERp/K, where K is a positive integer.
248. It was common ground between the experts that there is nothing inventive in the normalisation mechanism itself. Dr Jacobsen explained that once the discrepancy between lines was identified, it would have been obvious to the skilled person to achieve consistency by at least three different methods, one of which was the normalisation of the counter by multiplying by a factor dependent on PERp (Jacobsen 1 [403]). Dr Ginis accepted this in his Second Report at [81] and confirmed this during his cross examination at T2/156/22 to 157/2.
TQ Delta’s submissions in outline
249. TQ Delta submitted that, at the priority date, the skilled person would not “spot the issue addressed by the patent”. They criticised Dr. Jacobsen’s approach to the ADSL2/02, which was alleged to be vitiated by a combination of the following errors:
i) She was instructed to approach the prior art with a focus on how a skilled person would suggest to improve CRC reporting. As a matter of fact she approached her task even more narrowly – only considering Severely Errored Seconds.
ii) She assumed a superhuman ability of the skilled person to wade through a long and complex standard, assimilating the detail and piecing together consequences. Not only did the skilled person assimilate the material but he or she was also equipped to cherry-pick points from different places in the standardisation landscape. There are 13 cross-referenced documents in the ADSL2 prior art standard. The addressee knew what to consider and what to ignore, apparently questioned each and every constant they saw in the standards, and identified all current and potential problems including a problem with Severely Errored Seconds.
iii) The approach was riddled with hindsight and speculation: a classic step-by-step approach, ignoring many matters, focusing on others.
250. In addition, TQ Delta seek to rely upon events subsequent to publication of ADSL2/02. The industry was all focussed on the prior art. Mr Speck argued that nonetheless “the problem lay buried and unsolved”. He said that this was a field in which a substantial number of highly skilled and innovative individuals all focussed on routing out problems and proposing solutions. ADSL2+ was published in 2003. A new issue of the G.ploam standard was published in the same year – and it was also amended later that year. And yet, according to TQ Delta, nothing was done. Mr Speck asked why that was, if it was obvious for a skilled person to identify the problem to which there are several obvious solutions. The answer that he suggested was that it was not obvious in the light of the art relied upon – art that was being actively studied and worked upon by those in the industry at the time.
ZyXEL’s submissions in outline
251. ZyXEL relied on the fact that it was common ground that the allegedly inventive solution of the 430 Patent was acknowledged to be obvious, once the problem was known. It contended that, insofar as there was a real problem at the priority date, it required no invention to perceive it. On the contrary, it would have been evident to the skilled person from consideration of ADSL2/02, when read in the light of common general knowledge. Finally, ZyXEL argued that, insofar as relevant, events subsequent to publication of ADSL2/02 refuted any suggestion of an unresolved, longstanding problem.
Discussion
252. For the reasons set out below, I accept ZyXEL’s submissions on this issue, and have reached the conclusion that the 430 Patent was obvious in the light of ADSL2/02.
Focus on CRCs/SESs
253. In the light of my conclusion that the skilled team includes an ISP, I consider that Dr Jacobsen was correct to focus on CRCs, and in particular SESs, when considering the prior art. The experts agreed that when monitoring information coming in from thousands of lines, it was important to ensure that the information being received was being reported in a consistent way across the network: Jacobsen 2 at [82]; Ginis XX 1/131/lines 11-24:
Q. Okay. Let me put something else to you. If you were considering an automated system of the kind we have been discussing, that you mention in paragraph 253, which you wanted to implement as an ISP to identify problematic lines, you would need to consider, would you not, as a matter of course, whether the information you were relying on, in this case severely errored second counters, was being reported in a consistent way across all the lines on your network?
A. Allow me a few seconds. (Pause) I think it is indeed a desire of the software engineers or the systems engineers who are designing such systems, to rely on consistent parameters. So I would agree that there is the motivation to know, to make sure that quantities such as severely errored seconds, are consistent.
254. Dr Ginis confirmed at T1/141/8-15 that an ISP would be immediately concerned when considering the new ADSL2 standard to look at whether severely error seconds were reported and whether they were available:
“I think that the immediate, let us say, concern of the immediate motivation of an individual that is working for an internet service provider and who is seeing that there is this new standard, ADSL2, which is now coming into the market and possibly equipment needs to be included in the network, would be to look at whether severely errored seconds are reported and whether they are available.”
255. Dr Jacobsen’s approach to ADSL2/02, which focused on those parts of the standard concerned with SESs, was, in my view, justified. I do not accept that the Standards document, cited as prior art, should be approached on the basis that the skilled person reads the entire document through without focusing on the matters which interest him or her.
Superhuman ability/cherry picking
256. I reject the suggestion that superhuman ability is required to identify the problem from the standard, and I do not accept that this required any “cherry picking”. The relevant passages in ADSL2/02, which disclosed the change from a fixed period to a range, were identified by Dr Jacobsen at [28] – [30] of her third report. She also pointed out that G.997.1, which specified the fixed period in ADSL1, was prominently referred to in ADSL2/02, for example at Section 9. Therefore, the change would have been apparent to the skilled person.
257. Dr Ginis’ cross-examination also supported the conclusion that the relevant passages in ADSL2/02 would be apparent to the skilled person. In particular, he explained at T1/145-147 that:
i) The skilled person would note that the CRC octet is in the first octet in the overhead channel, as it was before, so the period of the CRC checks was the period of the overhead channel. This is shown in Table 7-14 on p40 of ADSL2/02. Dr Ginis agreed that this is where the skilled person would expect to find it and that this is what she or he would be looking for;
ii) The skilled person would find the overhead channel period which is explicitly identified in Table 7-7, on p32, as PERp. She or he would immediately see that PERp is variable, but that the scope for variation is fixed by the throttle of 15-20ms in Table 7-8, on p33.
258. At this point , an inconsistency between the standards would have been clear to the skilled person. Under ADSL2/02, the period of the overhead channel (PERp) for any particular line now depended on a number of variables which could be set by the pair of modems but was constrained to a range between 15 and 20ms (Table 7-8 page 33). Therefore, the CRC checks were no longer taking place at the same consistent rate between lines. The result was that depending on the PERp for the particular line, the minimum number of CRC errors needed to generate an SES report could now be anything between 27% (15ms) and 36% (20ms); (Jacobsen 1 paragraphs392-397).
259. I have concluded that SES reporting was part of the common general knowledge at the priority date. It was well understood that it was dependent on the CRC computation period. It was common general knowledge at the priority date that the CRC computation period was fixed in ADSL1. ADSL2/02 changed this to a variable period. It required no invention for the skilled addressee to perceive that this would lead to inconsistency in the significance of SES between different lines. In particular, a person working for an ISP, whose job it was to understand the significance of the information to monitor the performance of lines on the network, would have to understand this.
Step by step approach and hindsight
260. In Mills & Rockley (Electronics) Ltd v Technograph Printed Circuits Ltd [1971] FSR 188 at 193, Lord Diplock observed that once one knows of the invention, it is possible to set out a combination of steps by which the inventor might have arrived at the invention, starting from the prior art. Such steps, in isolation, may not be inventive, such a reconstruction may be unrealistic and may ignore the inventive ingenuity in selecting the particular combination of steps which the inventor perceived would lead to the final result. However, it is also the case that a patentee may identify numerous steps in response to an allegation of obviousness, and those steps may themselves be artificial, or obvious, both alone and in combination.
261. In the present case, Mr Speck did not argue that the step-wise, hindsight, approach had been applied to the alleged invention of the 430 Patent, but to the perception of the problem that the Patent identified. Mr Speck suggested that Dr Jacobsen wrongly focused on SESs when considering ADSL2/02 and thereby ignored other areas in which the skilled team would be more interested. I have already rejected this argument. He further pointed to deficiencies and inaccuracies in SES reporting, which he argued that Dr Jacobsen had ignored. I do not accept this criticism. Although there were inaccuracies inherent in SES reporting, which I have noted, SES was mandatory under ADSL2/02, and was regarded as informative and reasonably reliable in certain circumstances. So any changes in reporting between standards had to be addressed.
Secondary evidence – events subsequent to the publication of ADSL2/02
262. Secondary evidence must be kept firmly in its place, as emphasised by the Court of Appeal in Molnlycke v Procter & Gamble [1994] RPC 49 at 112. It is no more than an aid to assessment of the primary evidence. However, in an appropriate case, secondary evidence may provide a useful cross-check against hindsight. In Schlumberger (supra) Jacob LJ explained the relevance of secondary evidence at [77]:
“ It generally only comes into play when one is considering the question "if it was obvious, why was it not done before?" That question itself can have many answers showing it was nothing to do with the invention, for instance that the prior art said to make the invention obvious was only published shortly before the date of the patent, or that the practical implementation of the patent required other technical developments. But once all other reasons have been discounted and the problem is shown to have been long-standing and solved by the invention, secondary evidence can and often does, play an important role. If a useful development was, in hindsight, seemingly obvious for years and the apparently straightforward technical step from the prior art simply was not taken, then there is likely to have been an invention. ”
263. I am not persuaded in the present case that secondary evidence is of assistance to TQ Delta. I do not accept that events subsequent to the publication of ADSL2/02 demonstrate a longstanding problem which had not previously been perceived.
264. In my judgment, the evidence shows that at the priority date, the discrepancy in SES reporting between lines operating in the 15-20ms PERp range was not regarded as a problem that was sufficiently serious to require further action. This was accepted by Dr Ginis during cross-examination at T2/154-155 and supported by the evidence of Dr Jacobsen at [400] of her first report.
265. The invention in the present case is said to lie in the perception of a problem, and not in its solution. If there was no problem worth solving at the priority date, then I would have concluded that the 430 Patent had made no technical contribution to the art.
266. However, in my judgment, the evidence demonstrated that it was widely known by the priority date that a general increase in the range of PERp was going to be introduced. Dr Jacobsen said at [443] of her first report:
As I explained above when considering developments of ADSL2/02 without knowledge of the ’430 Patent or future developments in ADSL, the normalizing step merely recites one of solutions the skilled person would have recognized, as a matter of routine, for the problem of different receivers declaring SESs for different percentages of CRC checks being in error. The skilled person would have understood this to be a solution within ADSL2/02 to ensure that error reporting was consistent (i.e., SES declared at a 30% CRC error percentage) across all allowed values of PERp. Moreover, as I explained above, the skilled person would have understood the importance of solving this problem for later versions of DSL in which the PERp could be expected to vary even more than between 15 and 20 ms, such as for the higher-bit-rate standards (e.g., VDSL2) already being developed as of the priority date.
267. Dr Ginis commented on that evidence in his second report. He accepted that the skilled person would have been aware in September 2004 that standard-setting was underway for VDSL2 and that it was intended to support higher bit rates than ADSL2. But he did not think that would have altered the skilled person's understanding of ADSL2/02.
268. I accept Dr Jacobsen’s evidence on this issue. Although VDSL had not been published at the priority date, it was commonly known that large data rate changes, outside of the range of 10-20ms were desirable, and that VDSL (and other new communication systems) would specify data rates that would occupy a large range.
269. In summary, I conclude that it was not necessary to normalise the CRC count so long as the CRC period was fixed between 15 and 20ms. It was necessary to do so once the CRC period was widened, which was predictable at the priority date.
270. This analysis does not show any longstanding, unresolved problem. The 15-20ms range existed between 2002 and January 2005. No normalisation was carried out. In January 2005, it was amended in the new version of the G.992.3 Standard. Table 7-8 introduced a possible PERp range from 1.875 to 160ms where online reconfiguration had taken place. Normalisation of the CRC count was introduced simultaneously with this change, but not in relation to the 15-20ms period for which the count remained as before. There was no period of long-felt want.
271. For the reasons set out above, I conclude that the claims of the 430 Patent were obvious at the priority date in the light of ADSL2/02. The 430 Patent is invalid.
Overall conclusions
272. The result of the technical trial is as follows:
i) The 268 Patent is valid and infringed.
ii) The 430 Patent is obvious in the light of ADSL2/02.
iii) If the 430 Patent had been valid, it would have been infringed.
Annex 1
Standards of relevance to the 268 Patent and the 430 Patent
|
Official Name |
Responsible Organisation / Committee |
Date |
Colloquial Name |
|
ANSI T1.413 Issue 1 |
ANSI T1E1.4 |
1995 |
T1.413 Issue 1 or T1.413i1 or G.DMT |
|
ANSI T1.413 Issue 2 – "Letter Ballot" Version |
ANSI T1E1.4 |
5 June 1998 |
T1.413 Issue 2 "Letter Ballot" |
|
268 Patent – Priority Date: 26 June 1998 |
|
ANSI T1.413 Issue 2 |
ANSI T1E1.4 |
Nov 1998 |
T1.413 Issue 2 or T1.413 Issue 2 or G.DMT |
|
ITU-T G.992.1 |
ITU-T SG15/Q4 |
July 1999 |
ADSL1 or G.DMT |
|
ITU-T G.997.1 |
ITU-T SG15/Q4 |
July 1999 |
G.ploam or G.997.1/99 |
|
ITU-T G.992.2 |
ITU-T SG15/Q4 |
July 1999 |
G.lite |
|
ITU-T G.992.3 |
ITU-T SG15/Q4 |
July 2002 |
ADSL2/02 |
|
ITU-T G.997.1 |
ITU-T SG15/Q4 |
May 2003 |
G.ploam or G.997.1/03 |
|
ITU-T G.992.5 |
ITU-T SG15/Q4 |
May 2003 |
ADSL2+ |
|
ITU-T G.997.1 Amendment 1 |
ITU-T SG15/Q4 |
December 2003 |
G997.1/03 Amendment 1 |
|
ITU-T G993.1 |
ITU-T SG15/Q4 |
June 2004 |
VDSL1 |
|
430 Patent – Priority Date: 25 September 2004 |
|
ITU-T G992.3 |
ITU-T SG15/Q4 |
Jan 2005 |
ADSL2/05 |
|
ITU-T G997.1 (2003) Amendment 2 |
ITU-T SG15/Q4 |
Jan 2005 |
G997.1/03 Amendment 2 |
ITU-T G.993.2 |
ITU-T SG15/Q4 |
Feb 2006 |
VDSL2/06 |
|
ITU-T G.993.5 |
ITU-T SG15/Q4 |
April 2010 |
Vectored VDSL2 |
|
ITU-T G992.5 |
ITU-T SG15 Q4 |
Jan 2009 |
ADSL2+/09 |
|
ITU-T G992.3 |
ITU-T SG15/Q4 |
April 2009 |
ADSL2/09 |
|
ITU-T G.9701 |
ITU-T SG15/Q4 |
Dec 2014 |
G.fast |
|
ITU-T G993.2 |
ITU-T SG15/Q4 |
Jan 2015 |
VDSL2/15 |
|
ITU-T G997.1 |
ITU-T SG15/Q4 |
Nov 2016 |
G.ploam or G997.1/16 |












![]()
![]() Table A: Exemplary contents and positions of sync byte within a superframe without
Table A: Exemplary contents and positions of sync byte within a superframe without 